WastedLocker ransomware was supposedly used by the Evil Corp group, which is known to have delivered Dridex banking malware to attack at least 31 U.S.-based corporations since May 2020. Here we provide an in-depth analysis of WastedLocker, which employs numerous defensive evasion techniques such as digital signing, DLL side-loading, auto-elevation and alternate data streams .
Attack overview
To deliver ransomware, the attackers used SocGholish, a malicious JavaScript-based framework that had been deployed on compromised websites as a result of vulnerability exploitation.
SocGholish gathers information about the victim's system and if it belongs to the targeted corporate environment, downloads a ransomware that pretends to be a fake software update. In this way, the criminals gain their initial access to the target corporate network.
After that, Cobalt Strike‘s Beacon — a “red team” tool — was used by the attackers for internal reconnaissance, elevation of privileges, disabling security tools, internal network proliferation — and finally, deploying WastedLocker ransomware on Windows computers with the help of Windows-native admin tools such as PsExec and WMIC.
Static analysis
SHA256: 5cd04805f9753ca08b82e88c27bf5426d1d356bb26b281885573051048911367
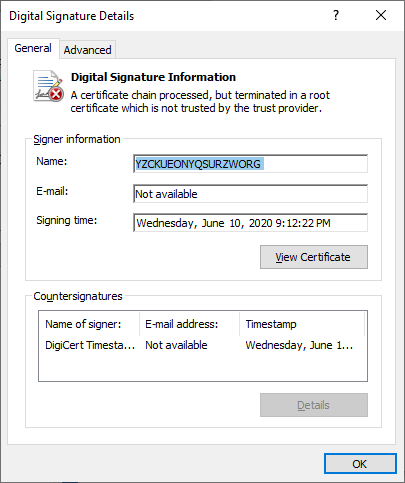
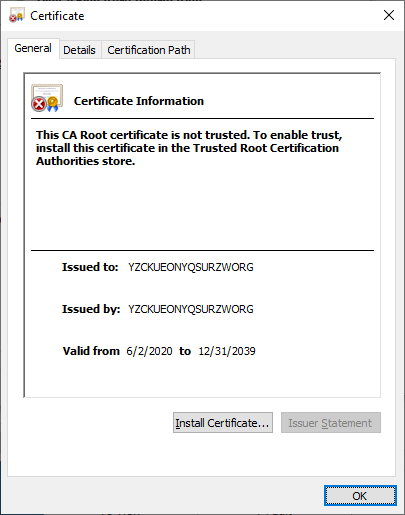
The ransomware is a PE file which is signed with the self-signed certificate.
It is also protected with a CryptOne cryptor that embeds the junk calls to obfuscate the code and litter the sandbox dynamic analysis logs.
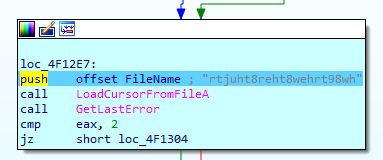
Installation
Once started, the ransomware loader schedules its own removal for 10 seconds after execution:
cmd /c choice /t 10 /d y & attrib -h "C:\Users\<USER>\Desktop\WastedLocker.exe" & del "C:\Users\admin\Desktop\WastedLocker.exe.exe"
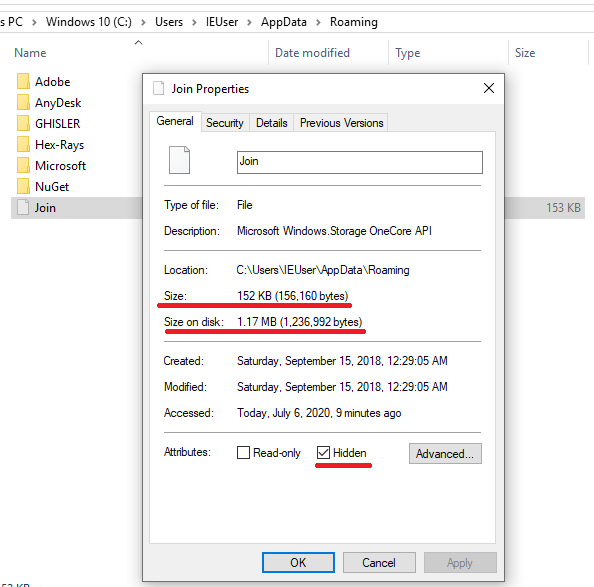
Then, it drops its binary into a user’s folder with the attribute ‘hidden’:
- C:\Users\<USER>\AppData\Roaming\<Random name> (18.64 Kb, SHA256: A256D30A99870B14A7A752F6F216F207D1C4453478908D6353A8511904BF2542)
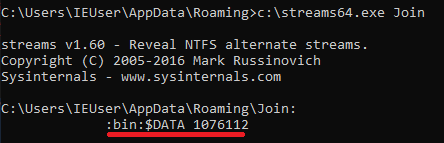
To hide its payload, the ransomware dropper creates an alternate data stream (ADS) named as ‘bin’ and saves its code to it:
- C:\Users\<USER>\AppData\Roaming\<Random name>:bin (1.03 Mb, SHA256: 5CD04805F9753CA08B82E88C27BF5426D1D356BB26B281885573051048911367)
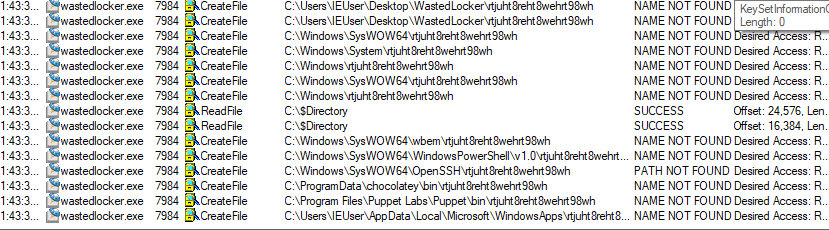
