Authors:
Ilia Dafchev, Security Researcher
Robert Neumann, Head, Acronis Cyber Protection Operations Center
Introduction
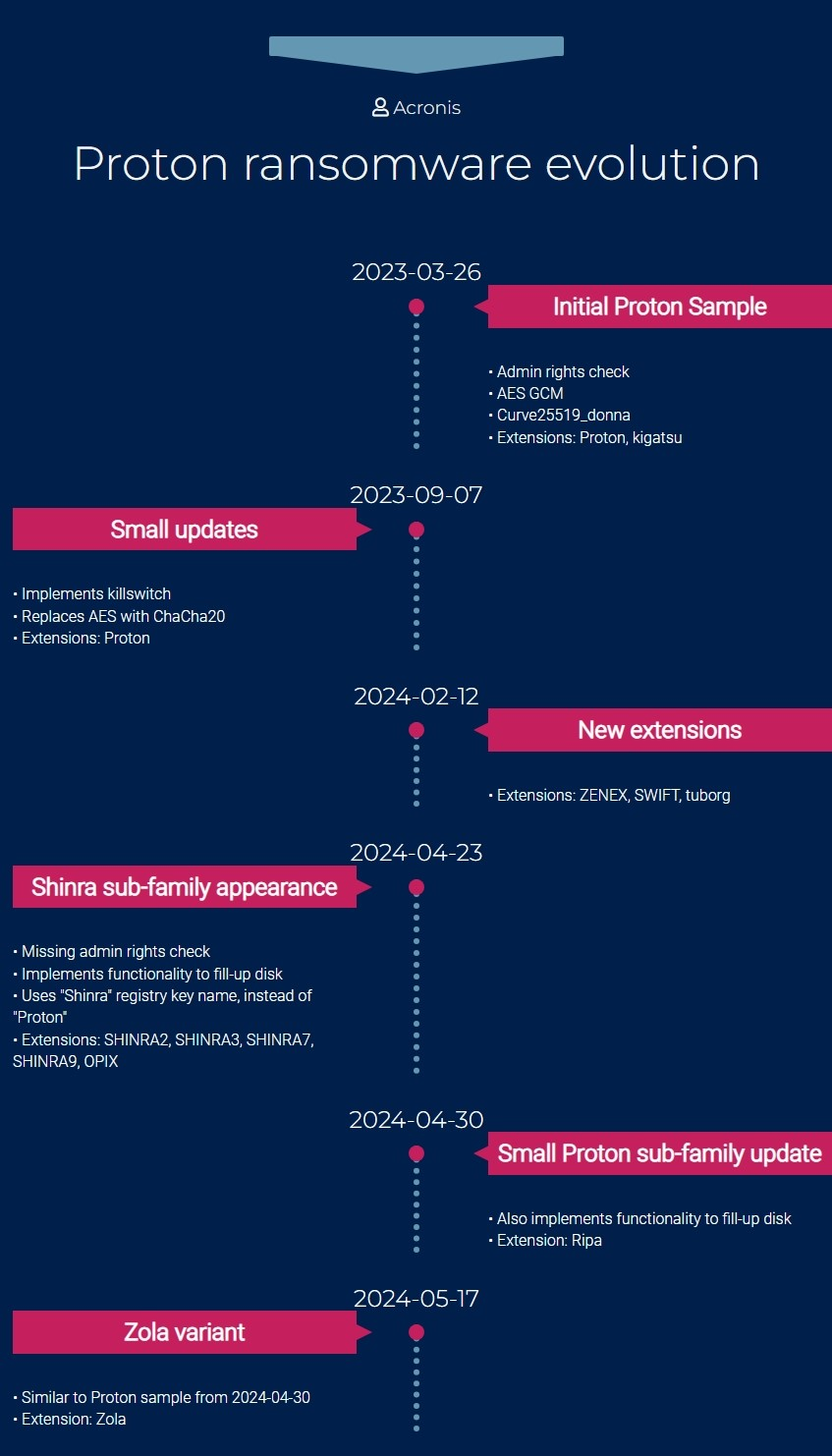
The appearance of new ransomware families every month has become an unfortunate norm in recent years. While some will appear as quickly as they fade out of existence, some establish an extended stay, and others simply change their virtual clothes. We recently came across an example of the latter — calling itself Zola. On the surface, it appeared new, but after a thorough investigation, Zola turned out to be just another rebrand of the Proton family, which first appeared in March 2023.
