The Nefilim ransomware group, known to be active since February 2020, adopts the Nemty ransomware code written in the Delphi programming language. It uses a Citrix vulnerability/RDP to access corporate networks. Nefilim started its own data leak site called ‘Corporate Leaks,’ where the operators publish exfiltrated data from compromised organizations if they refuse to pay.
Summary
- First seen in February 2020Uses AES-128-CTR and RSA-2048 encryption algorithms
- Distributed in many variants: Nephilim, OFFWHITE, SIGARETA, Telegram.
- Uses Citrix vulnerability/RDP to enter the victim machine
- Written in Borland Delphi
- Supposed to be a Nemty successor with simplified encryption
Distribution
Nefilim is most likely distributed through exposed Citrix virtual desktop interfaces (VDI) and Remote Desktop Services (RDP).
Obfuscation
Nefilim employs an obfuscation technique to hide imported functions. During the runtime linking, Nefilim enumerates the functions from shell32.dll and calculates hex representation of their names. If values are matched, the API is imported.
It converts the API name to hex format, then matches with the ones from the system DLL.
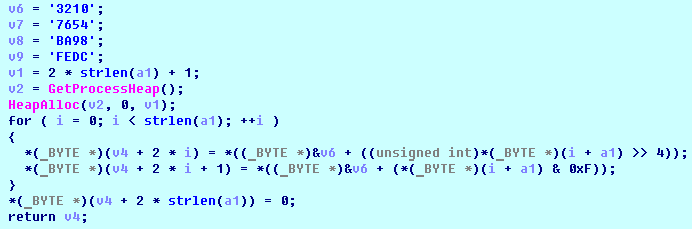
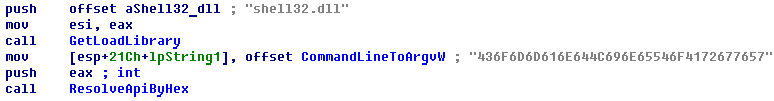
For example, to import the CommandLineToArgvW() function, it pushes ‘436F6D6D616E644C696E65546F4172677657’ to the stack to compare.
Encryption
First, the ransomware imports the RSA-2048 master public key, which is hardcoded in Base64 format.
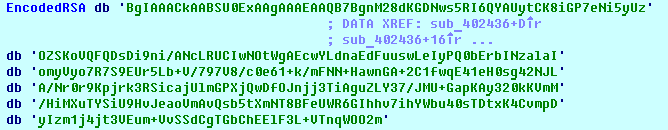
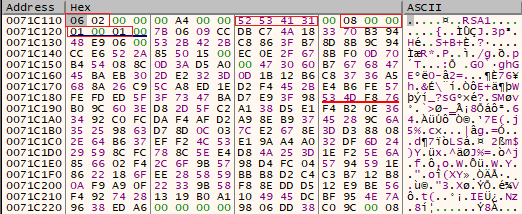
The key is decoded to BLOB format with the help of CryptStringToBinary() and the ‘CRYPT_STRING_BASE64’ flag:
Encryption is done in 26 threads to speed up the encryption process.
Nefilim generates 128-bit file keys using SystemFunction036() — a.k.a. RtlGenRandom() — from advapi32.dll for AES encryption.
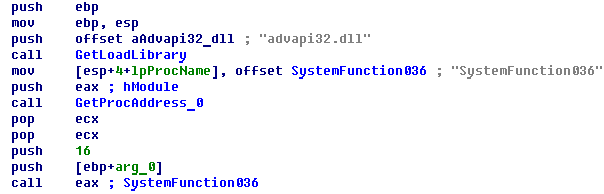
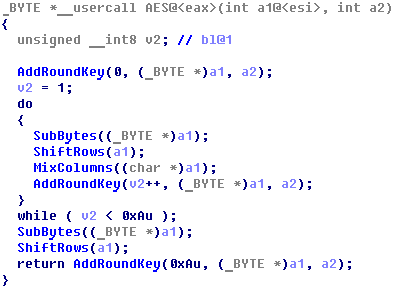
Nefilim uses the AES CTR mode that turns a block cipher into a stream cipher. It generates the next keystream by using the successive values of a counter, which is any numerical sequence that does not repeat for a long time (usually incrementing the value by one). CTR mode is well-suited to operate in a multithread mode where blocks can be encrypted in parallel.