The dropped files also include the Windows System Assessment Tool (WinSAT). While ‘winsat.exe’ is the original Microsoft application, winmm.dll is altered to embed the ransomware payload from ‘Providers:bin’ ADS:
- C:\Users\<USER>\AppData\Local\Temp\3B5A\system32\winsat.exe (212 Kb, SHA256: A6B45DB4A9D9A423B85491FFD7686BD2E3BAA358D72C1AF6494AF3069DB4C316)
- C:\Users\<USER>\AppData\Local\Temp\3B5A\system32\winmm.dll (3.77 Mb, SHA256: 9AECD7C83CE46625F3C52F765F864630866714CDE232C49F65C88B2BC8227245)
After that, it executes Windows process ‘winsat.exe’ which loads the ransomware payload from ‘winmm.dll’. This technique is called DLL side-loading, and is used by attackers as a defense evasion technique. Winsat.exe also belongs to the list of Windows executables that are allowed for UAC auto-elevation, which helps attackers to bypass UAC.
WastedLocker also sets the following values in the ‘Internet Settings’ registry key to enable access to the internet — supposedly to access remote drives:
The <Random name>:bin’ executable then changes the name and executes itself again with the command line option ‘-r’ from ‘C:\Users\<USER>\AppData\Roaming\’ folder. This mode is used to prepare the ransomware for encryption that includes the following stages:
- Deleting
shadow copies, so that victims cannot restore their files from a previous
version:
C:\Windows\system32\vssadmin.exe Delete Shadows /All /Quiet - Copying the ransomware payload to %System32% as:
C:\Windows\system32\<Random name>.exe - Taking ownership of the copied ransomware binary:
C:\Windows\system32\takeown.exe /F C:\Windows\system32\<Random name>.exe - Resetting the ACL permissions:
C:\Windows\system32\icacls.exe C:\Windows\system32\<Random name>.exe /reset - Creating and running a service which is deleted once all available files have been encrypted.
After that, the ransomware starts file encryption by launching with the option ‘-s’.
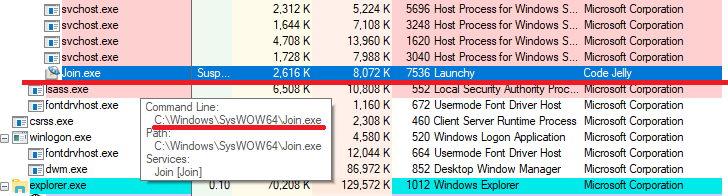
Once encryption is completed, the cmd line
script deletes the ransomware binary in 10 seconds:
cmd /c choice /t 10 /d y & attrib -h "C:\Windows\SysWOW64\<Random name>.exe" & del "C:\Windows\SysWOW64\<Random name>.exe"
Encryption
WastedLocker targets files on removable, fixed, shared and remote drives. The encryption is run with multiple threads within the process executed from the binary copied to the Windows folder under administrative privileges.
