
Over the past eighteen years, Apple devices have taken the world by storm, revolutionizing how we interact with technology. From the iconic iPod to the sleek iPhone, the versatile iPad, and the powerful MacBook, Apple has woven itself into the fabric of our daily lives. Today, it’s hard to find a household without at least one Apple device. But with great innovation comes great responsibility—especially when it comes to security.
Apple products are known for their cutting-edge design and reliability; their built-in protection features are designed to stop most cyber threats, giving users a sense of safety. But here’s the catch: cybercriminals aren’t taking a break. In fact, they’re working harder than ever, crafting sophisticated and destructive attacks that can slip past even Apple’s security systems.
Hackers have found alarming success in targeting Apple devices. Why? Because many users assume their built-in security is enough and skip adding advanced third-party protection software. This false sense of security leaves the door wide open for cybercriminals to exploit software vulnerabilities, use social engineering tricks, and unleash malware infections. Their goals? To steal your bank details, encrypt your database through a ransomware attack, or quietly exfiltrate your sensitive data for personal profit.
The good news? There’s a way to fight back and protect your Mac from these relentless threats. In this article, we’ll dive into how you can protect your device from malware, reduce your risk of falling victim to hackers, and keep your digital life secure. Let’s get started!
Why Mac malware protection is more important than ever
Mac malware protection has never been more important because cybercriminals are now extremely focused on creating more destructive and harder-to-detect malware attacks, specifically targeting Mac devices. The 2024 ThreatDown State of Malware Report reveals a mind-blowing trend: malware attacks increased by 68% and 11% of all malware detections on macOS devices are zero-day attacks—unknown threats that easily bypass the built-in security systems entirely. This is not just a wake-up call; it’s a red alert.
Why should you care? Imagine becoming a victim of a ransomware attack, which locks your files and displays a message on your screen demanding payment to restore access to your database, or malware that steals your banking credentials and sensitive financial data silently.
Advanced threats go a step further by installing keyloggers that capture every keystroke, harvest passwords, and transform your Mac into a partial botnet for cryptocurrency mining, thereby draining your device's resources. How does this sound? Scary, right? The risks are real, and the consequences can be disastrous.
For businesses, the stakes are even higher. According to IBM’s 2024 Cost of a Data Breach Report, the average global cost of a data breach has soared to $4.88 million. This is not just about financial loss; it’s about operational disruptions, costly data recovery efforts, and irreparable reputational damage. For Mac users in business environments, the message is clear: complacency is not an option.
One thing is for sure: the myth of Mac’s impenetrable security is officially debunked in millions of pieces. Simply put, cybercriminals constantly look to exploit vulnerabilities in the users’ devices, which still believe their built-in security features make their Macs immune to malware infections.
This illusion confirms that advanced malware protection is not just an option but an essential component of your Mac's security. Whether you are an individual user or a business owner, taking timely actions to improve the security layer of the Mac devices you are using is not a necessity but a must.
How Mac malware scanners work
Mac malware scanners use advanced detection methods to protect your system from malicious software. The most effective programs combine multiple techniques to identify, isolate, and remove malware threats before they can harm your device through spreading across your files and apps. Let's now explore how they actually work.
Signature-based scanning
At its core, the anti-malware tools rely on signature-based scanning, which compares files against a database of known malware patterns. Think of these signatures as digital fingerprints—each type of malware has a unique code that identifies it. Premium tools maintain extensive, frequently updated databases to detect the latest threats, while free versions often have limited pattern recognition, leaving them less effective against newer malware.
Behavioral analysis
Beyond signature-based detection, malware scanners use behavioral analysis to identify suspicious activities. These tools monitor your system in real-time, looking for unusual behavior like unauthorized file modifications or encryption attempts. For example, if a program tries to encrypt your files without permission, the scanner blocks it immediately, thus protecting you from zero-day attacks.
