As a managed service provider (MSP), your clients may ask you what type of software they need to ensure their employees’ devices and other network endpoints are protected. This article discusses what endpoint protection or endpoint security is and what you need to do to ensure the safety and security of your clients’ network endpoints and the data they contain.
What is endpoint protection?

An endpoint is any device or node that is the entry point for communicating over a local- or wide- area network (LAN/WAN). Computers, laptops, mobile phones, printers, servers, virtual environments, ATM machines, medical devices, and Internet of Things (IoT) devices are examples of endpoints. The modern definition of an endpoint includes any device that sits outside the corporate firewall but can connect to the corporate network. Expanding the definition of endpoints to include those devices outside the corporate firewall has developed because of the adoption of bring your own device (BYOD) policies and the mass migration to remote work.
Endpoint protection (EPP) solutions secure a business’ endpoints from cyber threats/attacks, including malware threats, zero-day attacks, and ransomware. EPP solutions can either be on-premises or cloud-based and allow you to continuously monitor and collect your clients’ data and take remote remediation actions on an endpoint that is within or outside of their corporate network.
How does endpoint protection work?
Cloud-based EPPs store their database of cyber threat information in the cloud. The system administrator uses a centralized console to assign client software and security policies to each endpoint. The client software can be delivered via software as a service (SaaS) or installed directly on the device.
Who needs endpoint protection?
Endpoint protection provides management and protection of a business’ endpoints and data from cyberattacks. If an employee is remotely using a computer, laptop, or mobile phone for work, the device can hold their company’s sensitive information. The device can hold the employee’s personal and sensitive information as well. If the endpoint is attacked, an EPP can stop the attack.
By centrally protecting the endpoint, you also protect your client’s network and other endpoints from malware threats. Once a hacker infiltrates one endpoint, they can access and deliver a payload into the corporate network and other network endpoints to steal, corrupt, delete, or otherwise harm a business’ sensitive data and systems.
For these reasons, any business of any size needs endpoint protection but endpoint protection, in and of itself, is not the “be all and end all.”
While endpoint protection protects endpoints from cyberattacks and threats, it does not protect a business’ endpoints from other unforeseen events that cause data loss or corruption, such as deletion or corruption of files caused by user errors, software errors, hardware/software upgrades, and human-made and natural disasters.
Acronis Cyber Protect Cloud provides more than endpoint protection
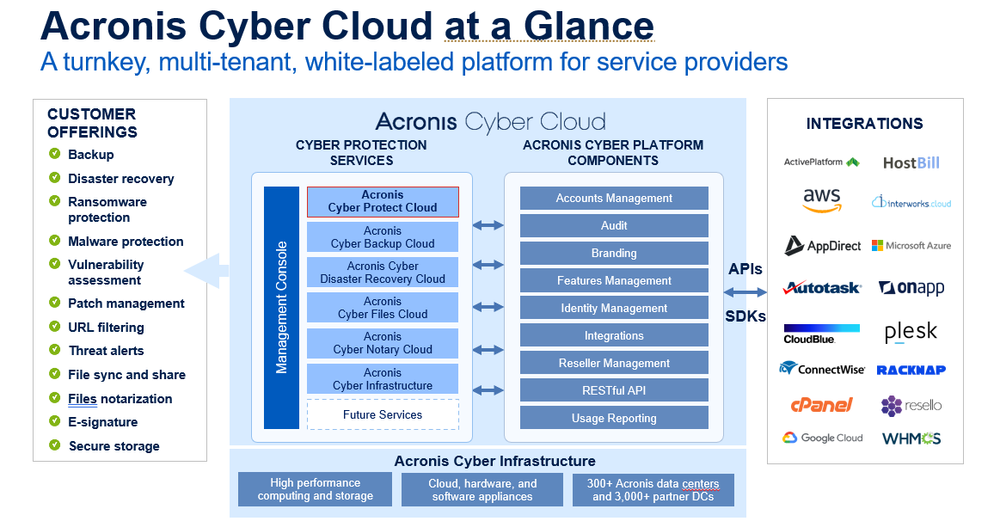
Acronis Cyber Protect Cloud is a one-of-a-kind solution that unites backup, disaster recovery, next-generation, AI (artificial intelligence)-based anti-malware, antivirus, endpoint protection management, and remediation and investigation capabilities in one solution. This eliminates the need for you to provide a patchwork of system and endpoint protection tools, which typically create gaps in your client’s defenses. Instead, Acronis Cyber Protect Cloud offers unmatched integration and automation to reduce complexity, increase your productivity, and decrease operating costs. Some of its unique features include:
- A single console and single agent that are fully integrated and automated
- Anti-malware updates and patching during recovery
- Auto-adjust patching, scanning, and backup policies based on threat landscape alerts
- Automatic back up of endpoints before installing patches to enable easy recovery in case a patch renders the system unstable
- Forensic backup that allows you to collect digital evidence data, include them in disk-level backups that are stored in a secure place to protect them from cyber threats, and use them for future investigations
- The ability to offload endpoints and enable more aggressive scans and vulnerability assessments in backups
- Continuous Data Protection that ensures you will not lose data changes made between scheduled backups
- Next- generation anti-malware, which uses machine learning/AI-based technologies to prevent emerging/new/unknown malware
- Automated app whitelisting – including customer apps – from backups
- A data protection map that ensures tracking data distribution across the machines, monitoring the protection status of files, and using the collected data as the basis for compliance reports
- Fast and reliable recovery of your applications, systems, and data on any device, from any incident
- Remote work security capabilities and prioritized patching and protection for collaboration apps
- And more! (See Figure 1 above.)
With Acronis Cyber Protect Cloud, you can provide multiple layers of protection for your clients’ endpoints to ensure your clients’ data, applications, and systems are always available and protected, no matter what happens.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