The Proton strain already had its fair share of members, and as such, we investigated how they relate to each other with the newest addition of the family. Let’s take a look at the key capabilities of Proton’s youngest sibling, Zola.
Technical analysis
Tactics, techniques and procedures (TTPs)
While observing the attackers’ activity, we successfully identified some popular hacking and power-user tools being deployed at the same location on multiple PCs within the same network. The attackers’ toolset did not make a lasting impression, it featured more of the same tools that casual ransomware groups have been using in recent years for the purpose of escalating privileges, scanning networks and stealing authorization tokens from memory to gain necessary access rights prior to deploying the ransomware payload. Sometimes, the threat actors stick to much-older versions of these tools, even if newer ones already exist — for example, to disable Windows Defender, nothing recent or sophisticated is needed.
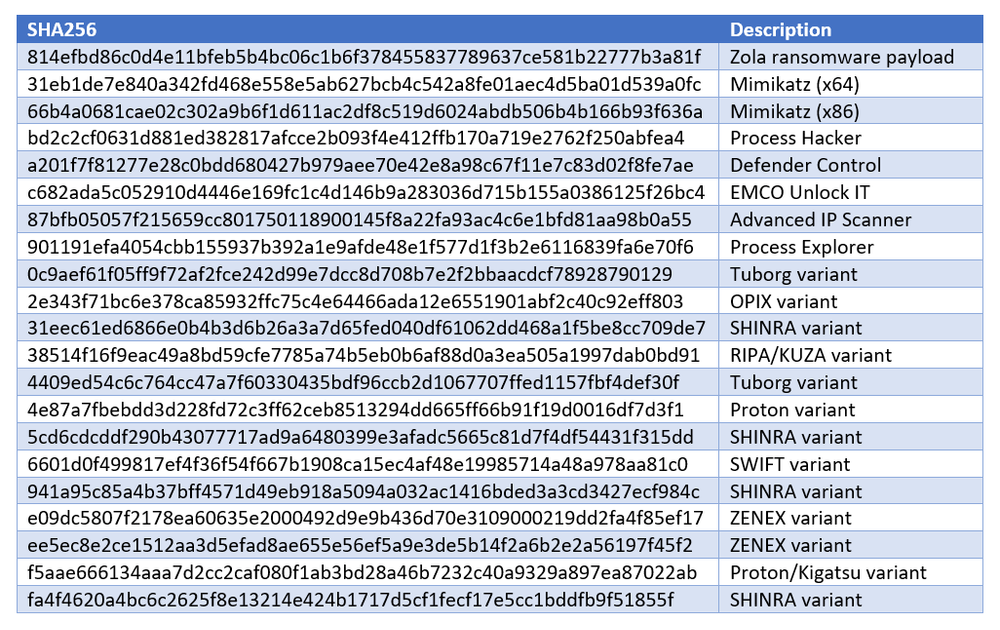
During our investigation, we observed the attackers using the following tools:
- Mimikatz 2.2.0
- ProcessHacker 2.39
- Sysinternals Process Explorer 16.42
- Advanced IP Scanner 2.5.3850
- EMCO Unlock IT 7.0.1
- Multiple tools for disabling Windows Defender
The tools were commonly dropped under the “Downloads,” “Music” or “3D Objects” directories of the current user.
The ransomware payload
We recovered the main Zola executable during an incident response session; it was close to 1 MB in size, developed in C++ and compiled on May 17, 2024. Upon execution, a new mutex "4B991369-7C7C-47AA-A81E-EF6ED1F5E24C" was created to prevent concurrent execution. This is a distinctive feature of all existing members of the Proton family, and so far, the hardcoded mutex hasn’t changed since the first variant. Another commonality is the checking of administrative rights; execution would not be interrupted in the case of insufficient rights, but the ransomware would repeatedly prompt the user for re-execution with admin privileges. In case of Zola, these actions were preceded by a kill switch, and the process would be terminated if any keyboard layout was found using the Persian language. This kill switch might be indicative of the Proton family’s origins, but no further evidence was found to strengthen this assumption.
