You are on United States website. Change region to view location-specific content:
Global
English
Select another region
Choose region and language
- Americas
- Asia-Pacific
- Europe, Middle East and Africa
- Worldwide

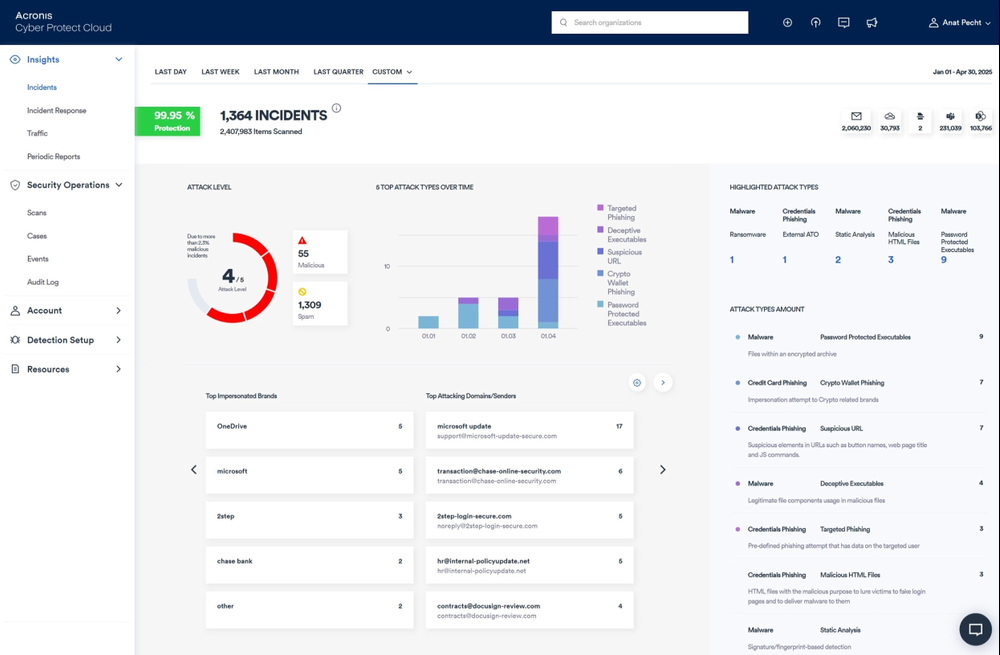
Email is the biggest threat vector for your clients - neutralize it and minimize risks in email communication with a unique technology. Email Security enables you to offer more thorough cyber protection without increasing your management burden.
Replace the inefficient security stack of sandboxes and content disarm and reconstruction technologies (CDRs) with a multi-layered email security solution for lightning-fast detection that’s easy to deploy and manage.
Acronis operates a global network of cloud data centers designed to deliver a high level of safety, security, and accessibility.
Clients are increasingly dissatisfied with the native defense capabilities of Microsoft 365, as they are slow in detection and unable to prevent more advanced attack techniques. Email Security ensures all email-borne threats are blocked in seconds.
Detection speed | < 30 sec | 5-20 min |
Detection accuracy | Best-in-class | Good |
Threat coverage | Best-in-class | Good |
Detection of malicious URLs | Best-in-class | Average |
Detection of zero-days | Best-in-class | Limited |
Prevention of APTs | Included | N/A |
Prevention of ATO | Included | Add-on |
Anti-evasion | Included | Below average |
Incident response services | Included | N/A |

Protect clients’ collaboration apps, increasingly exploited in attacks with prioritized patching and exploit prevention. Leverage Acronis Cyber Protect Cloud, integrating backup and disaster recovery, next-generation anti-malware, and cyber protection management.





Looking for help?
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.