URL filtering
Malware is often distributed by malicious or infected sites and uses the so called Drive-by download method of infection.
The URL filtering functionality allows you to protect machines from threats like malware and phishing coming from the Internet. You can protect your organization by blocking user access to the websites that may have malicious content.
The URL filtering also allows you to control web usage to comply with the external regulations and internal company policies. You can configure access to the websites depending on the category they relate to. The URL filtering supports currently 44 website categories and allows to manage access to them.
Currently, the HTTP/HTTPS connections on Windows machines will be checked by the protection agent.
The URL filtering feature requires an internet connection to function.
In later protection agents, the compatibility issues are resolved so URL filtering is always enabled according to the policy.
How it works
A user enters a URL link in a browser. The Interceptor gets the link and sends in to the protection agent. The agent gets the URL, parses it, and then checks the verdict. The Interceptor redirects a user to the page with the message with available actions to manually proceed to the requested page.
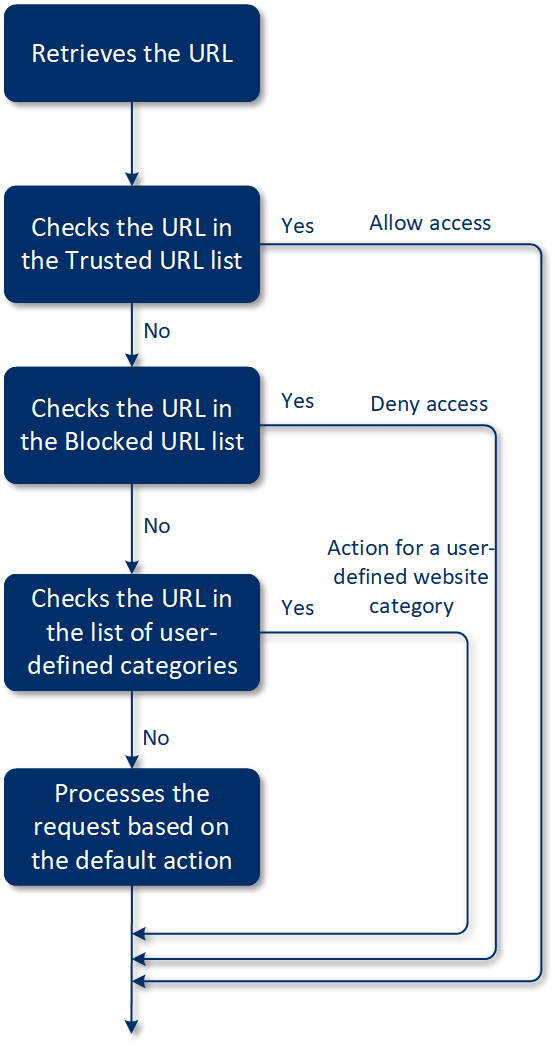
URL filtering configuration workflow
Generally, the URL filtering configuration consists of the following steps:
- You create a protection plan with the enabled URL filtering module.
- Specify the URL filtering settings (see below).
- Assign the protection plan to the machines.
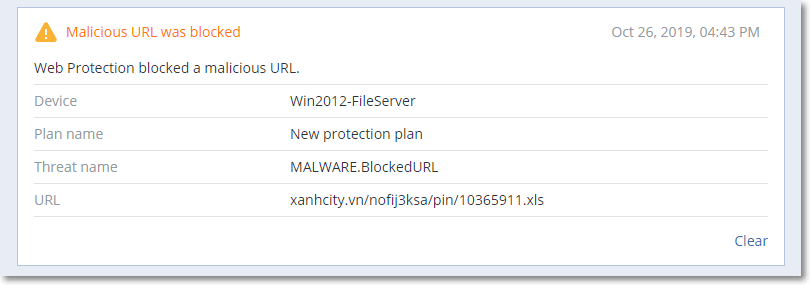
To check which URLs have been blocked, go to Monitoring> Alerts.
URL filtering settings
The following settings can be specified for the URL filtering module.
Malicious website access
Specify which action will be performed when a user opens a malicious website:
- Notify only—the software generates an alert about the process suspected of ransomware activity.
- Block —blocks the access to the malicious website. A user will not be able to access the website and a warning alert will be generated.
- Always ask user—asks the user whether to proceed to the website anyway or return back.
Categories to filter
There are 44 website categories for which you can configure access:
- Allow – allow access to websites related to the selected category.
- Deny – deny access to websites related to the selected category.
By default all categories are allowed.