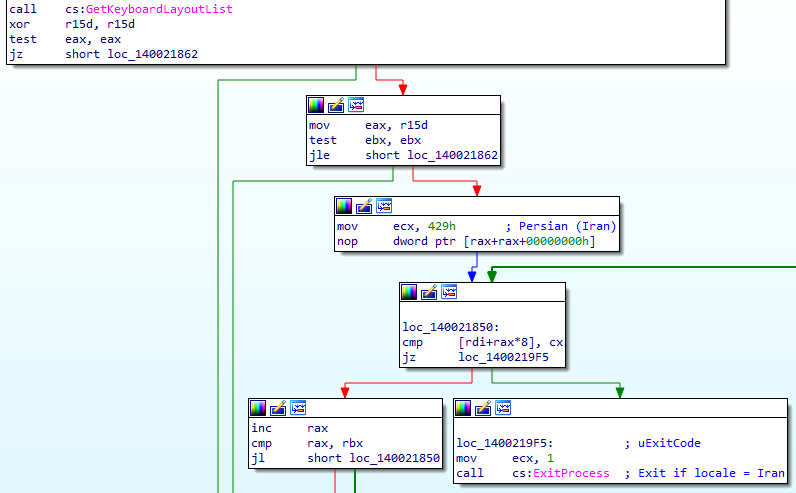
Prepare for surrender
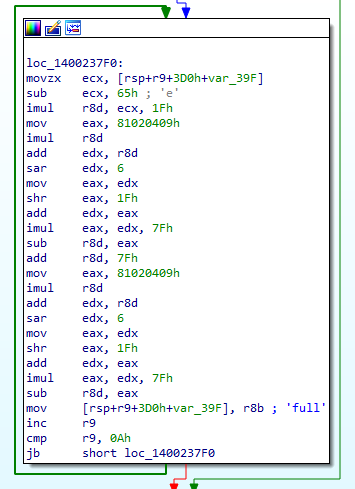
Once the initial steps with mutex creation, admin and kill switch operations were complete, there followed a set of actions aimed at preparing the PC for encryption. The first was the generation of a victim ID and key information that is later used in the encryption phase. Some of that information was saved under newly created registry values:
- HKCU\Software\Proton\public
- HKCU\Software\Proton\full
Note that these values were saved under HKCU\Software\Shinra for the Shinra variants. Additionally, later during execution, it also changed the wallpaper and set registry values like “legalnoticecaption,” which displayed a custom message during user login. Strings used for all operations were encrypted in the executable and were decrypted inline immediately before their use.
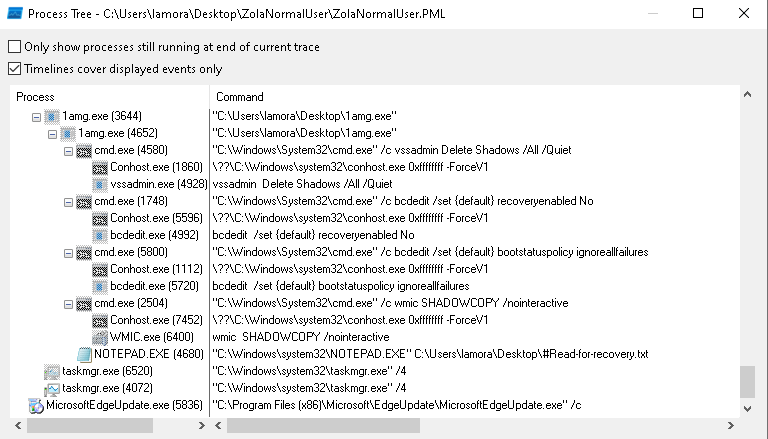
Execution then proceeded with emptying the Recycle Bin, making modifications to the boot configuration and deleting the shadow copies. Zola uses the vssadmin command to delete all available shadow copies on the system, which is done to hinder recovery. In addition, it also executed an invalid command: “wmic SHADOWCOPY /nointeractive”. The “SHADOWCOPY” argument was used to show the available shadow copies, but the switch “/nointeractive” was invalid and the command threw an error. In both cases, the ShellExecute API was used to execute the commands with the help of a command prompt:
- “cmd /c vssadmin Delete Shadows /All /Quiet”
- “cmd /c wmic SHADOWCOPY /nointeractive”
Once shadow copies were deleted, Zola executed additional commands with the help of the in-built BCDEdit Windows tool to modify the boot configuration of the system. The modifications disabled automatic repair during the boot process and forced Windows to ignore all failures and continue with the boot process:
- “cmd /c bcdedit /set {default} recoveryenabled No”
- “cmd /c bcdedit /set {default} bootsatuspolicy ingoreallfailures No”