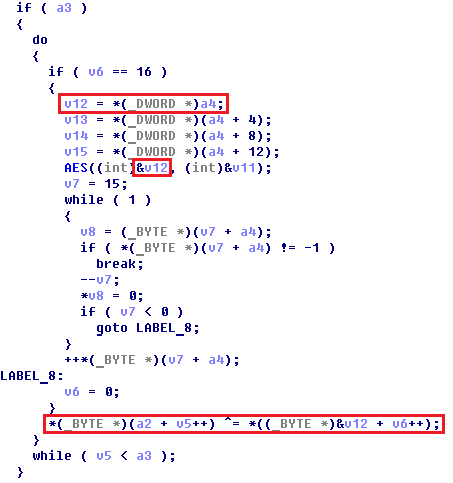
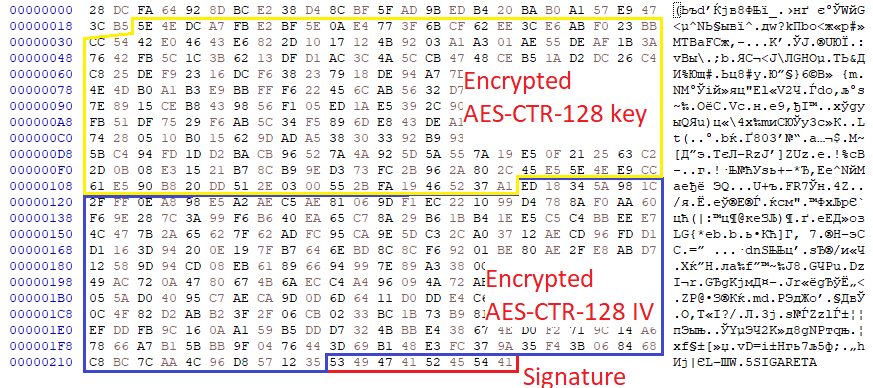
The encrypted files are appended with ‘SIGARETA’ (eng. ‘cigarette’) extension:

The footer of the encrypted file contains the file key and IV, encrypted by the RSA-2048 master public key and terminated with the signature ‘SIGARETA’.
During encryption, Nefilim avoids folders and files that have the following strings:
Nefilim additionally provides the command line arguments to encrypt a single file or disk.
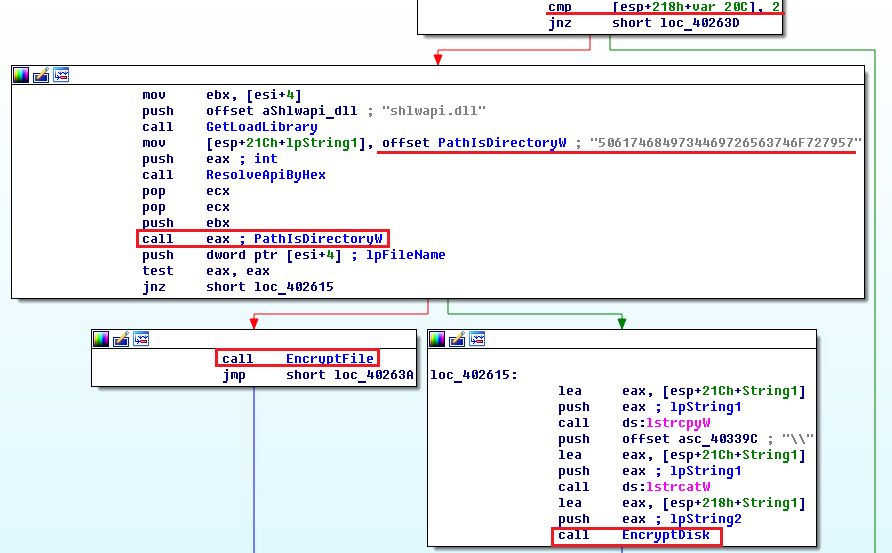
Easter eggs
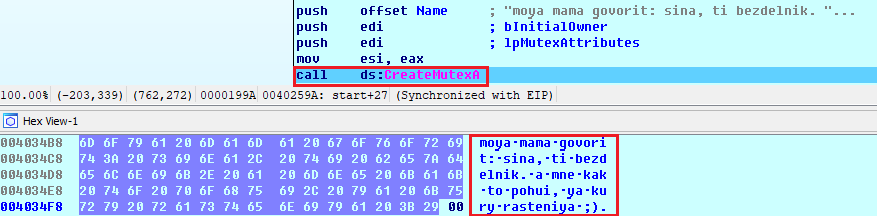
Nefilim ransomware contains funny names, mostly based on Russian people. The Mutex name is written in Russian, but uses the Latin alphabet rather than Cyrillic.