Ransomware protection
Ransomware is a growing threat, and every reputable anti-malware software offers specialized protection against it. Using real-time monitoring, they detect and block encryption attempts or unauthorized system changes. This is especially valuable for businesses, as ransomware attacks can cripple operations and lead to significant financial losses.
Real-time and web protection
Real-time protection is responsible for constantly monitoring your web traffic and file downloads. When you visit a website or download a file, the scanner checks it for malware before it reaches your system.
Quarantine features
When the malware scanner detects suspicious files, it doesn’t always delete them immediately. Instead, it moves these potentially malicious files to a secure quarantine zone. This allows you to review them and decide whether they’re safe or should be removed. While false positives can occur, they’re rare compared to genuine threats.
Key features to look for in a Mac malware scanner
Imagine this: Someone you know, maybe a business owner or a friend, has experienced a destructive ransomware attack. It ends with a screen providing instructions to pay the ransom, most commonly with cryptocurrency, to restore access to their database. Your friend has found themselves in a delicate situation, choosing between paying the demanded ransom or losing their entire database for good.
Now, to ensure that this won't happen to you, you're searching for the best Mac anti-malware scanner to help you avoid becoming the next victim of cybercriminals. This task might not be as easy as you think because almost all third-party vendors promote their products as the most effective on the market. But you know they can't all be the best.
So, you now wonder how to choose the right malware scanner for your Mac device(s). Don't worry; we've got you covered by thoroughly exploring the essential features of a reliable solution. Let's not waste any more time and get to work to help find the solution that meets your requirements and budget!
Real-Time protection
A top-tier malware scanner for Apple computers must offer real-time protection, enabling continuous monitoring of your system. This feature scans downloaded files, monitors network traffic, and prevents malicious activity from infecting your Mac. Whether you are browsing the web, opening email attachments, or downloading files and applications, real-time protection ensures that infected files or potentially unwanted applications are stopped in their tracks.
Advanced threat detection
The most effective anti-malware solutions employ a multi-layered approach to detect both known and zero-day threats. Signature-based detection compares files against a database of known malware patterns, acting like a digital fingerprint system to identify malicious codes.
Heuristic analysis goes a step further by identifying suspicious behavior, such as unusual file modifications or encryption attempts, protecting your device from zero-day threats that have not been identified and documented before.
On the other hand, behavioral monitoring tracks how applications interact with your system and flags any unusual activity. Together, these methods provide reliable and effective malware protection, ensuring known and unknown threats are detected and neutralized before they enter your device.
Ransomware protection
Ransomware is one of the most destructive forms of malware, leading to catastrophic consequences for both individual users and organizations through encrypting databases and demanding a ransom to be paid in order to retrieve access to your files.
Reputable anti-malware tools will actively monitor your system for encryption attempts and block unauthorized changes to your files in order to intercept such an attack before things escalate.
Furthermore, these tools are able to automatically create secure backups to ensure your data can be restored if an attack occurs, without losing a single file. For businesses, this feature is non-negotiable, as ransomware attacks can totally paralyze the workflow of the entire organization and lead to significant financial losses and reputational damages.
Web protection
Malware often spreads through malicious websites, fake websites, or malicious downloads. A good scanner should block access to harmful sites, scan downloaded files in real-time, and warn you about phishing attempts before you enter sensitive information. Thus, preventing malware from even thinking of reaching your system and allowing you to review these files and decide whether they are safe or must be removed. This is especially useful for avoiding false positives, where legitimate files are mistakenly flagged as malware threats.
Quarantine management
When the malware scanner detects suspicious content, it must quarantine the infected files rather than immediately deleting them. Quarantine features isolate potential threats in a secure environment, preventing infection from spreading across your system, allowing you to review these files and decide whether they are safe or must be removed. This is especially useful for avoiding false positives, where legitimate files are mistakenly flagged as malware threats.
Performance optimization
A well-designed anti-malware software balances protection with system speed. It should schedule full scan operations during idle periods and employ smart algorithms prioritizing high-risk areas. The software should maintain your Mac's performance while providing comprehensive security.
