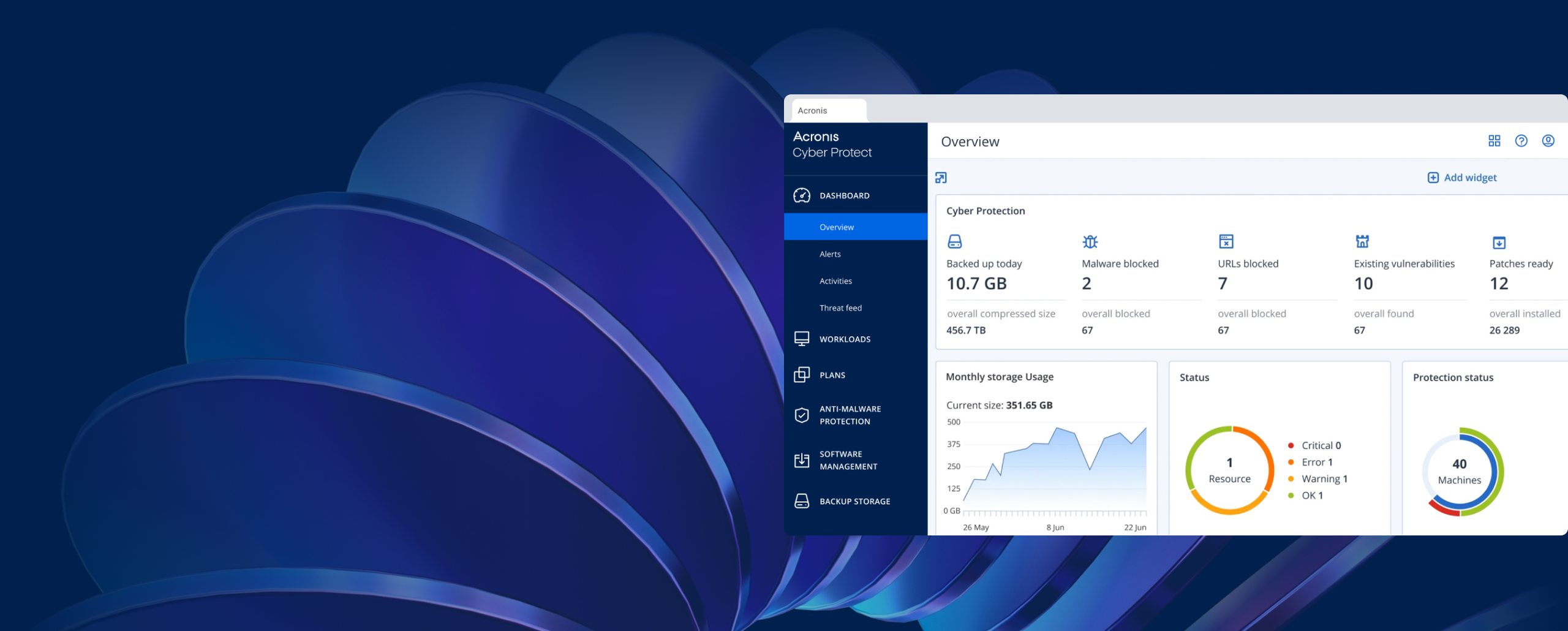
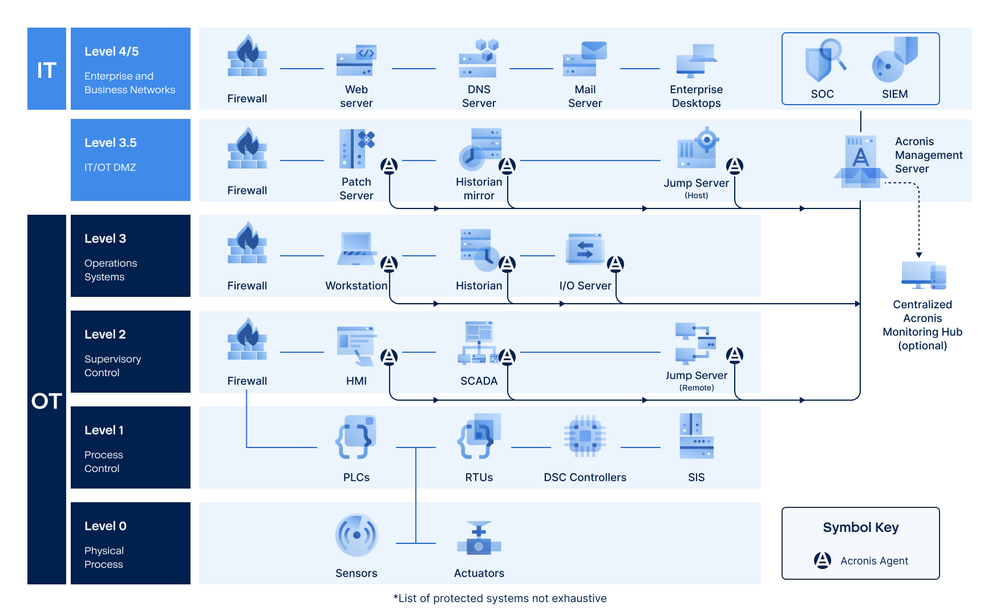
Acronis Cyber Protect provides backup and recovery for OT systems running on Windows or Linux. For example, this includes OT systems operating in Zones 2, 3 and 3.5 of the Purdue Model, including, but not limited to Zone 2 Supervisory Control Systems like HMI, SCADA and Jump Servers, Zone 3 Operations Systems like Historians and I/O Servers, and Zone 3.5 (OT / IT DMZ) Systems like Patch Servers and Historian Mirrors. Acronis Cyber Protect is also commonly used to protect non-OT systems operating in Zone 4, Enterprise and Business Network Systems, including an extremely broad range of hardware platforms, virtual machines, cloud workloads, operating systems and applications.