The ransomware does not encrypt files with the following extensions and paths:
*.rlhwasted, *.rlhwasted_info, *\ntldr, *.386, *.adv, *.ani, *.bak, *.bat, *.bin, *.cab, *.cmd, *.com, *.cpl, *.cur, *.dat, *.diagcab, *.diagcfg, *.dll, *.drv, *.exe, *.hlp, *.hta, *.icl, *.icns, *.ics, *.idx, *.ini, *.key, *.lnk, *.mod, *.msc, *.msi, *.msp, *.msstyles, *.msu, *.nls, *.nomedia, *.ocx, *.ps1, *.rom, *.rtp, *.scr, *.sdi, *.shs, *.sys, *.theme, *.themepack, *.wim, *.wpx, *\bootmgr, *\grldr
Nor will it encrypt files in the following folders:
*\$recycle.bin*, *\appdata*, *\bin*, *\boot*, *\caches*, *\dev*, *\etc*, *\initdr*, *\lib*, *\programdata*, *\run*, *\sbin*, *\sys*, *\system volume information*, *\users\all users*, *\var*, *\vmlinuz*, *\webcache*, *\windowsapps*, c:\program files (x86)*, c:\program files*, c:\programdata*, c:\recovery*, c:\users\ %USERNAME%\appdata\local\temp*, c:\users\ %USERNAME%\appdata\roaming*, c:\windows*
Files are encrypted using AES-256-CBC, and renamed by adding the ‘.rlhwasted’ extension.
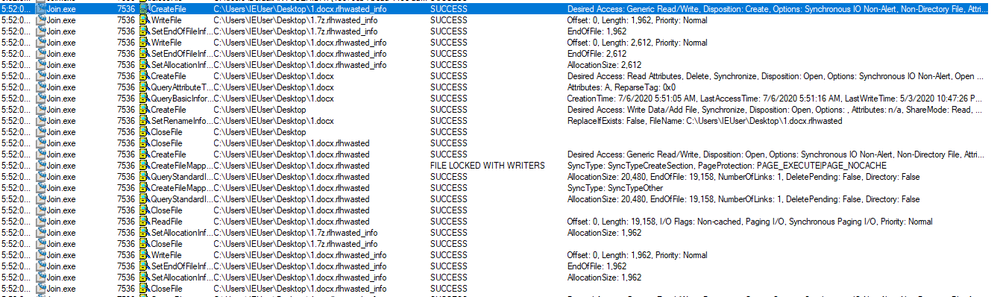
First, WastedLocker renames a file and maps the file’s content to the memory.
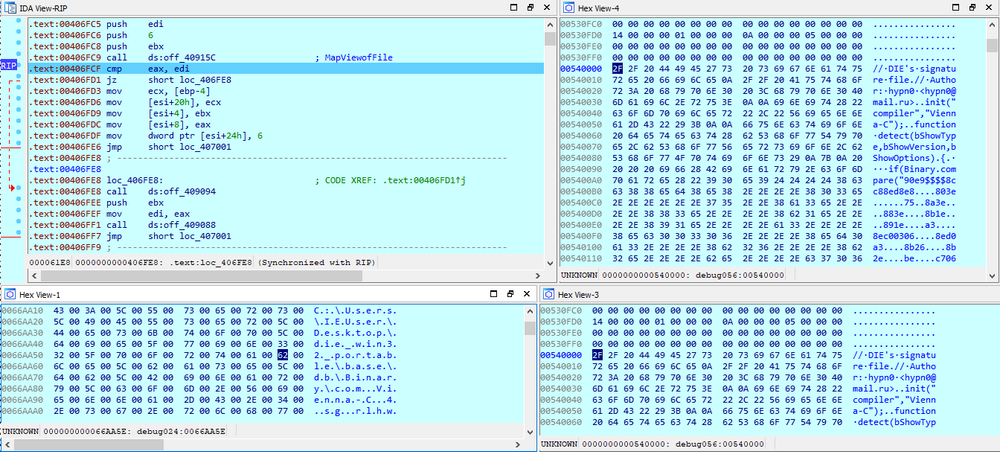
The encryption process consists of the following steps:
- The AES-256 key and IV are generated for every file.
- Files are encrypted.
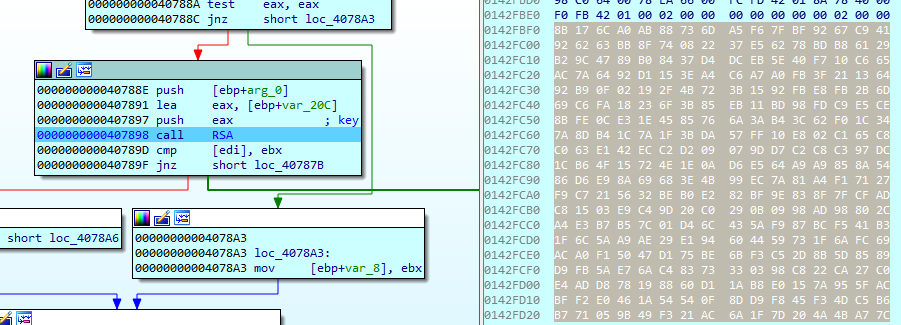
- File keys are encrypted with the public Master RSA-4096 key stored in the ransomware body.