Cloud-based protection
Cloud-based scanners leverage real-time threat data from the cloud to improve malware detection and response times. This ensures your protection tool is always up-to-date with the latest malware patterns and can quickly adapt to new threats.
Email protection
Emails are a common vector for malware distribution; every reliable anti-malware software should be able to analyze email attachments for malware and detect phishing attempts that try to steal your credentials or sensitive information.
Without email protection, you could accidentally open a malicious attachment or fall for a phishing scam, compromising your data and privacy. Bear in mind that you must also be able to recognize such harmful emails; they contain grammar and spelling errors in the text, so be aware when checking your emails.
USB/External drive scanning
Malware can spread through external drives, making USB and external drive scanning a critical feature. Your anti-malware software must be able to automatically scan USB drives and other removable storage devices once they’re connected to your Mac, preventing potentially unwanted applications from spreading. Without this feature, you risk introducing malware to your system when plugging in an external device.
Customizable scanning options
Look for a program that offers quick scans to check critical areas for immediate threats, full system scans to thoroughly examine your entire system, and custom scans to target specific locations or files. Scheduling options allow you to automate scans to run at convenient times.
Regular updates
Threat databases must stay current to provide effective protection, so the anti-malware software should automatically download and install security updates frequently, ensuring protection against the latest threats without requiring user intervention.
Backup and recovery
The best anti-malware solutions offer advanced backup and recovery features, ensuring that you won't lose a single file under any circumstances.
Clean interface and usability
Even the most powerful anti-malware program is useless if it’s hard to use. Choose a solution with an intuitive interface that provides clear information about detected threats and easy access to key features.
Acronis True Image: The ultimate Mac malware scanner
Have you noticed your Mac behaving strangely — even experiencing brief slowdowns or performance issues? Many of us immediately question, "Is my Mac infected with malware?" While performance issues don't always indicate such an attack, the growing sophistication of cyberthreats means Apple's built-in security features may no longer provide sufficient protection against modern attacks, making you constantly wonder if you are the next victim of the cybercriminals.
Fortunately, there is a way to stop malware from infecting your devices or prevent a ransomware attack from encrypting your invaluable files, where the options would be only two: pay the ransom or lose your data permanently. Acronis True Image is the ultimate solution to your concerns, offering an all-in-one solution for robust ransomware protection, reliable file and image backups, automatic rollbacks and efficient cloud storage.
Knowing you’ll never lose a single file, no matter what happens, is a true advantage — so why wait for disaster to strike before acting? Act today by choosing Acronis True Image, a solution equipped with advanced features and technologies to protect your devices. Let’s explore what makes it stand out and how it effectively defends your device from nasty macOS malware attacks:
Real-time protection and advanced threat detection
Acronis True Image isn’t just about backups—it’s your Mac’s 24/7 digital security guard. Using AI-based behavioral analysis and proactive vulnerability assessments, it constantly monitors your system for suspicious activity. Whether it’s an unauthorized encryption attempt or an unusual file modification, it springs into action immediately, blocking threats in real-time. This proactive approach ensures that even zero-day ransomware attacks—exploits that target unknown vulnerabilities—are intercepted before they can harm your device.
But Acronis True Image doesn’t stop there; the behavioral analysis capabilities allow it to learn and adapt, identifying new and evolving threats that traditional signature-based detection might miss. Combined with AI-driven insights, this multi-layered defense system provides unparalleled protection for your devices.
System performance
The software is designed to maintain a low system footprint, ensuring that your Mac’s performance remains optimal while providing enterprise-grade protection against ransomware and other destructive threats.
Integrated backup solution
What truly sets Acronis True Image apart is its integrated backup functionality; it automatically creates incremental backups of your files, ensuring that you can quickly restore your system to a safe state if needed. These backups can also be scheduled to be performed hourly, weekly, or on a monthly basis, choosing between full, incremental, or differential backups. This dual functionality eliminates the need for separate backup and security solutions, making it a cost-effective choice for Mac users.
