
Modern cyberthreats require businesses to safeguard their data with all they've got. As hybrid work environments and BYOD make it challenging for security teams to protect every potential entry point on a company network, every business should devise a detection and response strategy and follow it to the letter to mitigate risks, ensure revenue, and protect its brand image.
This article will explore three main detection and response approaches and compare them (EDR vs. XDR vs. MDR), so you can choose the best strategy for your company's needs.
What is EDR?
EDR stands for "endpoint detection and response." These technologies aim to secure network-connected endpoint systems (PCs, laptops, IoT, servers, etc.) against cyberthreats that have circumvented traditional security measures (basic antivirus).
EDR defined
As a next-gen solution against sophisticated threats, EDR typically includes the following features:
- Endpoint monitoring
The rise of hybrid work environments leads to a broader attack surface for malicious actors. Attackers would typically target endpoints outside the primary network to try and penetrate company defenses. EDR solutions monitor endpoints, collect data about the protected system, analyze it for suspicious behavior, detect potential threats and send alerts to your security team.
- Anomaly detection (and AI)
EDR tools integrate machine learning to ease threat intelligence via anomaly detection and artificial intelligence. EDR systems can analyze enormous amounts of data, outline malicious patterns and trends, and pinpoint potential intrusion attempts and other vulnerability issues across the network. Advanced EDR technologies can detect local threats on a specified level and recognize an attack on their customers via cloud-based, global anomaly detection features.
- Active endpoint protection
Upon detection, an EDR tool can automatically react to a threat — delete malware, counter ongoing attacks, or isolate the entire system from the vulnerable endpoint to prevent the malware from spreading.
- Threat investigation and threat hunting
Threat investigation is crucial to incident response and determining the root cause and scope of an infection in the protected system. EDR performs log collection and data analytics to provide security teams with a comprehensive report.
- Endpoint log management
Endpoints typically generate log files; however, log data won't be helpful if left unexplored. EDR can perform automatic log management to make critical log data available to the responsible data analytics system and the teams accountable.
What is extended detection and response (XDR)?
Traditional EDR is often seen as limited cybersecurity solution focused on a single aspect within the company network. On the other hand, XDR comprises detection and response capabilities for endpoints, cloud services (single platform), and networks. A comprehensive cybersecurity strategy can benefit significantly from XDR, especially in complex, hybrid work environments. Companies can often request XDR as part of a software-as-a-service (SaaS) offering.
What is managed detection and response (MDR)?
EDR and XDR are useful across an organization's entire network. However, both approaches generate enormous data volumes that require thorough analysis. Even highly skilled cybersecurity professionals would put in great time and effort to review all telemetry data. To counter the cumbersome and tiring process, companies can turn to MDR.
Managed detection and response (MDR) is not a stand-alone technology but rather a managed service that comprises the benefits of EDR and XDR into a convenient solution. MDR can help with data search investigation and threat hunting, ingestion analysis and workflows across the network, reduce alert fatigue, enhance threat-focused event analysis, and more.
MDR negates the need to hire outside cybersecurity experts. Given that an experienced third-party provider created the solution, it can easily procure alert triage to distinguish false positives from actual threats. Most often, MDR offers a comprehensive approach to traditional detection and response functions. It can also accelerate multi-domain threat analysis and benefit DNS firewalls, cloud monitoring, network sensors, and more to safeguard the company's IT infrastructure.
What is the difference between EDR vs. MDR vs. XDR?
EDR is central to every security plan. EDR threat detection solutions focus on monitoring and securing endpoints on a network. EDR relies on sensors (or software agents) installed on all endpoints to gather data and send it to a centralized repository to enable comprehensive analysis. When a service manages endpoint security, we can call that MDR. The service focuses on mitigating, eliminating, and remediating threats via an experienced security team. XDR enhanced EDR capabilities to protect all vulnerable entry points for attackers (not only endpoints).
An XDR solution gathers diverse multidomain security telemetry, streamlining security data ingestion, analysis and workflows across an organization's entire security stack, enhancing visibility across the enterprise. This way, XDR shines brightest around hidden and advanced threats to enable a unified response. If purchased as a managed service, XDR will allow access to highly-skilled specialized talent, top-tier threat intelligence, and analytics.
MDR vs. EDR vs. XDR: Summary
General endpoint detection and response tools (EDR) monitor endpoints in real time using behavioral analysis (IOCs and IOAs), rely on a threat database and graphing, network containment, and present security teams with remediation recommendations.
MDR provides the same capabilities as EDR but offers 24/7 managed services to monitor endpoints and eliminate and remediate threats.
XDR offers threat-centric network traffic analysis solutions. It streamlines security data ingestion from various sources, dramatically improves threat visibility, accelerates threat analysis, and reduces threat risk. XDR's enhanced threat visibility accelerates security operations, enables in-depth domain threat analysis investigation, and provides teams with siloed security tools unifying your company's entire cyber security strategy.
EDR benefits
An endpoint detection and response solution is the first step toward a healthier company network. Below are the three primary benefits of the approach.
