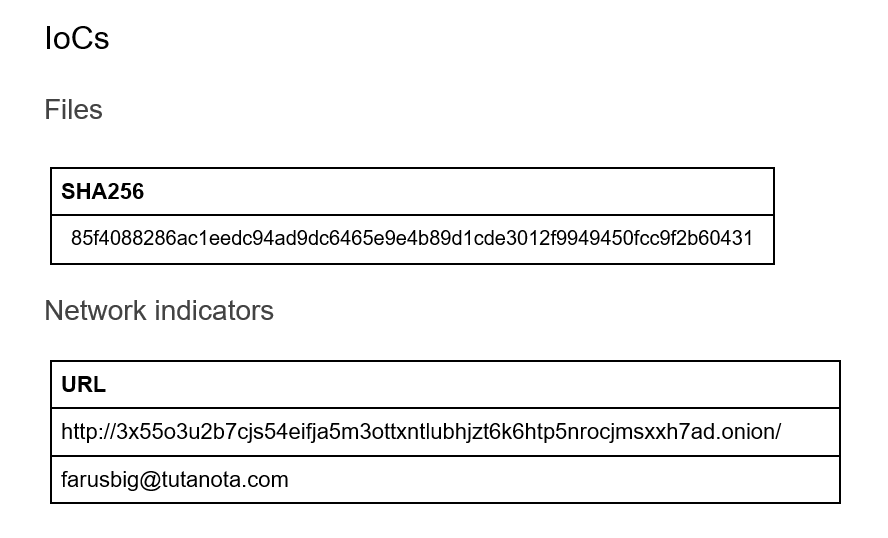
Summary
● PE32 file written in Borland Delphi.
● Designed as a console application, which supports a lot of arguments.
● Uses AES CBC to decrypt configuration.
● Uses AES OFB cipher to encrypt files.
● File names will be encrypted.
● Encrypted files will have ‘._locked’ extension.
Introduction
Trigona ransomware was first observed in June 2022. It has Windows and Linux versions, which are similar in their functionality. On underground forums, threat actors announced the start of the affiliate program, meaning that Trigona operates as ransomware as a service. It provides a builder for different configurations, an admin panel for Tor browsers and proofs about the impossibility of file decryption. In October 2023, the UAC (Ukrainian Cyber Alliance) hacked Trigona's data leak site and wiped all their data. Despite this, Trigona is still targeting different organizations, as evidenced by their other leak site, which is still updated with new victims, as well as new samples, which were made after UAC defaced their site.
Technical details
Overview
The Trigona ransomware sample is a PE32 file, written in Borland Delphi. It contains several resources, including package data, manifest, string tables and an unreadable string resource: ‘CFGS’.
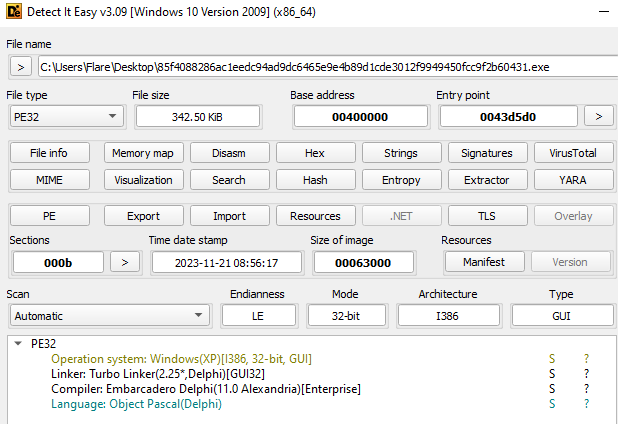
Execution
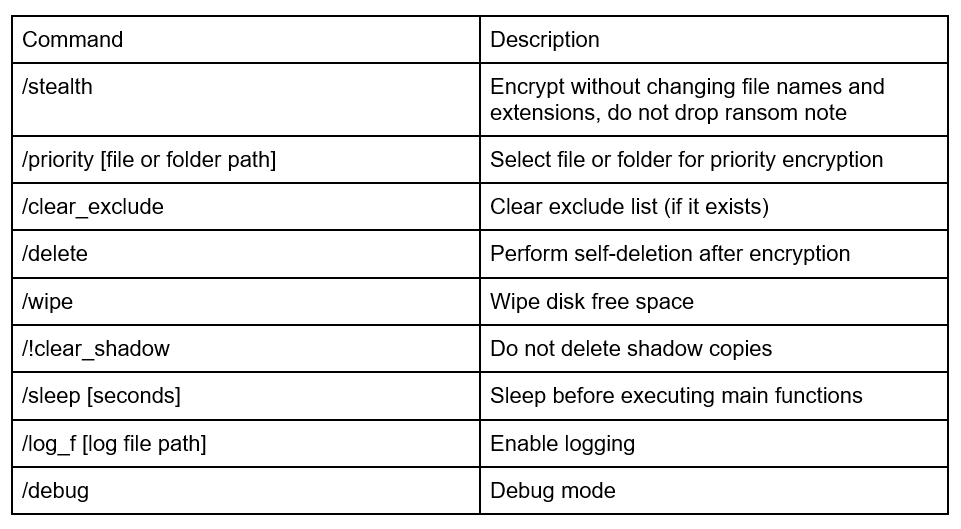
A Trigona sample contains a lot of commands, which can be passed to the command line.