Show all notifications for blocked URLs by categories – if enabled, you will get all notifications shown in the tray for blocked URLs by categories. If a website has several sub-domains, then the system also generates notifications for them, therefore the number of notifications may be big.
In the table below, you can find category descriptions:
| Website category | Description | |
|---|---|---|
| 1 |
Advertising |
This category covers domains whose main purpose is to serve advertisements. |
| 2 |
Message boards |
This category covers forums, discussion boards, and question-answer type websites. This category does not cover the specific sections on company websites where customers ask questions. |
| 3 |
Personal websites |
This category covers personal websites, as well as all types of blogs: individual, group, and even company ones. A blog is a journal published on the World Wide Web. It consists of entries (“posts”), typically displayed in reverse chronological order so that the most recent post appears first. |
| 4 |
Corporate/business websites |
This is a broad category that covers corporate websites that typically do not belong to any other category. |
| 5 |
Computer software |
This category covers websites offering computer software, typically either open-source, freeware, or shareware. It may also cover some online software stores. |
| 6 |
Medical drugs |
This category covers websites related to medicine/alcohol/cigars that have discussions on the use or selling of (legal) medical drugs or paraphernalia, alcohol, or tobacco products. Note that illegal drugs are covered in the Narcotics category. |
| 7 |
Education |
This category covers websites belonging to official educational institutions, including those that are outside of the .edu domain. It also includes educational websites, such as an encyclopedia. |
| 8 |
Entertainment |
This category covers websites that provide information related to artistic activities and museums, as well as websites that review or rate content such as movies, music, or art. |
| 9 |
File sharing |
This category covers file-sharing websites where a user can upload files and share them with others. It also covers torrent-sharing websites and torrent trackers. |
| 10 |
Finance |
This category covers websites belonging to all banks around the world that provide online access. Some credit unions and other financial institutions are covered as well. However, some local banks may be left uncovered. |
| 11 |
Gambling |
This category covers gambling websites. These are the “online casino” or “online lottery” type website, which typically requires payment before a user can gamble for money in online roulette, poker, blackjack, or similar games. Some of them are legitimate, meaning there is a chance to win; and some are fraudulent, meaning that there is no chance to win. It also detects “beating tips and cheats” websites that describe the ways to make money on gambling and online lottery websites. |
| 12 |
Games |
This category covers websites that provide online games, typically based on Adobe Flash or Java applets. It does not matter for detection whether the game is free or requires a subscription, however, casino-style websites are detected in the Gambling category. This category does not cover:
|
| 13 |
Government |
This category covers government websites, including government institutions, embassies, and office websites. |
| 14 |
Hacking |
This category covers websites that provide the hacking tools, articles, and discussion platforms for hackers. It also covers websites offering exploits for common platforms that facilitate Facebook or Gmail account hacking. |
| 15 |
Illegal activities |
This category is a broad category related to hate, violence and racism, and it is intended to block the following categories of websites:
|
| 16 |
Health and fitness |
This category covers websites associated with medical institutions, websites related to disease prevention and treatment, websites that offer information or products about weight loss, diets, steroids, anabolic or HGH products, as well as websites providing information on plastic surgery. |
| 17 |
Hobbies |
This category covers websites that present resources related to activities typically performed during an individual’s free time, such as collecting, arts and crafts, and cycling. |
| 18 |
Web hosting |
This category covers free and commercial website hosting services that allow private users and organizations to create and publish web pages. |
| 19 |
Illegal downloads |
This category covers websites related to software piracy, including:
Some of these websites may also be detected as pornography or alcohol/cigars, since they often use porn or alcohol advertisements to earn money. |
| 20 |
Instant messaging |
This category covers instant messaging and chat websites that allow users to chat in real-time. It will also detect yahoo.com and gmail.com since they both contain an embedded instant messenger service. |
| 21 |
Jobs/employment |
This category covers websites presenting job boards, job-related classified advertisements, and career opportunities, as well as aggregators of such services. It does not cover recruiting agencies or the “jobs” pages on regular company websites. |
| 22 |
Mature content |
This category covers the content that was labeled by a website creator as requiring a mature audience. It covers a wide range of websites from the Kama Sutra book and sex education websites, to hardcore pornography. |
| 23 |
Narcotics |
This category covers websites sharing information about recreational and illegal drugs. This category also covers websites covering development or growing drugs. |
| 24 |
News |
This category covers news websites that provide text and video news. It strives to cover both global and local news websites; however, some small local news websites may not be covered. |
| 25 |
Online dating |
