In your search for the ideal endpoint security solution, Reddit and Spiceworks might be the first places you visit to get feedback and recommendations from fellow MSPs. Third-party analyst reports and peer review websites are also a good place to start.
But while these resources provide insight into endpoint security solutions based on market standings and feedback from real-life adopters, they do not consider the unique characteristics of your MSP business, including the size of your team, their existing skill set, and their limitations, all of which play a major role in your endpoint protection strategy.
Evaluating endpoint detection and response (EDR) and managed detection and response (MDR) does not boil down to a ‘this or that’ question. Many growth-minded MSPs leverage EDR and MDR full time and intermittently. The key is determining which is best for you, your clients and your stage of growth.
Here are seven factors to consider when evaluating EDR and MDR.
1. EDR integration
Traditional EDR solutions require additional integration to achieve adequate protection. These integrations need careful attention from skilled experts to ensure compatibility across multiple solutions.
A prime example is single-purpose patch management. Single-purpose patch management tools often require significant integration efforts when used with core endpoint protection solutions. Because these tools are typically siloed, they require a great deal of time, resources and attention to work effectively with EDR.
Cobbling EDR and other security tools together is labor intensive and prone to human error that can lead to security gaps. Multi-integration security creates additional complexity that can heighten compliance and cyber insurance concerns. With several vendors in play, this makes it more difficult to ensure that all solutions adhere to regulations and that clients meet all requirements.
During your evaluation, determine whether the EDR is natively integrated with other critical solutions. If not, determine if the required integrations will improve security or just increase complexity.
2. Deployment time
A common challenge that MSPs have with EDR is that conventional EDR solutions take a long time to deploy. With industry-leading EDRs taking up to 90 days to deploy and set up, MSPs and their clients end up waiting longer to see a return on investment (ROI). In many cases, the initial setup of EDR is so resource-intensive that the cost and effort outweigh the immediate benefits.
When evaluating an EDR solution, consider the average deployment time and whether the time frame will work for your business. The easier an EDR is to deploy, the sooner your business will see a return on investment. Solutions that are simple to launch and implement will enable you to protect more endpoints for more clients.
3. Management
Cyberattackers never sleep, and that makes managing EDR alerts a 24/7 job. This requires technicians who can manage alerts around the clock. Do you have the staff to devote to this?
If you have only a few technicians, managing alerts through the night could be a challenge, so outsourcing endpoint security to an MDR service is a sensible option for early maturity MSPs that have only a few technicians. MDR can help alleviate the burden of managing alerts and investigating and remediating incidents. With endpoint security handled by MDR 24/7, early maturity MSPs can focus on other objectives, such as enhancing service quality.
Additionally, many MSPs use MDR services as a stand in to handle the night shifts or when additional help is needed.
4. Complexity
Consider whether the EDR solutions you are evaluating are overly complex — most traditional solutions are. When evaluating solution, determine whether it is truly MSP friendly. If it is overly complex and requires highly skilled security staff, then the answer is “no.”
Unlike enterprise-grade products, solutions that are designed for MSPs lower the barrier to entry typically associated with EDR, enabling MSPs of all sizes to offer EDR services.
5. AI-enabled capabilities
AI-enabled capabilities found in many of today’s EDR products can simplify things even further.
For example, Acronis Advanced Security + EDR provides AI-based attack summaries to help technicians understand attacks — saving time and aiding in rapid response and remediation.