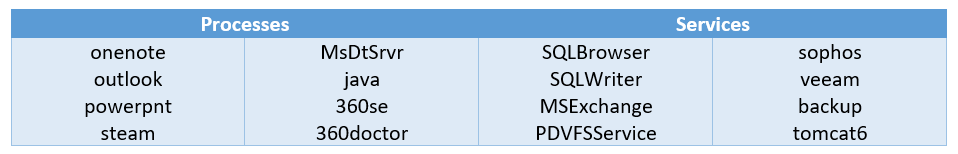
Right before reaching the encryption phase, Zola copied itself to the user’s Startup folder using the victim ID as the filename. The binary also contained an embedded list of 137 processes and 79 services, which it tried to kill prior to the encryption phase. Some of them belong to security software, while others are popular applications that could keep multiple files locked and as such prevent encryption. Some but not all are shown in the table below.
The encryption scheme
As soon as the preparation steps were completed, Zola started multiple threads for the encryption and another for dropping the ransom note under each folder. Network-attached drives with write access would also become part of the encryption process.
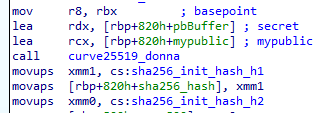
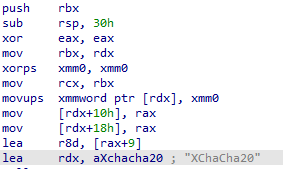
Early samples of Proton ransomware employed an especially fast elliptic curve implementation (curve25519) for key derivation and AES in GCM mode for the actual file encryption. Both algorithms were implemented with the help of the Crypto++ library, which especially provides cryptographic functions for C++ applications. The AES part was changed around September 2023 when the authors transitioned to using ChaCha20 for the encryption. This change was done only on the code level — the ransom note above still claims the use of AES and ECC algorithms.
While the encryption threads were running, the main thread continued its execution by generating a BMP image, which is saved at “C:\ProgramData\<ID>.bmp” and used as a desktop wallpaper.

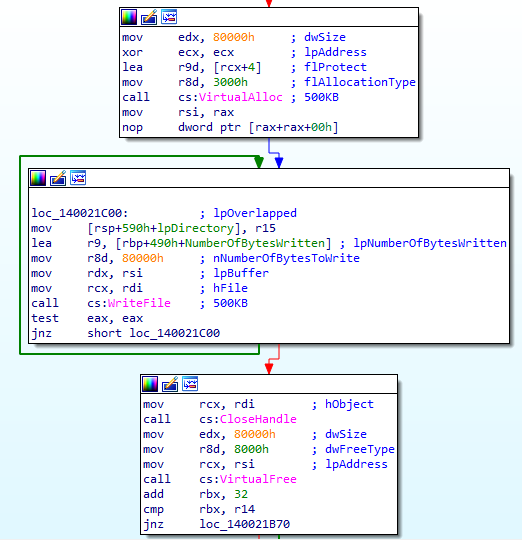
Since April 2024, all Proton-based families added an extra functionality, which, nearing the end of the execution, creates a temporary file under C:\ and writes uninitialized data in 500 KB chucks until the entire disk is full, after which the file is deleted. We suspect this might be an attempt to make digital forensics and data recovery harder by ensuring that any slack space on the disk will be overwritten.
