
With mounting responsibilities and skills shortages, IT professionals are overburdened, making a threat more likely to slip past their defenses. To complicate things further, cybercriminals now have a helping hand from AI, which helps them operationalize and automate sophisticated attacks.
The newly released Acronis Cyberthreats Report, H1 2024 details these and other challenges for businesses across the globe. In this report, we explore new ransomware groups, changes in ransomware patterns, emerging attacks on collaboration apps and developments in AI threats.

Key findings from the report:
- Bahrain, Egypt and South Korea were the most targeted countries in malware attacks in Q1 2024.
- Nearly 28 million URLs were blocked at the endpoint by Acronis in Q1 2024, a 3% increase over Q4 2023.
- 27.6 % of all received emails were spam — 1.5% contained malware or phishing links.
- Each malware sample lived an average of 2.3 days in the wild before it disappeared — 82% of samples were seen only once.
- There were 1,048 publicly reported ransomware cases in Q1 2024, a 23% increase over Q1 2023.
- Three highly active groups were the primary contributors to ransomware attacks, collectively responsible for about 35% of the attacks.
- LockBit accounted for 20% of ransomware attacks, followed by Black Basta and PLAY, with 7.1% and 7.0% respectively.
LockBit was taken down a peg, but ransomware gangs persist
Acronis observed a 5% increase in the number of new malware samples in the wild since Q4 of 2023. When we zero in on ransomware, the first few months of 2024 were dominated by LockBit, Play, 8Base, BlackBasta and Hunters International, the most active ransomware gang. These all-too-familiar groups continue to wreak havoc on organizations worldwide.
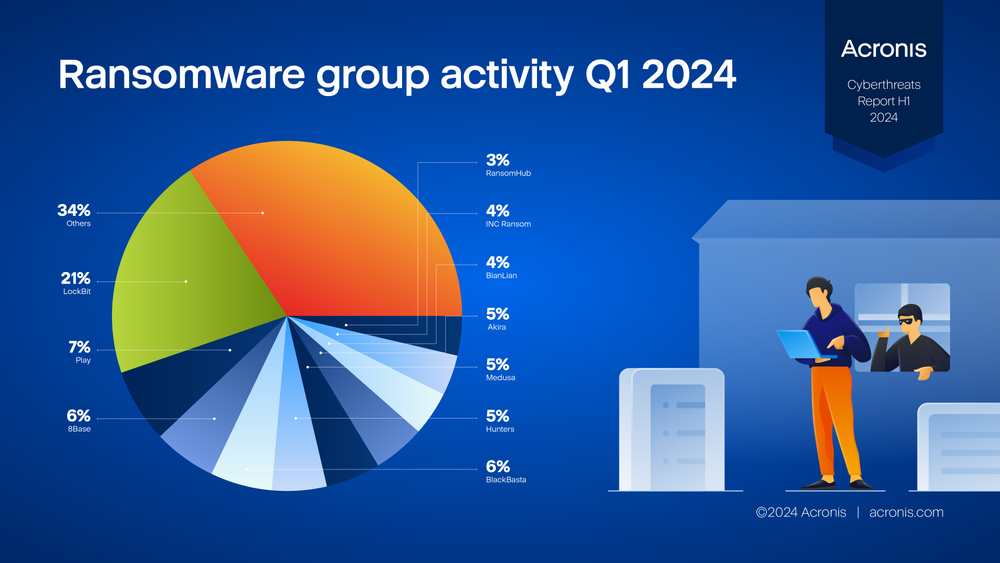
Ransomware activity continues to climb year over year, but the data reveals a 46% decrease in ransom payments in H1. This decline is a promising sign of increased cyber resilience throughout organizations and improved security efforts within private and public entities. Despite ransomware attacks being easier to launch, profitability was hindered.
In another win, the U.K.’s National Crime Agency (NCA) made monumental progress in the battle against LockBit ransomware. With the support of Europol, the NCA led Operation Cronos. The months-long stint resulted in overtaking LockBit’s primary platform and critical infrastructure, including 34 servers across the Netherlands, Germany, Finland, France, Switzerland, Australia, the U.S. and U.K. However, LockBit reemerged and reengaged in cybercrime despite the arrests of some key LockBit criminals.