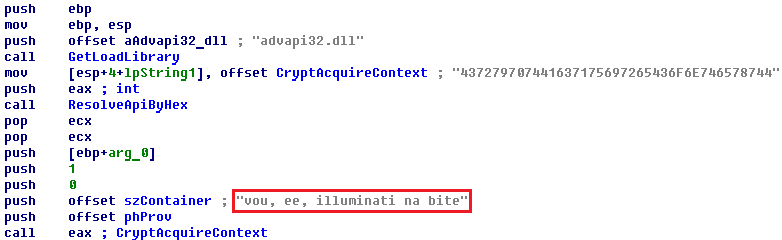
The name of the crypto container also looks weird.
The pdb file location contains the Russian words ‘pahan’ (‘father’) and ‘sigareta’ (‘a cigarette’).
Ransom note
The hardcoded ransom note is Base64-encoded and encrypted using AES-128-CTR with key ‘asdfasdffdasfdas’ and IV ‘fsdafadsfsadfads’:
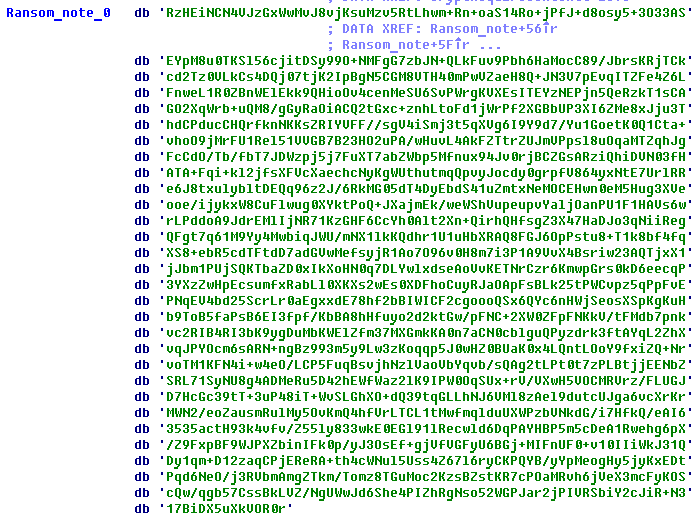
The ransom note is decrypted and stored in the root folder of the encrypted disks:
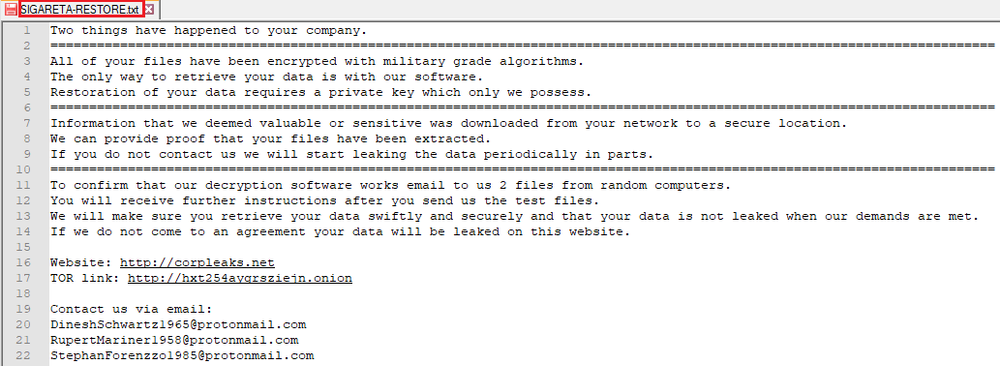
Once encryption is finished, Nefilim creates an image, putting the ransom note content in Yu Gothic Light font and setting it up as a wallpaper.
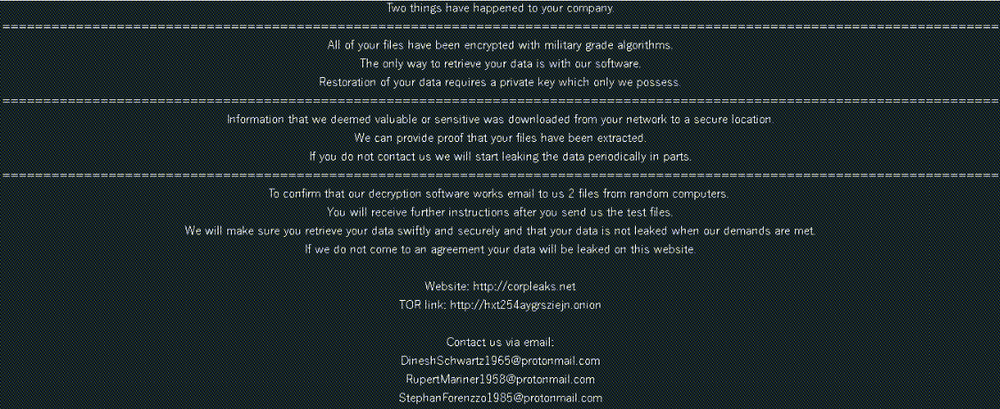
The image itself is stored in the %TEMP% folder and is called ‘virubim_eshky.jpg’.