- The encrypted file keys are encoded with Base64 and stored in a ransom note for every encrypted file.
File encryption with AES-256-CBC and no padding:
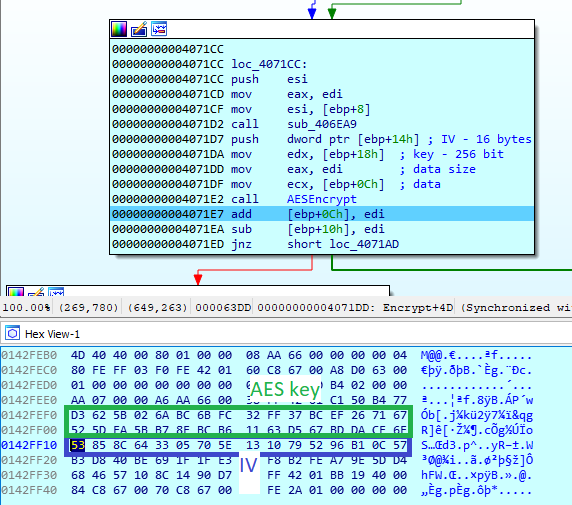
Еncrypting the file key is done using the 4096-bit master public RSA key hardcoded in the ransomware binary.
Then, the encrypted file key and IV are Base64-encoded.
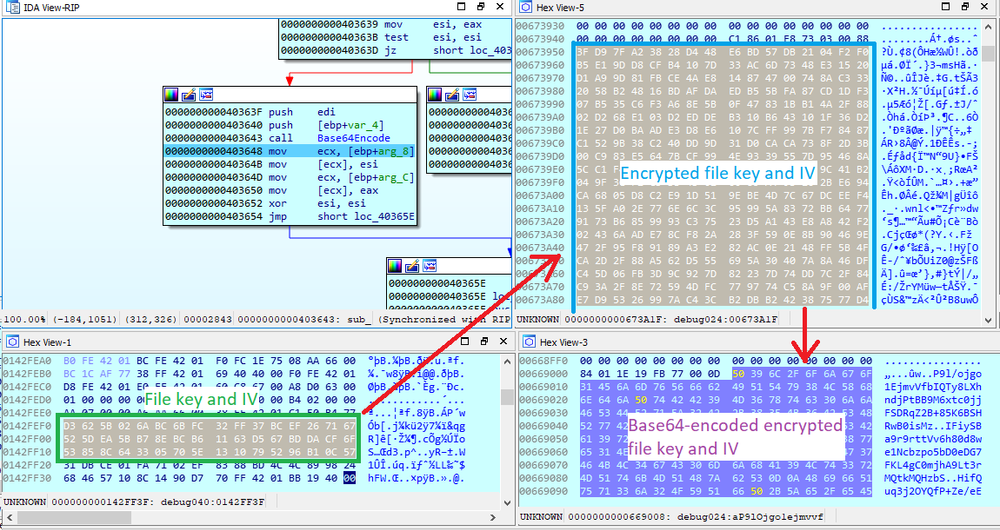
They then are stored to the file ‘<original file name>.rlhwasted_info’
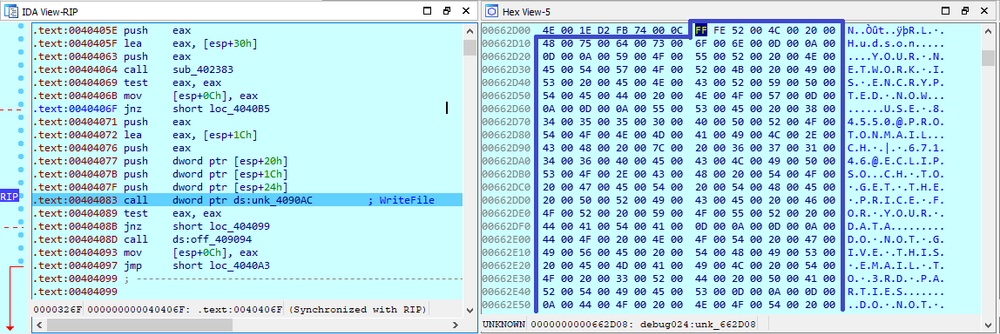
Unfortunately, it is generally not possible to decrypt the files without the decryptor provided by the attackers.