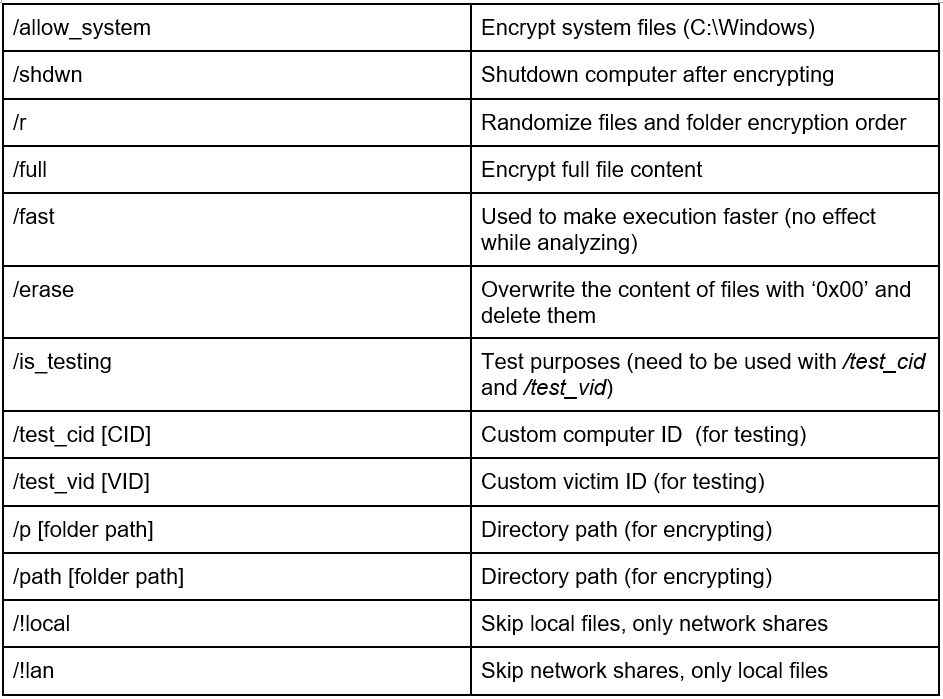
At the start of execution, Trigona loads the string resource “CFGS”. If this resource is missing, the malware attempts to load a ‘cfgs.txt’ file in the same folder as the executable.
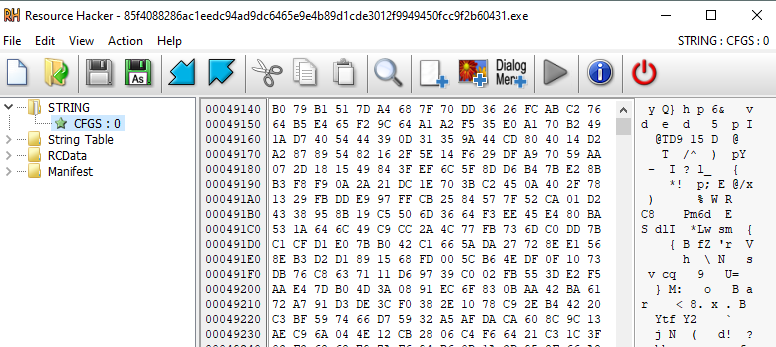
This resource is twice encrypted with an AES CBC cipher. After reading a resource to the memory, the malware takes its first 32 bytes as a key and the next 16 bytes as IV and performs a decryption. The second decryption takes the key and IV from the previous result.
