As the value of cryptocurrencies like Bitcoin and Monero skyrocketed last year, a more sinister trend came with it. Cybercriminals saw the opportunity to hijack unprotected computers to use their processing power to mine cryptocurrency – an activity that involves calculating extremely complex mathematical problems.
Those calculations require a lot of CPU resources and electricity, so hackers use browser mining scripts to illicitly using other people’s computers (called cryptojacking) so they can mine cryptocurrencies at no cost.
In this article, we’ll explain how you can protect your system from browser mining so it’s not used as a get-rich-quick vehicle for cybercriminals.
Cryptomining costs
First, we need to understand the nature of cryptocurrencies. These digital currencies are based on cryptography (also referred to as hash algorithms) that record financial transactions. There are only a certain number of hashes available, which help establish the relative value of each unit.
Creating new units of a cryptocurrency involves solving complex mathematical problem. The first person to solve the problem gets paid for their efforts in that cryptocurrency. That means legal cryptominers must invest in server farms for computing power, tremendous amounts of electricity, and cooling systems that help keep their mining operations efficient as they crunch the numbers.
Spreading the wealth with cryptomining
Browser mining scripts are not all malicious. Some websites have been experimenting with them as a possible revenue generator that would replace online advertising. One of the first websites to try this approach, for example, was Quartz. The idea of spreading cryptomining efforts across multiple user computers in exchange for access to the website seemed reasonable, especially since the user would be informed and asked to agree to the deal.
Unfortunately this approach has been abused by criminals. Rather than invest in the infrastructure needed for legitimate cryptomining, they look at browser mining scripts as a way to avoid those costs. And whether it’s Coinhive offering Monero mining tools that you insert into a website, or Coinhive alternatives like EObot and Awesome Miner that have browser Bitcoin miners, criminals have the tools needed at their fingertips.
The result is cryptojacking.
How to tell if your computer been cryptojacked
Given the drain on your CPU, if your computer suddenly is running slowly or your battery is draining particularly fast, you might have been hacked. How can you tell?
Open up your Windows Task Manager or macOS Activity Monitor and click on "Processes." If you see that your browser is working overtime, you can shut it down and restart. Unfortunately, this doesn't tell you what site ran the browser mining script.
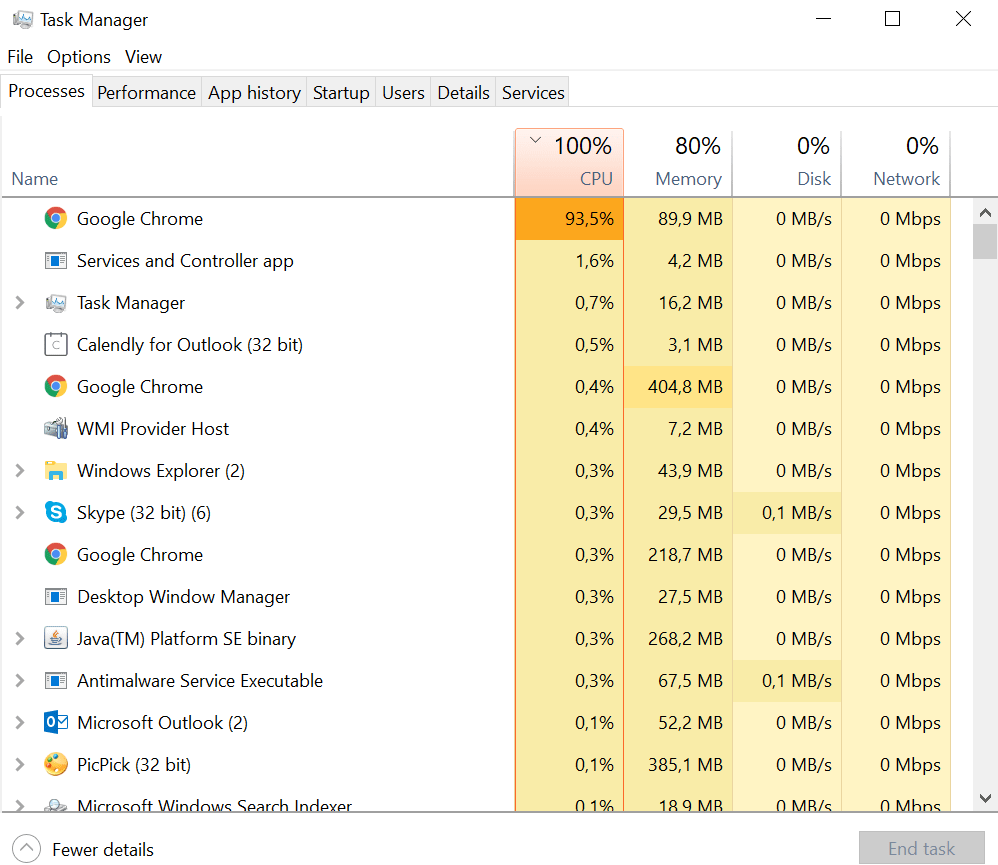
Unfortunately, hackers are making it harder to spot their efforts. While older scripts maximized CPU use, new cryptomining scripts throttle back to as little as 20 percent, making them more difficult to detect.
Stopping cryptomining in browsers
While manually identifying attacks is much harder now, there are preventative steps you can take that will automatically reduce your exposure and vulnerability to browser-based attacks.
Deploy Browser Extensions
Most popular web browsers now include extensions that can help stop web-based cryptomining attacks. These can include both solutions developed by the browser developer, or open-source extensions that can be added on. The No Coin and MinerBlocker solutions, for example, monitor for suspicious activity and block attacks, and both have extensions available for Chrome, Opera, and Firefox.
Ad-Blocker Software
Given the explosion of cryptomining malware, many ad-blockers now include a Coinhive blocker that filters the script from running on your browser. If you have an ad-blocker installed, you’ll need to select that script blocker.
Disable Javascript
If you want to completely block certain attacks, most browsers will allow you to disable JavaScript – although many legitimate websites still use JavaScript, so disabling it may cause problems.
Block Domains
You can also block specific domains that you suspect of cryptomining. Simply open your browser, find the "Customize" drop-down, and then block a URL. To block Coinhive, you can copy/paste https://coin-hive.com/lib/coinhive.min.js into the text box.
Final Thoughts
Blocking browser mining scripts is an important step to take to ensure the integrity and operational efficiency of your system – and the steps needed to secure your computer are not very complicated.
Keep in mind, however, there are many cryptojackers that are not browser based. Instead, they are standalone programs that infect your system directly, often including ransomware to maximize their profitability. To combat those standalone variants, you might consider Acronis True Image 2020 Cyber Protection, which provides both proven backup capabilities and an integrated anti-ransomware and cryptomining malware blocker that is powered by artificial intelligence.
By protecting against both browser mining and standalone cryptomining malware, you can stop cybercriminals from ever using your system as their personal cash machine.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