User interface design
You can easily configure real-time protection settings, manage backups, run different types of scans, and initiate system restores from a single console. The software also provides detailed reports on backup status and ransomware protection activities, giving you comprehensive oversight of your system’s security posture.
Regular updates and storage options
Acronis True Image receives regular updates to its behavioral analysis engine, ensuring it stays current with the latest ransomware threats. The backup system supports both local and cloud storage options, providing flexibility in your data protection strategy.
Step-by-step guide to using Acronis True Image Mac malware scanner
For your convenience, we have prepared a step-by-step guide that guides you through the following processes:
- How to install Acronis True Image
- How to run a full scan
- How to Enable Real-time Protection (Active Protection)
How to Install Acronis True Image
- Step 1: Locate and double-click the Acronis True Image installation package (with .dmg file extension)
- Step 2: Double-click the "Install Acronis True Image" icon in the window that appears.

- Step 3: Simply follow the on-screen installation wizard.
- Step 4: Enter your credentials when requested to complete the installation.
For users running macOS versions Mojave (10.14) or Catalina (10.15), additional configuration steps are necessary following the installation of Acronis International GmbH software. To enable comprehensive protection features, the system requires authorization for kernel extension loading.
To complete this configuration:
First, navigate to your System Preferences on your Mac. Next, locate and select the Security & Privacy section, then proceed to the General tab. When prompted, select Allow to grant the necessary permissions for kernel extension loading.
After completing these steps, your Acronis True Image installation will be fully functional with all protection features enabled.
How to Run Full Scan - Acronis True Image
- Step 1: Open Acronis True Image
- Step 2: Navigate to the “Protection” tab
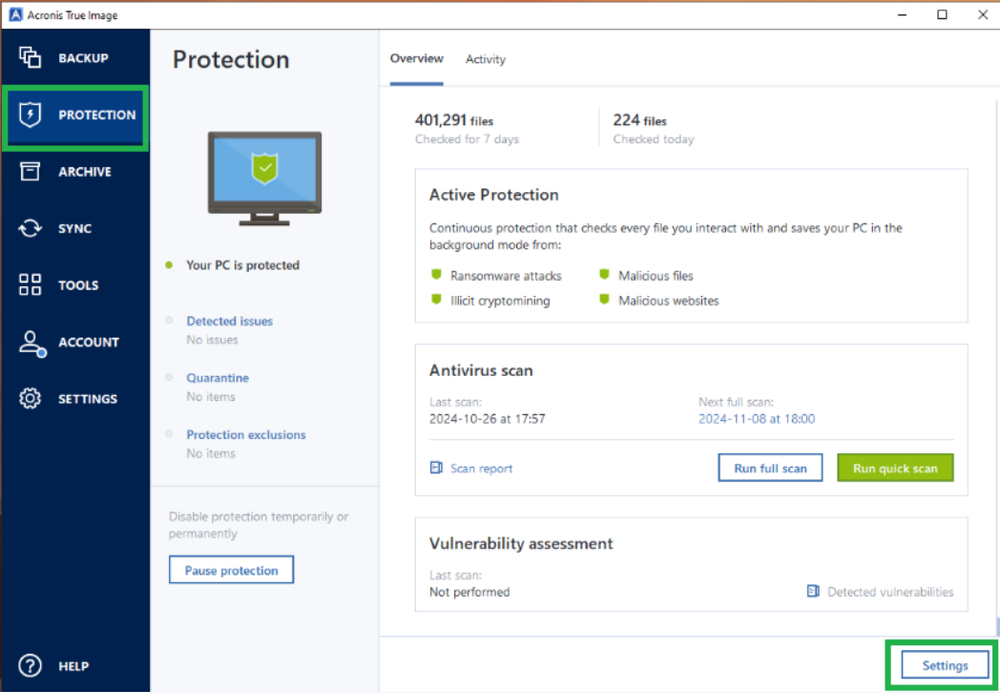
