They say crime doesn’t pay, but clearly the architects behind GandCrab ransomware didn’t get that memo. They recently announced they were retiring thanks to the money they’ve made encrypting victims’ computers.
At the beginning of June, operators of the notorious GandCrab strain of ransomware announced that “all good things come to an end” and they are ceasing their operations.
Unfortunately the success they reported will likely provide a roadmap for other cybercriminals that will continue for a long time.
“Printing money” with ransomware-as-a-service
The people behind this malware claim that they helped their “customers” collect more than $2 billion since the ransomware launched in January of last year.
By using the ransomware-as-a-service (RaaS) model, the developers of GandCrab reported that they earned at least $150 million for themselves, which they’ve already laundered by investing in various clean businesses.
All of those big money figures were powered, they say, by a weekly revenue that averaged $2.5 million.
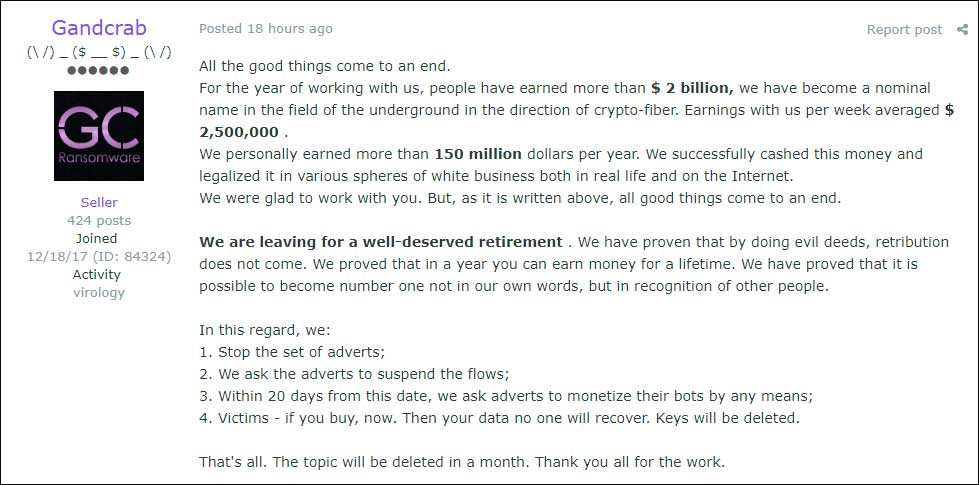
While some researches and security experts assume that these reported figures are exaggerated, it is clear that people behind the GandCrab took in a lot of money.
Successful criminal organization
GandCrab’s success was due to well-planned operations, a systematic approach, and constant support of the malware. The owners of GandCrab used the RaaS model to extend its reach, partnering with botnet operators and other affiliate cybercriminals to generate widespread virulence.
The RaaS model is much safer for the criminals because if they were ever caught by law enforcement, many countries have weak cybersecurity legislation. The logistics of the RaaS model also make it much easier for the owners, since they basically rent their malware and receive a commission, so they do not need to worry about the actual execution of attacks.
Broad distribution of GandCrab
We know that during its lifespan GandCrab was distributed in a variety of ways: via spam emails, exploit kits, targeted social engineering efforts, fake software downloads, and malicious websites. It was also spotted as the final payload for a series of attacks that exploit the Oracle WebLogic bug (CVE-2019-2725).
Some attackers have customized the code as well. PowerShell code was launching from malicious Excel spreadsheets, which were rewrapped to avoid detection by signature-based security tools in order to infect Windows-based machines in Italy. According to researchers, the script then downloaded a picture of Super Mario which contains more PowerShell code – and ultimately downloads GandCrab ransomware to encrypt files and network assets.
The technique of hiding malware within images is not new but still work like a charm with a lot of security solutions.
GandCrab infections worldwide
It is estimated that over 1.5 million Windows users have been infected with GandCrab since it first emerged in January 2018. During the past year and a half, GandCrab developers released five major versions of malware, continuously improving it to stay ahead of the security companies who were releasing decrypting tools (which delivered various levels of success).
Two weeks after the announcement of GandCrab’s “grand finale”, Bitdefender released a decryptor tool that can save data even after the latest 5.2 version of the malware. The effectiveness of the tool is not based on a flaw in GandCrab code, but rather in having gained access to GandCrab command and control servers in order to download the decryption keys needed to unlock a victim's files.
This new tool was released under the “No more ransom” initiative – of which Acronis is a part. The tool was not just from BitDefender, but is rather the result of a collaborative effort by Europol, the FBI and others.
Retiring GandCrab opens the door for more
While we can celebrate the closing of GandCrab, the example set by its owners is very important from many standpoints. While some people may think that combined effort or law enforcement and security firms finally won over bad guys, the situation may be quite the opposite.
In fact, GandCrab’s operators proved that:
- With ransomware-as-a-service, anyone with bad intentions can earn big money.
- Ransomware-as-a-service is a much safer approach to cybercriminal activity. While the operators are guilty, if caught they would suffer fewer charges because they did not infect victim directly.
- They showed how to “quit while you’re ahead”. They weren’t caught and collected a good amount of money at the same time. Lame cybercriminals do not know when to quit and end up in jail. These guys had a proper plan.
- Surprisingly, they behaved with understanding several times, showing some “humanity”. They didn’t encrypt the data of Syrian people during the conflict when it was very personal and emotional. They also warned victims recently that they shouldn’t pay anymore, as the data won’t be decrypted and they will simply lose the money. By making such actions public, it actually motivates other people to pay since the operators were seen as having some code of conduct – and that when you pay, you will get your data back.
Ransomware isn’t going anywhere
Despite the end of GandCrab, ransomware remains one of the largest threats to organizations, and attacks will continue to grow in numbers. In January 2017, there were 635 ransomware campaigns. By February 2018 that number nearly doubled to 1105. In January 2019 it rose to 1453 ransomware campaigns.
That is why having a proper anti-ransomware defense like the AI-powered Acronis Active Protection embedded into cyber protection solutions such as Acronis True Image or Acronis Backup is absolutely essential for today’s data users.
Final thought
If there is one thing the GandCrab example shows, it’s that if people and organizations pay the ransom, they’ll only encourage bad guys to continue doing what they do. With effective cyber protection that combines the safety and accessibility of backup with the security of innovative anti-malware technology, users won’t have to pay a ransom – and will help discourage criminals from turning to ransomware.
If users don’t adopt modern cyber protection or have a backup in place, all they can do is hope a decryptor tool will be released one day.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.