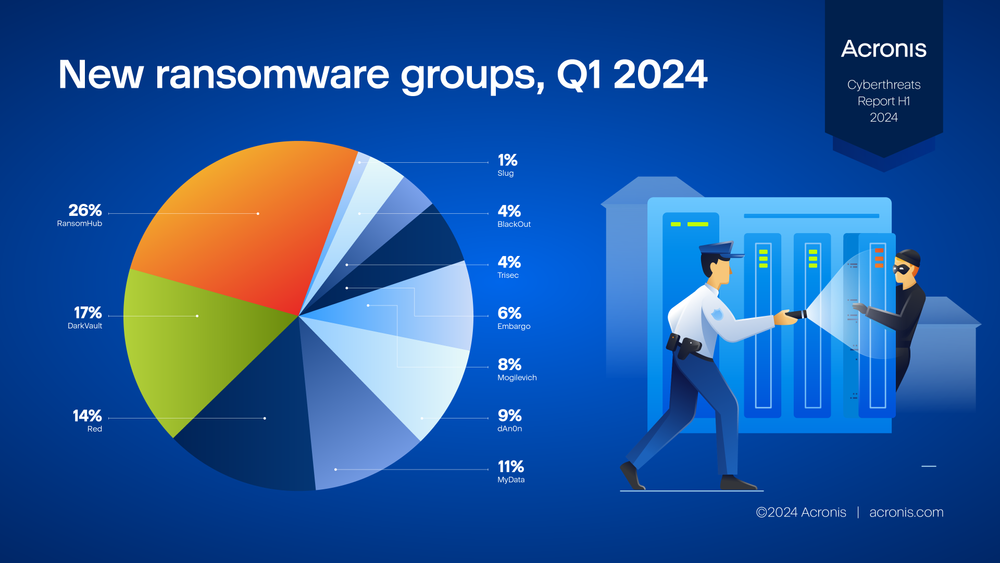
While ransomware payments decreased and ransomware operations were significantly disrupted, daily ransomware detections increased 32% from Q4 2023 to Q1 2024. Additionally, 10 new ransomware groups emerged in Q1 2024:
1. Mogilevich (7)
2. RansomHub (22)
3. dAn0n (8)
4. DarkVault (14)
5. Red (12)
6. Trisec (3)
7. Slug (1)
8. MyData (9)
9. Embargo (5)
10. BlackOut (3)
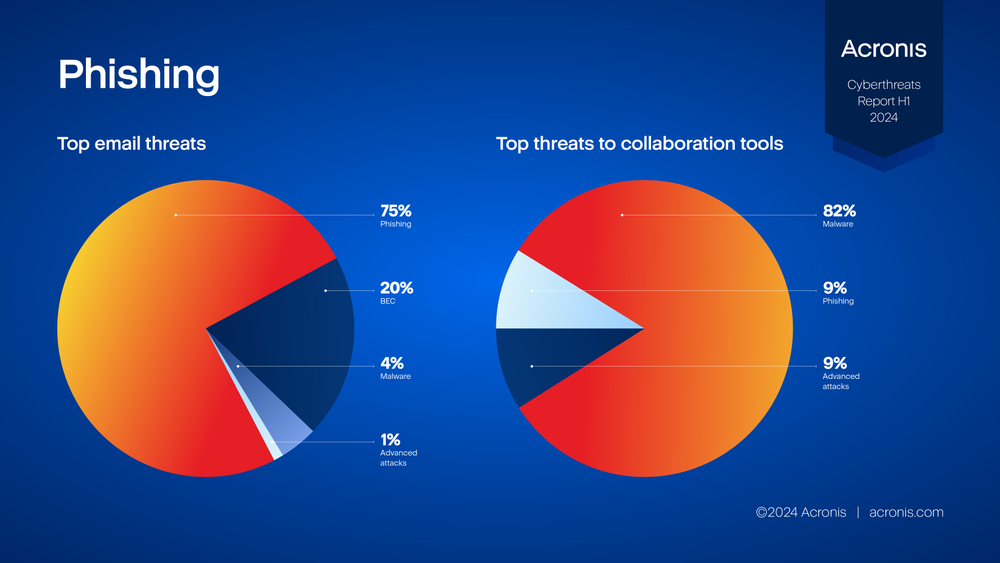
Phishing remains the top threat, but malware is the #1 threat to collaboration apps
Organizations experienced a significant surge in email communications in H1, with the number of emails per organization increasing by 25%. This rise in email volume has been paralleled by a concerning 47% increase in email attacks targeting these organizations.
Among the attacks, 26% of users encountered phishing attempts through malicious URLs, demonstrating cybercriminals' continued reliance on what is still the #1 attack type. Additionally, 13% of users received malware via email, highlighting the diverse methods attackers employ to compromise systems and steal sensitive information. Finally, social engineering increased 5% since H1 2023, while malware attacks decreased from 11% in H1 2023 to 4% in H1 2024.
As more companies rely on collaboration apps like Microsoft 365, attacks within those applications, including Microsoft Teams, is on the rise. While phishing is a popular method of attack in collaboration apps (20%), 82% of attacks in H1 were malware-based attacks.
Generative AI in cybercrime became clearer
The misuse of generative AI and large language models (LLMs) played a role in perpetuating attacks throughout H1. We wanted to make a clear distinction to help security-focused organizations better understand AI-powered attacks. The Acronis Cyberthreats Report, H1 2024 defines two types of AI threats that are commonly used synonymously: AI-generated threats and AI-enabled malware.
The term “AI-generated threats” is tossed around in headlines and the cybersecurity community. At Acronis, we want to put emphasis on the “generated” portion. These are the malware and threats that are created using AI techniques but do not incorporate AI in their operations. In this case, AI is solely a tool used for malware and threat creation.
When it comes to “AI-enabled malware,” the phrase is more complex. We define this as malware that integrates AI within its functionality. It may contain a complete AI model, such as an LLM, but more commonly, it communicates with a backend AI model for logic. AI-enabled malware threats can adapt to their environment and modify their behavior.
The report covers six popular AI-generated attacks that we observed, including malicious emails, deepfakes used in business email compromise, deepfake extortions, KYC bypassing, script generations and malware generation. The Acronis Cyber Protect Operation Centers team also shares practical recommendations for MSPs and businesses based on report findings.
Experts recommend: A reemphasis on security awareness training and solution consolidation
Educating MSP and business employees on cybersecurity best practices has proven to be effective against the prolific threat landscape. As we saw a noticeable dip in ransomware profitability, improved security awareness and enhanced measures may have contributed to this accomplishment. Both human-led efforts and cybersecurity technologies are equal parts of the cyber resilience equation.
On one hand, security awareness training enables employees to recognize and report phishing attempts, social engineering tactics and suspicious activity. On the other, reinforcing security measures not only involves investing in cutting-edge technologies but also taking an integrated approach to cybersecurity and data protection to augment IT management, efficiency and performance — and reduce costs and compatibility issues. With integrated solutions such as Acronis XDR, MSPs can make their security offering more competitive while boosting visibility and protection across attack surfaces.
Download the report to uncover the top cybersecurity threats and trends from H1 2024.

About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.