This Rijndael AES algorithm was taken from the DCPcipher cryptographic component. It uses saved Rijndael substitution block(S-box) constants.
Those constants are used to initialize the key.
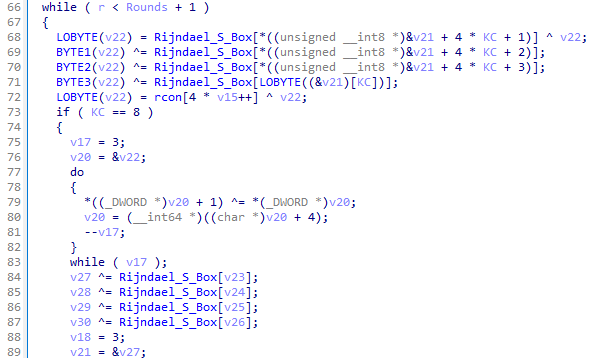
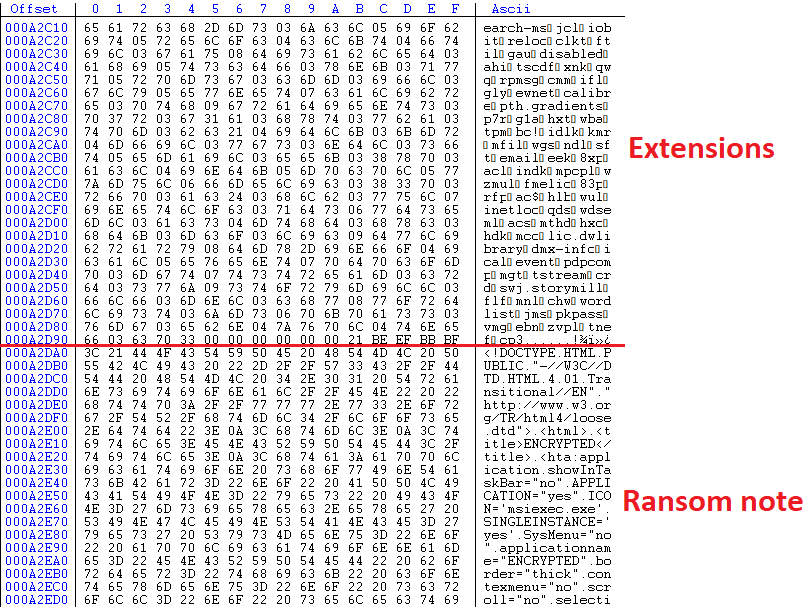
The decoded configuration then stored in the memory. It contains a ransom note HTML code template, data leak site link, threat actor email, victim ID and a large number of file extensions.
To identify victims, Trigona uses two unique parameters. The first one is VID – victim ID, which is saved in the sample configuration. For this sample, it is “EMPRESA”. The second one is CID (computer ID), which is generated during execution by obtaining information about the processor, operating system version and computer name.
The sample contains a saved list of possible Windows versions:

Then the sample uses IsWOW64Process to figure out system architecture. All gathered system information then passed to the MD5 hash function to generate VID.
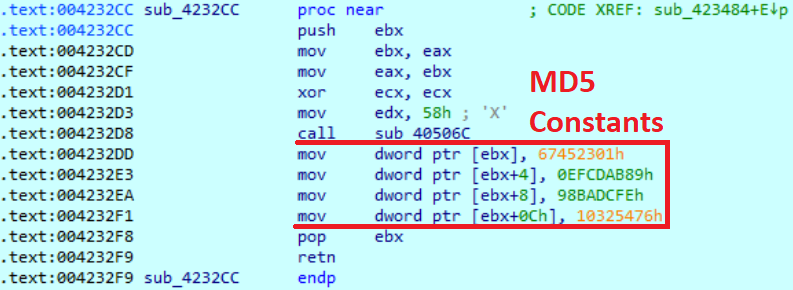
The example of generated VID: 8B7F6BA2-5D44-D267918C.