Evolution and conclusion
Proton made its first appearance in March 2023. We have witnessed almost a dozen new variants since then, mostly rebranded versions of the original, optionally showcasing minimalistic changes to their codebase as we highlighted above. Both x86 and x64 variants appear from time to time, and their toolset also employs binaries for both platforms, which indicates that threat actors are also prepared and willing to attack older x86-based systems as well. As of today, Zola still features most of the original core functionality from its predecessor. Besides Proton’s continuous rebranding, we do not expect major changes in the future, either.
Protection statement
Acronis Active Protection, an advanced ransomware protection technology, protects against every known variant of the Proton ransomware strain, and Acronis real-time protection helps prevent the execution of the hacking tools used by the threat actors.
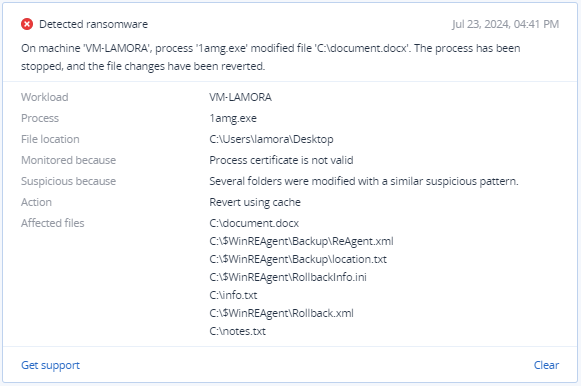
Indicators of compromise
Filename:
- 1amg.exe
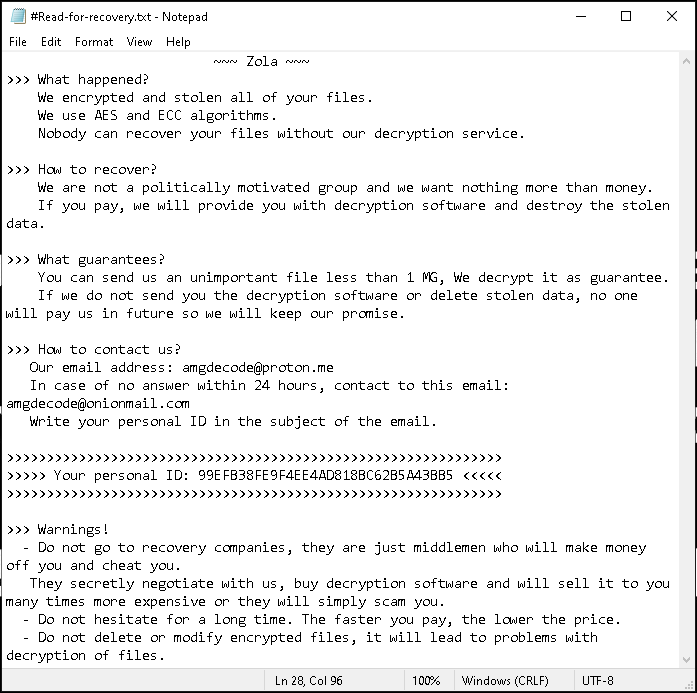
Ransom note emails:
- amgdecode[@]proton[.]me
- amgdecode[@]onionmail[.]com
Ransom note filename:
- #Read-for-recovery.txt
Extension:
- [<email>].Zola
Registry values created:
- HKCU\Software\Proton\public
- HKCU\Software\Proton\full
Registry values modified:
- HKCU\Control Panel\Desktop\Wallpaper
- HKCU\Control Panel\Desktop\WallpaperStyle
- HKCU\Control Panel\Desktop\TileWallpaper
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\OEMInformation\Manifucator
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\OEMInformation\SupportPhone
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\legalnoticecaption
- HKLM\SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System\legalnoticetext
Executed commands:
- cmd /c vssadmin Delete Shadows /All /Quiet
- cmd /c bcdedit /set {default} recoveryenabled No
- cmd /c bcdedit /set {default} bootsatuspolicy ingoreallfailures No
- cmd /c wmic SHADOWCOPY /nointeractive
Created files:
- C:\<random>.tmp
- C:\Users\<user>\AppData\Roaming\Microsoft\Windows\Start Menu\Programs\Startup\<ID>.exe
- C:\ProgramData\<ID>.bmp