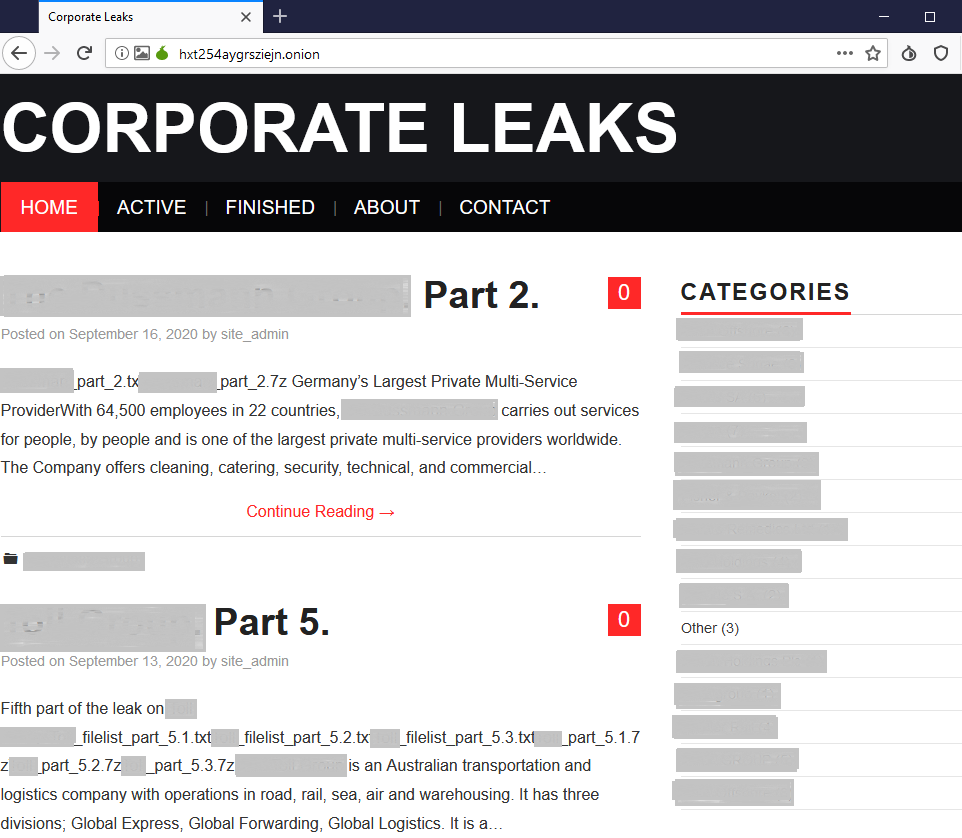
Decryption service
Decryption without paying a ransom is not possible. The ransom note contains the email addresses to contact the attackers. It also provides a link to a site on the Tor network where leaked data is published: http://hxt254aygrsziejn.onion. The site contains data stolen from 17 organizations.
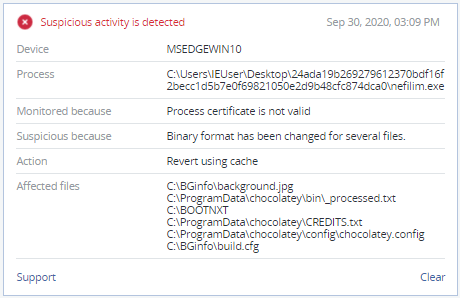
Detection by Acronis Cyber Protect
Nefilim ransomware is detected and blocked by Acronis cyber protection solutions.
Conclusion
Nefilim adopts the tactics and techniques of Nemti ransomware, including Object Pascal code (unusual for modern software). Based on strings found in the code, Nefilim was created by Russian programmers. Following the Maze cartel trend, the operators of Nefilim have their own data leak site where they have already reported 17 victims who didn’t pay the ransom.
IoCs
SHA256: 24ada19b269279612370bdf16f2becc1d5b7e0f69821050e2d9b48cfc874dca0
DineshSchwartz1965@protonmail.com
RupertMariner1958@protonmail.com
StephanForenzzo1985@protonmail.com
http://hxt254aygrsziejn.onion
http://corpleaks.net (not active now)
SIGARETA_RESTORE.TXT
.SIGARETA