Then the sample makes a few changes to the Register. It sets a new key with a random name and its own path to provide an autostart to itself:
Computer\HKEY_CURRENT_USER\Software\Microsoft\Windows\CurrentVersion\Run
The sample also adds a key to exclude itself from the Background Activity Monitor scan:
Computer\HKEY_LOCAL_MACHINE\SYSTEM\CurrentControlSet\Services\bam\State\UserSettings\S-1-5-21-3461203602-4096304019-2269080069-1000
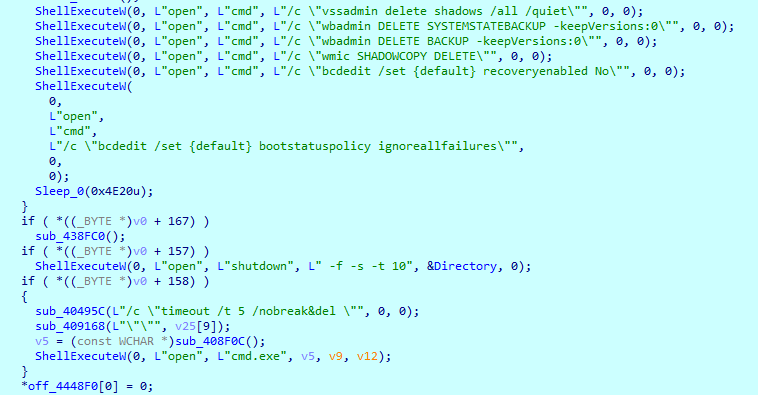
After the encryption process is finished, the sample executes some commands to disable recovery mode, change boot status policy and delete all shadow copies and backups using the “ShellExecuteW” function. If the ‘/!clear_shadow’ parameter was passed, the sample skips this section. Also, it can delete itself and shut down the machine.
Debug mode and log file
Starting a program with the ‘/debug’ parameter will enable console output using a lot of saved strings. This parameter cannot be used without the ‘/p [folder path]’ argument. At some point of execution, the sample asks to enter a command to proceed the execution. There are three possible commands here:
nonstop – continue execution in debug mode
kill – terminate process
!debug – stop debugging mode, continue execution
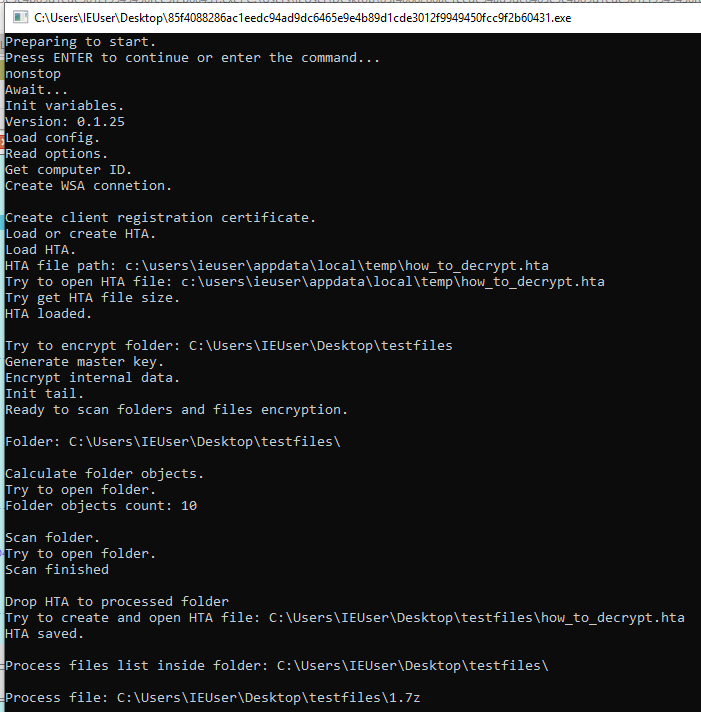
The same output will be saved to the log file, if the program was executed with ‘/log_f [log file path]’ argument.
