- More than 60%of breaches involve some form of hackingVerizon, Data Breach Investigations Report, 2022
- It takes 277 daysto identify and contain security threatsPonemon Institute, Cost of Data Breach Report, 2022
- 80% of data breachestarget data for financial gainVerizon, Data Breach Investigations Report, 2022
Simplify endpoint security with Acronis to unlock unmatched business continuity
While the complexity and frequency of cybersecurity threats continues to rise, service providers and businesses are left counting on multiple point security solutions for protection. Comprehensive protection of endpoint devices and data requires multiple integrations of advanced solutions that introduce high resource intensity, security silos, significant costs, long time to value, and staffing needs.
With Acronis, you can count on a single platform for holistic endpoint security and business continuity, aligned with established industry standards such as NIST — enabling you to:
Identify
Identify vulnerable assets and data you need to protect across multiple endpoints.Protect
Proactively protect IT assets, endpoint devices and data with integrated backup and endpoint security configuration management capabilities.Detect
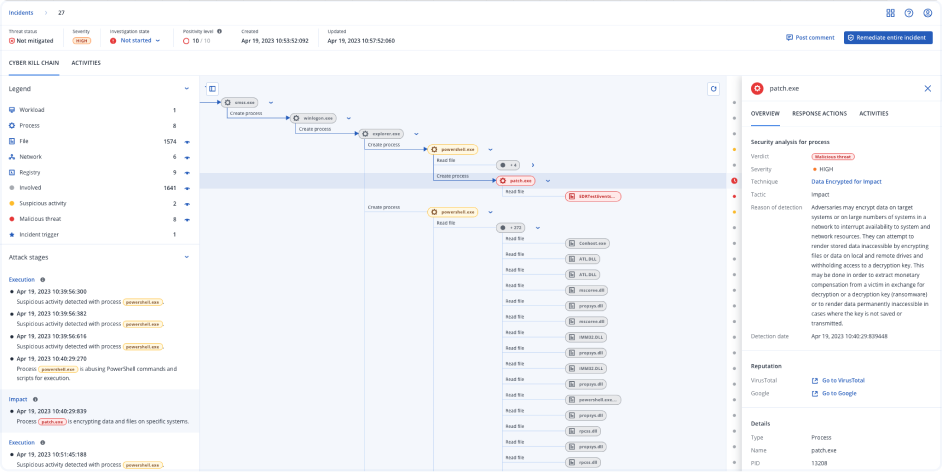
Continuous monitoring with AI/ML-based threat detection and behavioral analysis to guard against advanced threats and data exfiltrationRespond
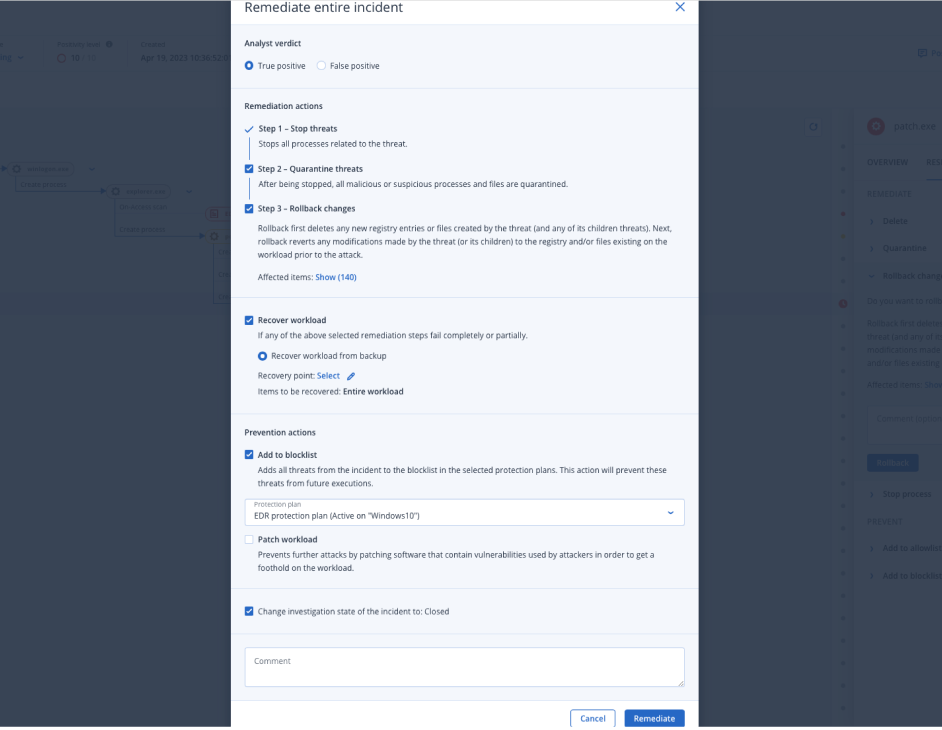
Leverage incident prioritization with a single-click to investigate, contain cybersecurity threats, remediate, rollback attacks, recover, and close vulnerability gapsRecover