- Step 3: Click “Run Full Scan”
How to Enable Acronis True Image - Real-time Protection (Active Protection)
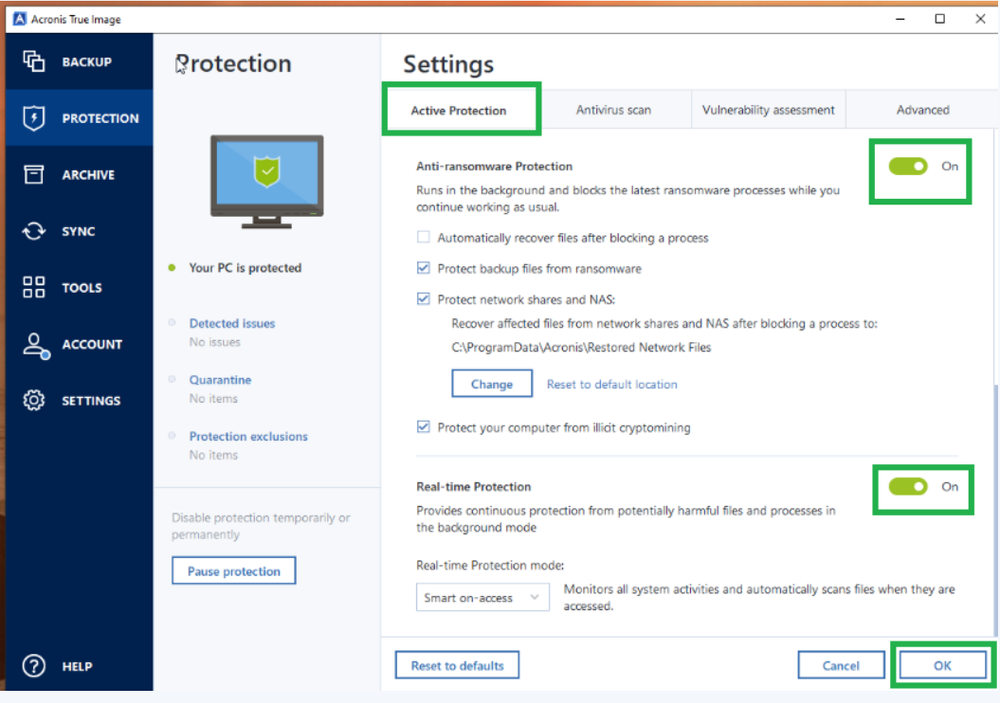
- Step 1: Log in to Acronis True Image.
- Step 2: Go to the Protection tab.
- Step 3: In the Protection tab, click Settings.

- Step 4: In the Active Protection tab, turn on the Anti-ransomware Protection, Real-time Protection, and Web filtering toggles to protect your computer and your personal files.
- Step 5: Click OK.
Best practices to keep your Mac malware-free beyond scanning
Equipping your Mac computer with a reliable and effective malware scanner is the foundation of building a reliable and effective malware-free security strategy. Still, there are many other steps to take to find the right path to your Mac’s safe land. What exactly are these best practices? We will discuss them in the following paragraphs.
Use strong passwords.
Daily, we use countless applications that require our credentials, which are the main target of cybercriminals. Breaking just one of your passwords can lead to catastrophic consequences if you use the same one across all applications, emails and social media platforms. The only way to prevent such a scenario is by using complex passwords, including capital letters, numbers, and special symbols, and their length should be at least fourteen characters. A password of this complexity would require at least five years to crack.
For enhanced identity protection, enable two-factor authentication (2FA) on all your critical accounts. This additional layer requires a verification code from your authentication app or a physical security key, making unauthorized access significantly more difficult even if your password is compromised.
Download only from the Mac App Store or official websites
Downloading apps or files from untrustworthy sources significantly increases the likelihood of a malware infection on your device. Want to keep your Mac malware-free? Then, use only the App Store or official websites because risking downloading even a single app or file from the wrong website can provide not only an application but a ticking bomb inside your device.