File encryption
To encrypt file content, the sample uses AES Rijndael as for decrypting configuration, but in OFB mode. After creating encryption threads, it starts to search files to encrypt.
The searching process is dependent on the command line arguments. The default setting is to skip the ‘C:\Windows’ folder to avoid system workability disruption, but it can be changed with the ‘/allow_system’ command. If the ‘/priority [file/folder path]’ command was used, it first would encrypt pointed files or folders.
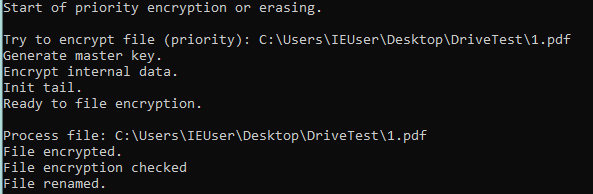
The sample starts searching all logical drives from “A” to “Z” and obtains information about them. Also, it checks for the presence of network shares, which can also be encrypted.
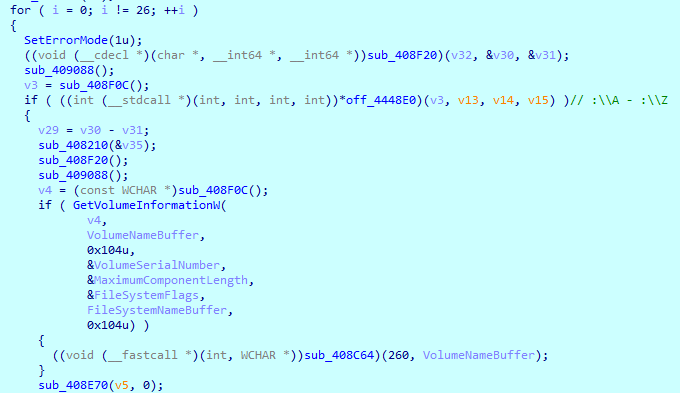
Then sample then starts searching for files to encrypt. Even though the configuration contains a lot of saved file extensions, it doesn’t use them. The excluded list is saved straight in the sample and contains only three file names:
'how_to_decrypt.txt'
'how_to_decrypt.HTA'
NTUSER.DAT
The AES in OFB mode implementation was also taken from the DCPcrypt library. The master key is generated pseudo randomly and is one for all files.
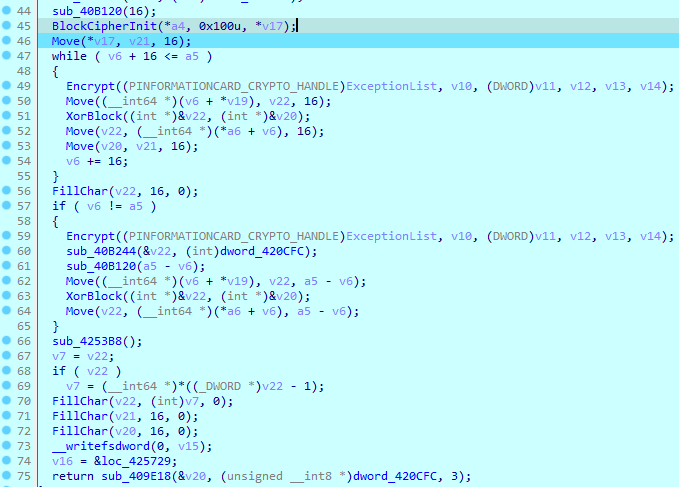
The “._locked” extension will be appended to each encrypted file. The file name will be encrypted with the same AES OFB cipher, sometimes appending to in the “availible_for_trial.” string. The files with this string can further be decrypted free as a part of test decryption.
By default, the sample encrypts the first 0x80000(524288 bytes) of the file, the other data will be saved.
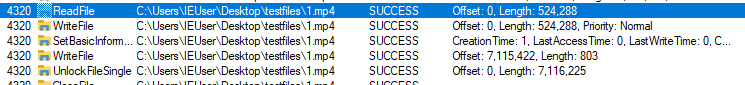
At the end of each encrypted file, it also writes 698 bytes of Trigona data, which is the same for all encrypted files. Also, it appends one more block with different size and content for each file.