This category covers online dating websites – paid and free - where users can search for other people by using some criteria. They may also post their profiles to let others search them. This category includes both free and paid online dating websites. Because most of the popular social networks can be used as online dating websites, some popular websites like Facebook are also detected in this category. We recommend that you use this category with the Social networks category. |
| 26 |
Online payments |
This category covers websites offering online payments or money transfers. It detects popular payment websites like PayPal or Moneybookers. It also heuristically detects the webpages on the regular websites that ask for the credit card information, allowing detection of hidden, unknown, or illegal online stores. |
| 27 |
Photo sharing |
This category covers photo-sharing websites whose primary purpose is to let users upload and share photos. |
| 28 |
Online stores |
This category covers known online stores. A website is considered an online store if it sells goods or services online. |
| 29 |
Pornography |
This category covers websites containing erotic content and pornography. It includes both paid and free websites. It covers websites that provide pictures, stories, and videos, and it will also detect pornographic content on mixed-content websites. |
| 30 |
Portals |
This category covers websites that aggregate information from multiple sources and various domains, and that usually offer features such as search engines, e-mail, news, and entertainment information. |
| 31 |
Radio |
This category covers websites that offer Internet music streaming services, from online radio stations to websites that provide on-demand (free or paid) audio content. |
| 32 |
Religion |
This category covers websites promoting religion or a sect. It also covers the discussion forums related to one or multiple religions. |
| 33 |
Search engines |
This category covers search engine websites, such as Google, Yahoo, and Bing. |
| 34 |
Social networks |
This category covers social network websites. This includes MySpace.com, Facebook.com, Bebo.com, etc. However, specialized social networks, like YouTube.com, will be listed in the Video/Photo category. |
| 35 |
Sport |
This category covers websites that offer sports information, news, and tutorials. |
| 36 |
Suicide |
This category covers websites promoting, offering, or advocating suicide. It does not cover suicide prevention clinics. |
| 37 |
Tabloids |
This category is mainly designed for soft pornography and celebrity gossip websites. A lot of the tabloid-style news websites may have subcategories listed here. Detection for this category is also based on heuristics. |
| 38 |
Waste of time |
This category covers websites where individuals tend to spend a lot of time. This can include websites from other categories such as social networks or entertainment. |
| 39 |
Traveling |
This category covers websites that present travel offers and travel equipment, as well as travel destination reviews and ratings. |
| 40 |
Videos |
This category covers websites that host various videos or photos, either uploaded by users or provided by various content providers. This includes websites like YouTube, Metacafe, Google Video, and photo websites like Picasa or Flickr. It will also detect videos embedded in other websites or blogs. |
| 41 |
Violent cartoons |
This category covers websites discussing, sharing, and offering violent cartoons or manga that may be inappropriate for minors due to violence, explicit language, or sexual content. This category doesn't cover the websites that offer mainstream cartoons such as “Tom and Jerry”. |
| 42 |
Weapons |
This category covers websites offering weapons for sale or exchange, manufacture, or usage. It also covers the hunting resources and the usage of air and BB guns, as well as melee weapons. |
| 43 |
|
This category covers websites that provide email functionality as a web application. |
| 44 |
Web proxy |
This category covers websites that provide web proxy services. This is a “browser inside a browser” type website when a user opens a web page, enters the requested URL into a form, and clicks “Submit”. The web proxy site downloads the actual page and shows it inside the user browser. These are the following reasons this type is detected (and might need to be blocked):
Since the SDK analyzes the HTML page (if provided), and not just URLs, for some categories the SDK will still be able to detect the content. Other reasons, however, cannot be avoided just by using the SDK. |
URL exclusions
URLs that are known as safe can be added to the list of the trusted domain. URLs that represent a threat can be added to the list of the blocked domain.
To specify the URLs that will always be trusted or blocked
- In the URL filtering module of a protection plan, click URL exclusions.
The URL exclusions window opens.
The following options are displayed:
Trusted items—Click Add to select from the available options:
-
Domain—When you select this option, the Add domain window opens.
- In the Domain field, enter each domain on a new line. In the Description field, enter a short description so that you can recognize your change in the list of trusted items.
-
Process—When you select this option, the Add process window is displayed.
- In the Process field, enter the path for each process on a new line. In the Description section, enter a short description so that you can recognize your change in the list of trusted items.
Blocked items—Click Add. The Add domain window is displayed.
In the Domain field, enter each domain on a new line. In the Description field, enter a short description so that you can recognize your change in the list of blocked items.
Description
You can use the Description field to make notes on the exclusions that you added in the URL exclusions list. Some suggestions on the notes you may make:
-
Reasons and purposes for the exclusion.
-
Time stamps.
If there are multiple items added in a single entry, there can only be 1 comment captured for the multiple items.