Deliver unmatched data protection and business continuity with no data loss across all your endpoint devices, including mobile devices
Acronis MDR is a simplified, fully outsourced EDR service, built for MSPs and delivered via a platform that amplifies security effectiveness with minimal resource investment.
Acronis holistic endpoint protection enables you to protect business assets against a plethora of modern threats and attacks. Learn more about the most common current threats and how Acronis is able help you to stop them in their tracks:
Leverage the Acronis MSP’s guide to EDR to understand how to launch and scale your EDR practice with ease.
Don’t just stop threats. Ensure data protection and business continuity
The problem with single-focus endpoint protection platforms is that even if you stop the threat, addressing its impact is whole another story. The attacker might have already opened backdoors, exfiltrated data, and affected the business continuity.
With Acronis, you do not need additional integrations, manpower, and enterprise-level budget to provide security — not only to the endpoints, but also the data that security teams need to guard.
Integrated best-of-breed backup and recovery
Protect data with file- and image-level backups and integrated recovery as part of the single-click response to incidents. Unlock minimal recovery times and ensure no data loss, including with mobile endpoint devices.
Learn morePrevent leakage of sensitive data
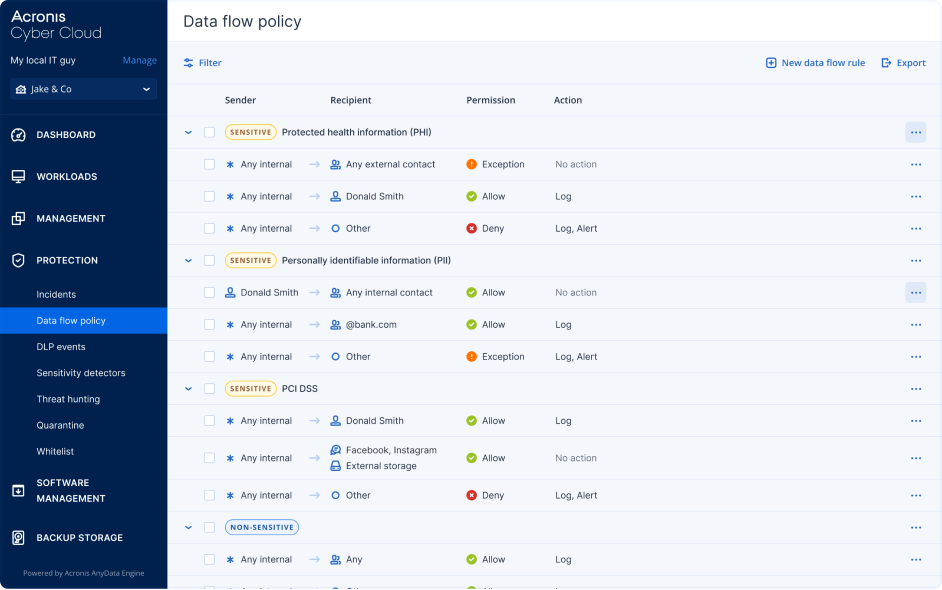
Leverage a behavioral-based data loss prevention (DLP) that automatically crates and continuously maintains business-specific policies to prevent sensitive data leaks across 70 channels.
Learn moreRollback endpoint attacks damage
Automatically roll back ransomware and leverage attack-specific rollbacks as response capabilities — leverage an endpoint protection solution designed to scale.
Learn moreEnsure unmatched business continuity
Leverage pre-integrated disaster recovery in our endpoint security software for an unmatched level of business continuity, and automatically switch to a backup environment in case of incidents.
Learn more
Powered by industry-recognized, award-winning endpoint protection











The value that Acronis endpoint protection brings partners:
Leverage the power of an integrated endpoint protection platform designed for MSPs to deliver holistic endpoint security, data protection and endpoint management service via a single agent.
Consolidation and service management centralization with Acronis is easier and more approachable than ever. Via single unified platform you can deliver a holistic endpoint protection aligned with industry-established frameworks like NIST. From identifying assets, proactively preventing and stopping threats, to responding to attacks and ensuring business continuity – we got you covered at every step.
See all features| Identify | • SW & HW inventory (Advanced Management) • Unprotected endpoint discovery • Data classification (Advanced DLP) |
| Protect | • Vulnerability assessments • Exploit prevention (Advanced Security / + EDR) • Device control • Security configuration management (Advanced Management) • Patch management (Advanced Management) • Data loss prevention (Advanced DLP) • Cyber scripting (Advanced Management) • Backup integration |
| Detect | • Emerging threats feed (Advanced Security / + EDR) • Search for IOCs of emerging threats (Advanced Security / + EDR) • AI/ML-based behavioral detection • Anti-malware & anti-ransomware • URL filtering (Advanced Security / + EDR) • Signature-based detection |
| Respond | • Rapid incident analysis (Advanced Security / + EDR) • Workload remediation with isolation (Advanced Security / + EDR) • Forensic backups (Advanced Security / + EDR) • Investigation via remote connection (Advanced Management) |
| Recover | • Rapid rollback of attacks (Advanced Security / + EDR) • One-click mass recovery • Self-recovery • Pre-integrated with disaster recovery (Advanced Disaster Recovery) |
Acronis #CyberFit partner program enables you to easily and efficiently launch and scale your practice with technical, sales, and marketing support and enablement.
Learn More, Earn More with Acronis Academy
Whether you and your team are seeking professional certifications or starting an MSP business, we're here to support you at every stage.

Start learning for Free
New! MSP Academy offers budding and seasoned MSP professionals vendor-neutral training covering the A-Z of managing a successful MSP business.
Train on-demand
Access our most popular sales and technical training courses designed for existing MSPs looking to enhance their cybersecurity skills and knowledge.
Login to Partner Portal
Available exclusively to Acronis Partners. Access our complete Acronis Academy training catalogue and earn your required certifications.
Looking for help?
Frequently Asked Questions
Why do businesses and service providers need endpoint protection?
With 80% of companies being attacked, based on the Acronis Cyberthreats Report 2021 — the need for effective endpoint protection platforms to secure businesses and their assets is clear.
Endpoint security protects against both common threats and advanced, targeted attacks by leveraging behavioral-based detection, commonly tied with signature-based detection engines that most antivirus solutions utilize. It’s important to note that antivirus software usually cannot bring an effective level of protection against modern threats that utilize more sophisticated techniques. Businesses usually require more advanced solutions like next-generation anti-malware (NGAV) capable of detecting modern threats and EDR capable of detecting and responding to in-progress attacks.
What’s the difference between antivirus software, NGAV, and EDR?
Antivirus, next-generation anti-malware (NGAV), and endpoint detection and response (EDR) can all be classified as endpoint protection software, but their capabilities and usage greatly differ.
Traditional antivirus software only provides an essential protection that is based on detecting common threats, and on cross-checking with a database of known malware variants and their signatures.
More advanced malware threats, like zero days, obfuscated and polymorphic malware will bypass antivirus defenses. However, these threats still exhibit known malicious behavior and can be detected with behavioral-based detection available in endpoint security software like next-generation anti-malware (NGAV).
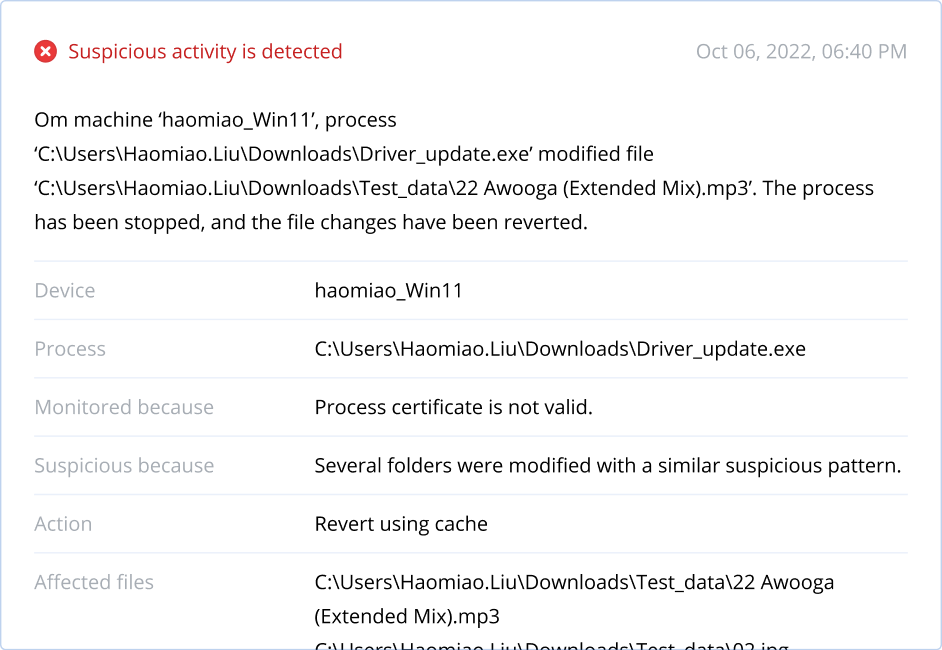
However, attacks and hacking attempts that are actually the source of a majority of breaches, usually use much more complex techniques, masking malicious processes as benign events, which security teams are blind to without deeper analysis and correlation of all events in the enterprise network. To detect and respond to such in-progress attacks, you require more advanced security solutions like Endpoint Detection and Response — capable of correlating events to understand whether the event chain suggests a security incident and providing the needed controls to analyze and remediate the attack. In the case of Acronis EDR capabilities, you can also recover from attacks — unlike traditional point security solutions with a siloed focus on stopping threats.
How is the Acronis endpoint protection solution deployed and managed?
Most endpoint protection systems have a siloed focus on threat remediation, requiring integration of additional endpoint solutions and agents for data protection, security configuration management, and other business needs that the service and client software need to cover.
Acronis empowers you with a centralized platform to, via a single agent, deploy, manage and scale multiple cyber protection services, including modular endpoint security, email security, security configuration management and data protection.
Specifically, for the data protection part — you can back up file-level and image-level data to a public cloud, a private, locally-hosted data center, or the Acronis Cloud, to ensure a safe recovery.
Additionally, you can outsource your endpoint protection services to Acronis MDR and unlock unmatched business continuity with optional resource allocation on your end.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.