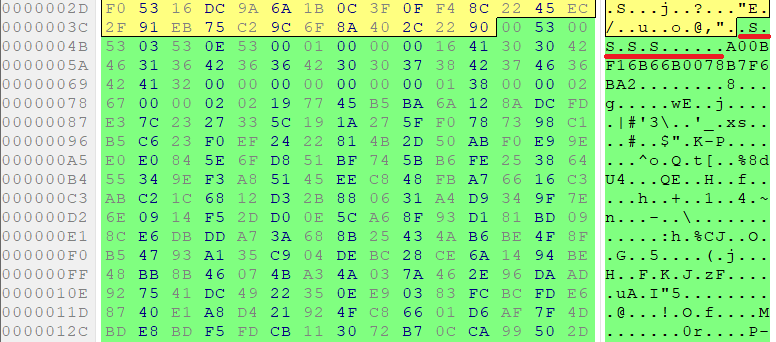
This data block starts with ‘S S S S’ string and contains a MD5 hash value of CID and VID, as well as other data, which was taken from configuration.
File eraser and free disk space wiper
The ‘/erase’ command will clear all file data. Similar to encryption, the first 524288 bytes of the file will be overwritten with ‘0x00’ bytes (full file overwriting available with ‘/full’ parameter). Then the file name will be overwritten with the random one and ‘.erased’ extension will be added. Finally, this file will be deleted. If the folder was passed as an argument, the sample will first delete all files, and then the folder will be deleted too.
The ‘/wipe’ command will wipe disk free space. The sample searches for logical drives similar to the encryption process and when the disk is found, it creates a ‘wipespace.sys’ file. Then it starts to write ‘0x00’ bytes to this file, 1048576 bytes per one write until the disk free space will end.
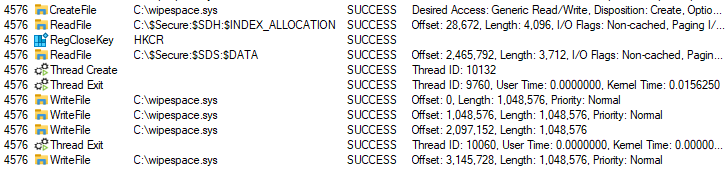
Ransom note
The ransom note ‘how_to_restore_files.hta’ is dropped in each encrypted folder and opened at the end of execution.
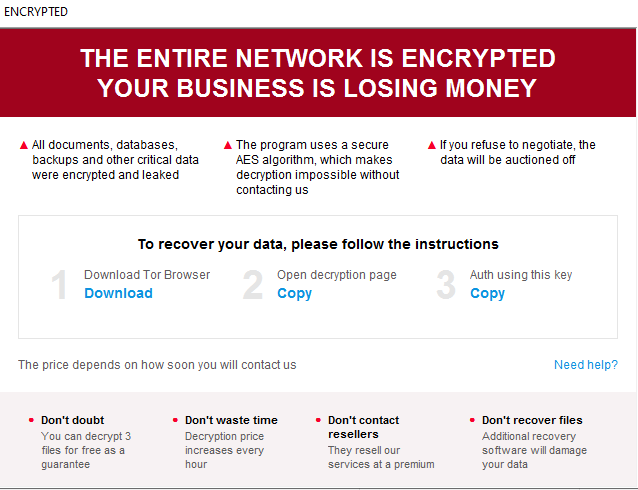
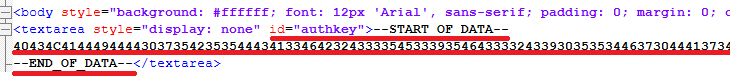
It contains a data leak site for Tor browser and an email to contact actors. At the time of analysis, the data leak site has already gone offline. Also, it has a CID, VID and authentication key.