Quick threat identification and remediation
EDR can quickly identify and counter threats that have circumvented traditional antivirus. EDR tools rely on automation to continuously monitor endpoint activity, identify suspicious behavior in real time, detect malicious threats, and isolate and deflect an attack from both internal and external sources.
Proactive threat hunting
Traditional antivirus typically reacts to threats after they've attacked the system. EDR proactively hunts new threats to find ill-intended actors within your environment and denies an attack before it occurs.
Security experts' assistance
In addition to automation, EDR tools allow organizations to analyze security risks at a human level. With a managed EDR solution, your company can benefit from the support of a dedicated security operations center (SOC) to manage all EDR tools, review incidents, and design an improved detection and response strategy.
XDR benefits
Extended detection and response (XDR) solutions can transform your cyber security strategy. A robust XDR tool covers a greater volume of potential vulnerabilities compared to EDR. XDR can:
Enhance advanced threat detection
While, for example, EDR solutions monitor endpoints to detect threats, XDR includes websites, DNS, URL, SQL, etc., to monitor all traffic on the entire network, detect anomalies, and block them instantly.
Provide multidevice and network protection
As mentioned, XDR doesn't focus solely on endpoints; it seeks threats across the entire network traffic to identify risks in all potential entry points. XDR covers all on-premises, off-site devices, and cloud-based environments to comprise your entire attack surface and negate all potential threats.
Analyze multi-source data easily
Streamlining security analysis investigation is a primary XDR detection and response capability. XDR enables threat hunting across multi-domain telemetry to rapidly remediate advanced threats.
Boost productivity
XDR can monitor and manage threats across the entire enterprise, accelerate security operations, and save your teams tremendous time and effort, especially if you go for a robust XDR tool that presents a centralized dashboard to manage all XDR features.
Enable rapid incident response and recovery and reduce costs
XDR can isolate and mitigate an incident as quickly as possible. This minimizes downtime and the risk of other areas being compromised after the initial attack. Additionally, having an XDR solution translates to multitool access. Not having to purchase overlapping services can reduce costs and optimize your resource spending.
MDR benefits
As MDR manages endpoint security technologies automatically, your IT teams will have more time to focus on business-related projects. Moreover, MDR can help your company with the following:
Event analysis
MDR can analyze billions of security events, sift through false positives, identify genuine threats, and combine machine learning with human analysis and management to counter attacks.
Alert triage
MDR can help prioritize cyber security activities and focus on the most pressing issues first. It also aids vulnerability management as it proactively addresses vulnerabilities to reduce your company's threat surface.
Threat hunting and remediation
A sophisticated MDR solution can help repair, restore and remediate your system following an incident, minimizing damage and reducing recovery times.
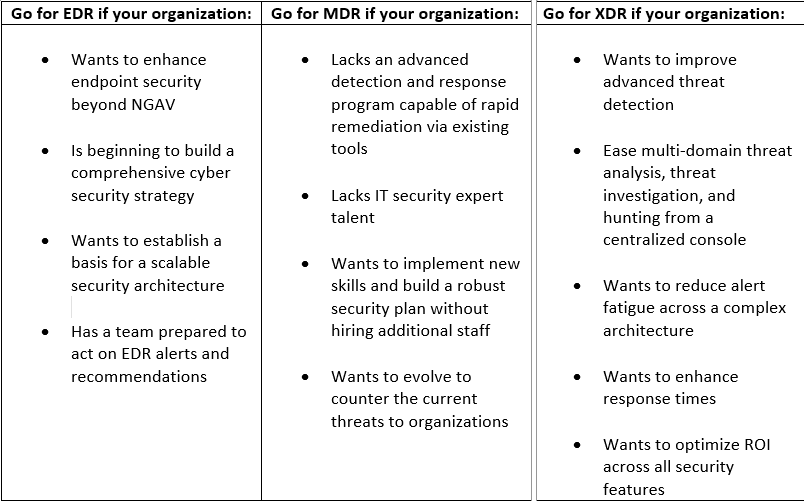
XDR vs. MDR vs. EDR: Which one is right for your business?
Every organization has unique needs. While securing your data is critical, it's essential to choose a cybersecurity tool that suits your budget and goals best.
The XDR vs. MDR vs. EDR diversification requires businesses to do their due diligence. It's not enough to type your search query and hit enter. Take the time to inspect different aspects of all approaches, and only then select the most suitable one.
Acronis Advanced Security + Endpoint Detection and Response (EDR)
Companies of all sizes need advanced security controls to counter today's cyberthreats. However, most advanced EDR and XDR solutions are highly complex and costly. With Acronis Advanced Security + EDR, businesses can rapidly detect, remediate, and investigate advanced attacks, dramatically improving MTTR, time-to-value, and lower costs via an integrated all-in-one MSP-class platform. With Acronis, you can unlock rapid analysis, MI-based guided attack interpretations, increase visibility across MITRE ATT&CK®, reduce false positives, and focus on true indicators-of-compromise (IoCs). In addition, you will benefit from comprehensive threat response tools across the NIST Cyber Security Framework — Identify, Protect, Detect, Respond, and Recover from sophisticated threats with ease, without the need for an extensive security team.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