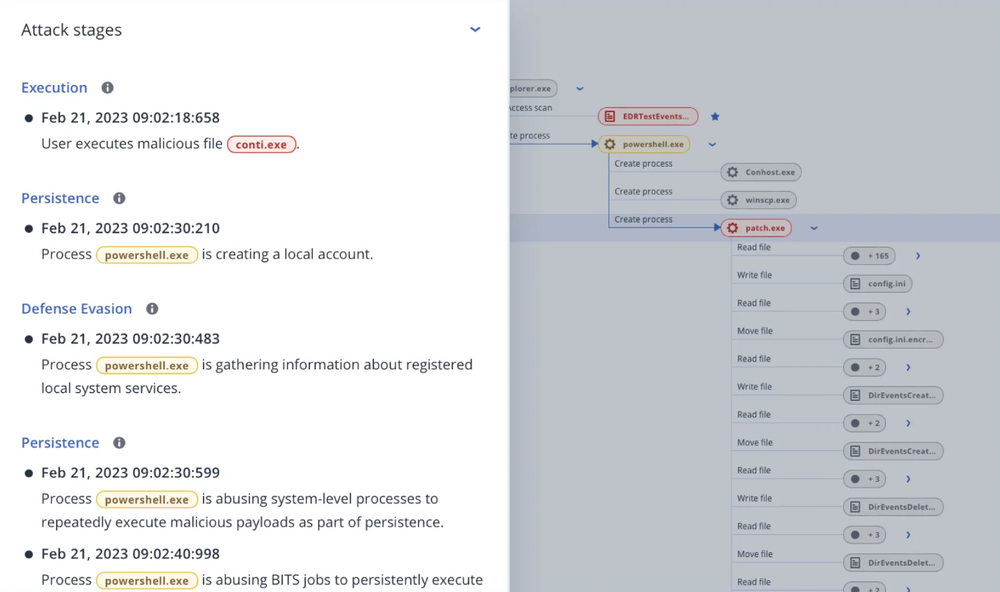
Additionally, generative AI can accelerate the decision-making process by providing context into incidents with concise incident summaries. Security Copilot in Acronis Advanced Security + XDR provides a natural language, generative AI-assisted chat function that provides a detailed, easy-to-understand summary when prompted.
This feature can also be helpful in guiding response actions.
With AI-enabled solutions, you enable existing technicians to investigate and remediate threats faster without wasting precious time trying to understand the incident and how to remediate it from scratch.
6. Maturity stage
Where is your business in terms of maturity? If you’re in the very early stages, then MDR might be the right option — using it as your primary service to deliver endpoint protection. In this case, you fork up more budget to outsource endpoint protection full time while liberating technicians to handle easier tasks. The goal is to complete more tasks, keep headcount lean and have happier clients.
If you’re further along in maturity, you could use both MDR and EDR simultaneously. MDR can be a stepping stone that supports your existing technicians who manage EDR. For instance, let’s say you assign the protection of every 350 endpoints to one technician. To justify hiring and onboarding a new technician, you must have enough client endpoints to offset hiring costs. In the meantime, you use MDR until you build enough clients to support adding to your headcount. Once the new technician onboards, you turn off MDR and switch back to EDR. By doing so, you get better control of expenses while mitigating the risk of financial loss.
7. Pricing models
A vendor’s pricing model is a critical factor to consider before committing to a solution or service. There are some downsides with popular models such as subscription-based, perpetual licensing and tiered pricing that can inadvertently lock you over time into paying for tools that you do not use.
Keep in mind your current and future needs. Maintenance, support and implementation are all considerations that influence costs. Evaluating and choosing the pricing model that is right for the business will pay dividends later.
With many different pricing models on the table, there is one that cost-conscious MSPs should consider: consumption-based pricing. This pricing model offers the scalability necessary to expand services according to what is used. One common mistake that MSPs make is that they neglect the importance of scalable solutions. The security needs of clients continuously change as cyberattackers shift their focus and techniques, and consumption-based pricing enables you to only pay for what you require and, crucially, to avoid wasting money on services that are not used.
The art of scaling with EDR- and MDR-based services
Strategically, MSPs can leverage both EDR and MDR to balance their resources and growth objectives. This ensures that you maintain comprehensive endpoint protection while managing costs and preparing for future expansion. Ultimately, a well-thought-out strategy that incorporates both EDR and MDR can help MSPs deliver robust security services tailored to each stage of your MSP business. The decision you make should be guided by the several aforementioned practical factors that take into consideration the unique needs and direction of your business.

About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.