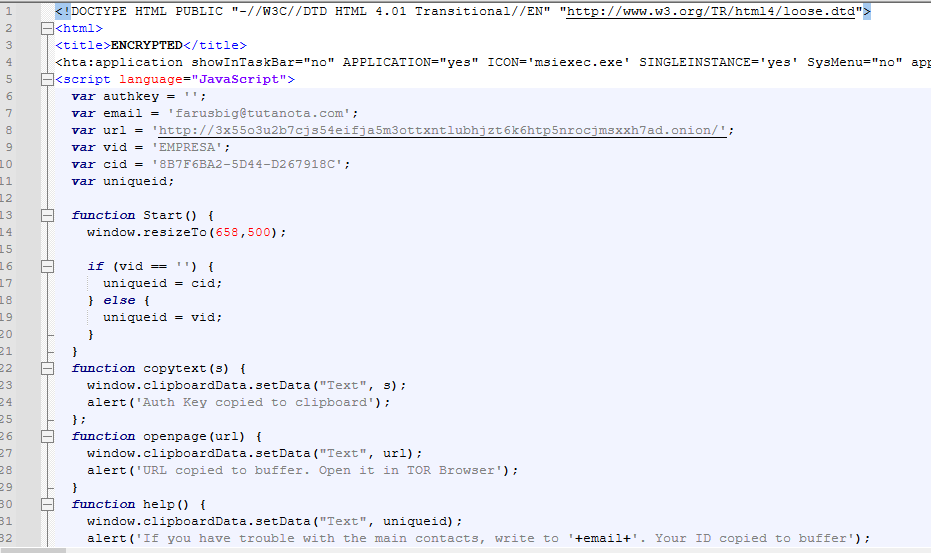
The authentication key has more than 3700 symbols, separated with “--START_OF_DATA--” AND “--END_OF_DATA--” strings:
Data leak site
While the link to the leak site from sample doesn’t work, there is one known that is still online.
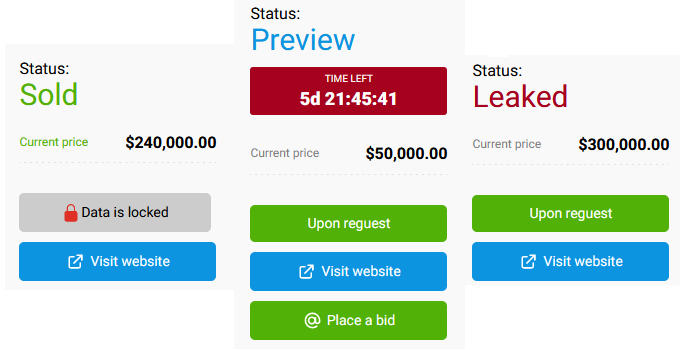
This is a ‘Blog’ site, which contains a list of victims.

All of those victims have a different status. The fresh ones have the status ‘Preview’ and contain a timer until the data is leaked. On the company page, there are some stolen documents to prove that the data is valid. The ‘Sold’ status means that the victim paid the ransom and the ‘Leaked’ status means that data has already been leaked.
Conclusion
Being not very active in the attacks, Trigona still continues its operation. Using a double extortion scheme, they demand a ransom to decrypt files and prevent stolen data from being leaked. The analyzed sample contains many different parameters for testing purposes. By default, the sample encrypts the first 0x800000(524288 bytes) of the file with AES Rijndael in OFB mode, the other data will be saved. The full file content can be encrypted only if using ‘/full’ parameter. Besides encryption, the sample can erase files content and delete them, as well as wiping free disk space. It stores encrypted configuration in the resources, which is different for all samples. At the end, it deletes shadow copies and backup files, which makes system recovery impossible.
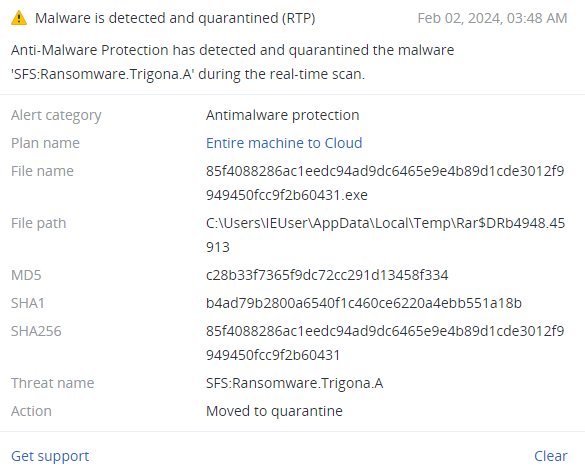
Detected by Acronis