Be wise and use only the App Store when installing applications, because all of them have undergone security tests and reviews before being uploaded to the platform.
Regular system updates
Make sure to enable automatic updates through System Settings > General > Software Update; it takes less than a minute to ensure your device consistently receives the latest security updates and performance improvements.
Data protection
Use Apple’s Time Machine for backups or third-party software to ensure critical protection against potential security breaches, ransomware attacks, or any other malware that can compromise your invaluable information. When the disaster strikes, you must be prepared or you can lose your entire database forever.
Clear cache
Regularly erasing your cache helps eliminate potential malware hiding in temporary or junk files.
Monitor your Apple device health
Stay aware of signs of compromise, such as
unexpectedly slow performance, unusual network activity, suspicious access in
file sharing, unexpected redirects and the appearance of new toolbars; all
these are signs of being infected with malware.
Delete unused apps
Remove unused applications, since each installed app increases the attack surface of your device. Cybercriminals target software vulnerabilities in a variety of software applications to launch a malware attack through them. Deleting those apps will improve your system performance and free disk space.
FAQs about Mac malware scanners
Do Macs really need antivirus or malware scanners?
Yes, Macs absolutely need malware protection, despite Apple's built-in security features. The common belief that Macs are immune to malware stems from an era when cybercriminals primarily targeted Windows systems due to their larger market share. However, as Macs have grown more popular in business environments, they've become increasingly attractive targets for sophisticated attacks.
Can malware slow down my Mac?
Undetected malware can significantly impact your Mac's performance in several ways. Cryptojacking malware, for instance, secretly uses your processor to mine cryptocurrency, causing noticeable slowdowns and increased energy consumption. Other types of malware might run multiple background processes, consuming memory and processing power while conducting malicious activities.
Signs of malware-related performance issues include unexpected fan activation, battery drain, slow application launches, and system crashes. Other malware variants even disable system updates or security features, making your Mac increasingly vulnerable over time. The longer malware remains undetected, the more severe these performance impacts become.
What makes Acronis True Image different from free malware scanners?
Acronis True Image distinguishes itself through comprehensive protection and has proven to be significantly more effective compared to basic malware detection solutions. While free scanners typically rely on simple signature-based detection, Acronis employs a multi-layered approach, combining advanced behavioral analysis and AI/ML-driven technologies to identify and block suspicious activities before they can harm your system.
The software's real-time protection continuously monitors system activities, unlike free solutions that often depend on manual scans. Acronis True Image includes specialized ransomware protection, which not only creates secure, immutable backups of important files but also actively blocks unauthorized encryption attempts.
Additionally, the software leverages a cloud-based threat detection network to provide immediate protection against newly discovered threats, sharing threat intelligence across all protected systems.
Stay Secure with Acronis True Image
Protecting your Mac is no longer optional—it’s essential. With malware attacks growing smarter, more destructive, and harder to detect, relying solely on your Mac’s built-in security is like leaving your front door unlocked during a storm. Cybercriminals are constantly evolving their tactics, targeting devices without advanced protection to infiltrate systems, stealing sensitive data like credentials and banking information, or even deploying ransomware for complete system encryption.
The truth is your Mac’s native defenses aren’t enough to stop these sophisticated threats. But there’s a solution that can: Acronis True Image. This all-in-one solution combines advanced ransomware protection, adaptive local or cloud backups (for your entire disk or selected files and folders on a flexible schedule), and instant recovery features to maximize cybersecurity. Whether it’s a malicious attack or accidental data loss, Acronis ensures you’ll never lose a single file—no matter what happens.
Imagine the peace of mind of knowing your data is secure, no matter the circumstances. With its robust features and cutting-edge technology, Acronis True Image doesn’t just protect your Mac; it prepares you for the unexpected, giving you the tools to stay a step ahead of cyberthreats.
Don’t wait for disaster to strike. Take control of your Mac’s security today. Download Acronis True Image now and make tomorrow safer and more secure for you and your Mac!
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.