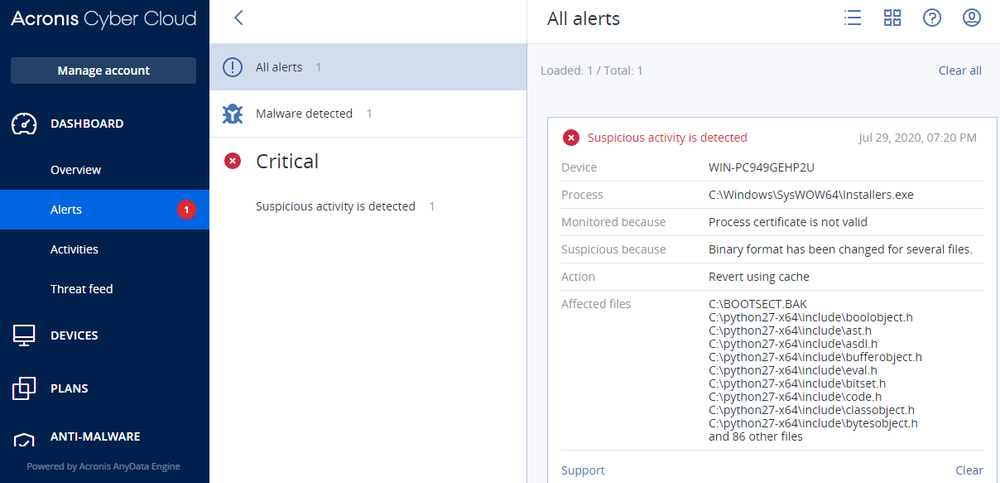
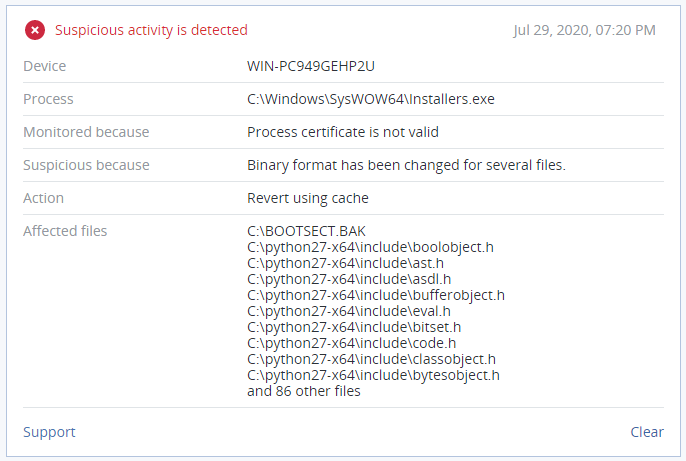
Ransom note
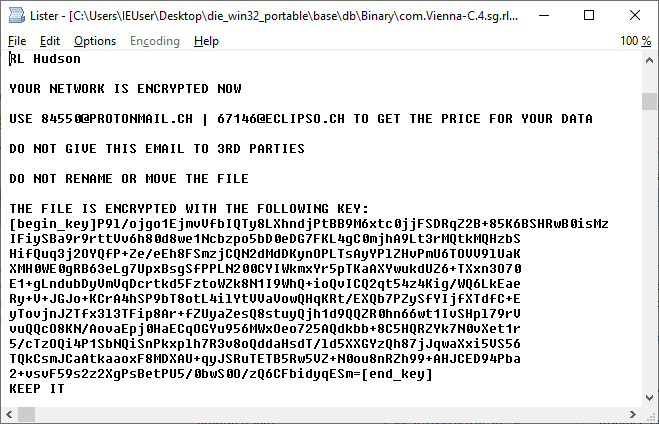
The ransom note ‘<original file name>.rlhwasted_info’ is created for every encrypted file and appears as follows:
Conclusion
Following the trend in ransomware development for targeted attacks, the authors of WastedLocker made attempts to protect the ransomware code against detection by anti-malware solutions. They employed digital signing and a PE cryptor as well as defense bypassing techniques used by APTs, such as auto-elevating of privileges with the help of the DLL side-loading attack and hiding payload code in alternate data streams before copying it to the Windows system folder.
The encryption scheme with file and master keys is specific to targeted attacks, and does not allow the decrypting of the victim’s files without the decryptor or master private key.
Acronis Cyber Protect Cloud (part of Acronis Cyber Cloud) detects and successfully blocks WastedLocker ransomware attacks: