Acronis SIEM Connector 1.0 has been superseded. We strongly recommend that you use Acronis SIEM connector 2.0.
For more information, see the SIEM Connector 2.0 documentation.
SentinelOne Singularity Data Lake
After configuring the Acronis Generic SIEM Connector, you need to follow a few more steps to view Acronis data in your SentinelOne Singularity Data Lake.
- Generate SentinelOne api_key to be used in the scalyr agent.json file.
- Download and install the scalyr agent on the syslog device where you want to collect the logs.
- Apply the following configuration to your agent.json file and replace the api_key with your own api_key.
-
Replace the path with the one that leads to your syslog directory and save the agent.json file.
- Restart the scalyr agent to ensure that your changes were implemented.
Copy
Configuration for the Scalyr Agent
// Configuration for the Scalyr Agent. For help:
//
// https://www.scalyr.com/help/scalyr-agent-2
{
// Enter a "Write Logs" api key for your account. These are available at https://www.scalyr.com/keys
"api_key": "...",
// Fields describing this server. These fields are attached to each log message, and
// can be used to filter data from a particular server or group of servers.
"server_attributes": {
// Fill in this field if you'd like to override the server's hostname.
// "serverHost": "REPLACE THIS",
// You can add whatever additional fields you'd like.
// "tier": "production"
},
// Log files to upload to Scalyr. You can use '*' wildcards here.
"logs": [
{
"path": "/var/log/syslog",
"attributes": { "parser": "systemLog" },
"formats": [
// Process name plus ID. Examples:
// 2013-03-19T12:25:16.267245+00:00 ip-10-11-222-111 auditd[14957]: Audit daemon rotating log files
// Feb 3 13:17:00 host-1 dhclient[1576]: DHCPREQUEST on eth0 to 169.108.1.0 port 67 (xid=0x323f0123)
{
"format": "$timestamp=timestamp$ $host$ $process$\\[$procid$\\]: $text$",
"halt": true
},
// Process name with no ID. Examples:
// Feb 3 03:47:01 host-1 rsyslogd: [origin software="rsyslogd" swVersion="5.8.03" x-pid="1631" x-info="http://www.rsyslog.com"] rsyslogd was HUPed
// Mar 17 04:34:12 li58-102 dhclient: DHCPREQUEST on eth0 to 206.192.11.29 port 67
{
"format": "$timestamp=timestamp$ $host$ $process$: $text$",
"halt": true
},
// CEF log format
{
"format": "$timestamp=timestamp$ $host$ $process$: $facility_version$ $cef_version$ $vendor$|$product$|$version$|$event_class_id$|$name$|$severity$|$extension$",
"halt": true
}
]
}
],
"monitors": [
]
}Acronis alerts look like this inside SentinelOne Singularity Data Lake:
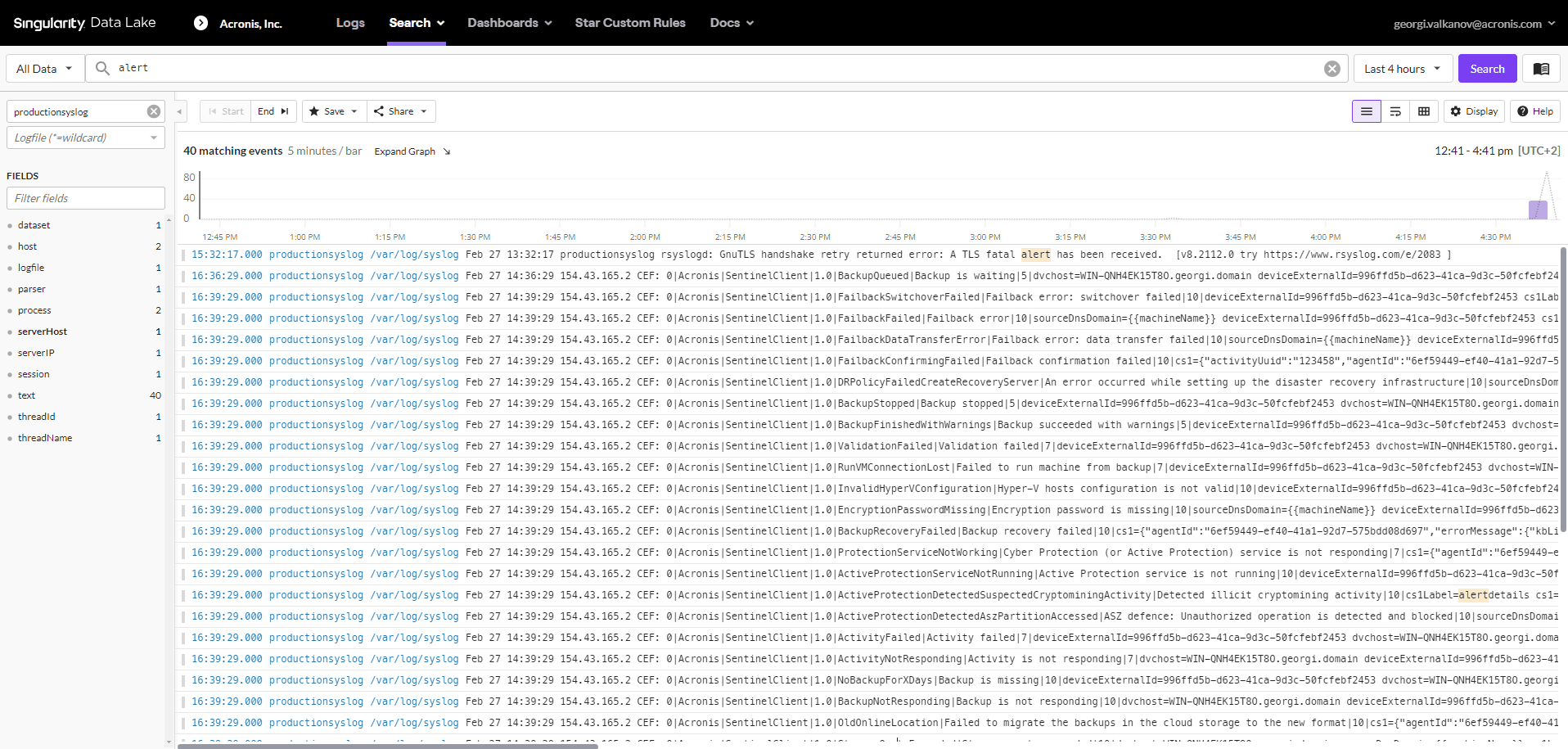
To view the Acronis alerts in a different format, switch to your preferred parser.