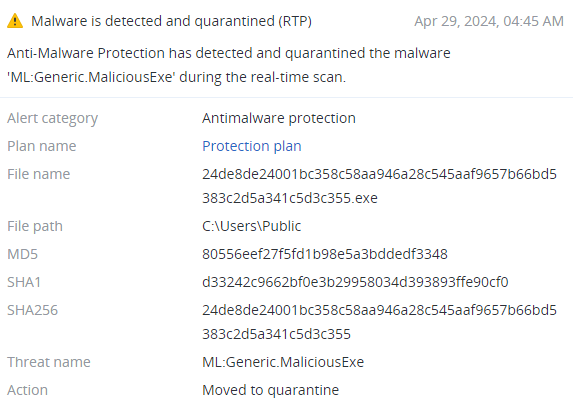
Summary
● Ransomware-as-a-service group.
● Reviewed sample is a PE64 file written in Rust.
● Requires username and password as command line arguments to start execution.
● Prevents backup and recovery.
● Terminates processes and services.
● Encrypts files using AES and RSA ciphers.
Introduction
Hunters International ransomware was first spotted in October 2023. While it shares many similarities with Hive ransomware, it is not a rebrand, as threat actors said. After the FBI defaced the Hive ransomware leak site, Hunters International sold older versions of their source code written in C and Golang, as well as their website.
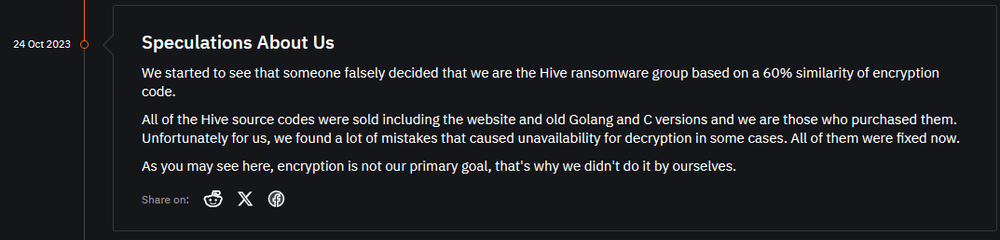
As Hunters International threat actors said, they took Hive encryption logic and fixed several issues that sometimes prevented file decryption. Similar to Hive, Hunters International works as ransomware as a service (RaaS) and besides encryption, it also exfiltrates victim data.
Technical details
Overview
The analyzed sample is a PE64 file, written in Rust and designed as a GUI application.
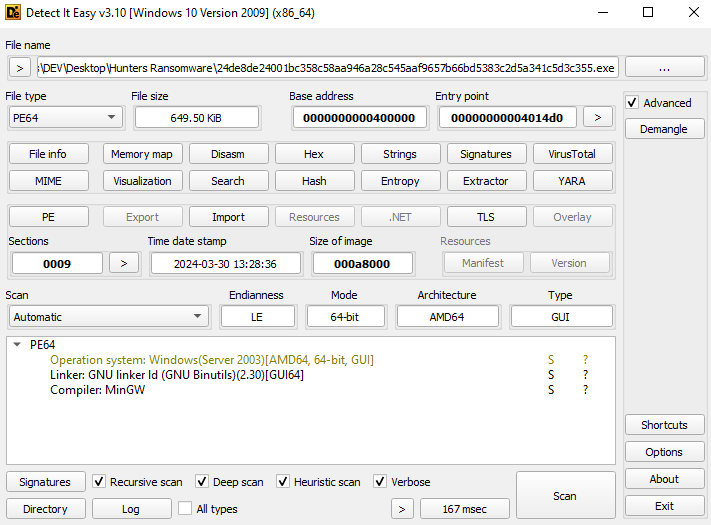
Execution
At the start of execution, the sample checks command line arguments. If no arguments were provided, execution would be immediately terminated. To begin execution, the ‘-c’ argument must be passed with credentials in the next format “-c username:password”. The username and password will later be written to the ransom note file as credentials to the threat actor chat site. Additionally, the folder path to encrypt can be given after ‘-c’ argument.
After parsing commands, the sample starts creating encryption threads using Tokio asynchronous runtime for Rust.
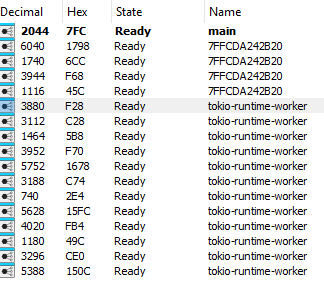
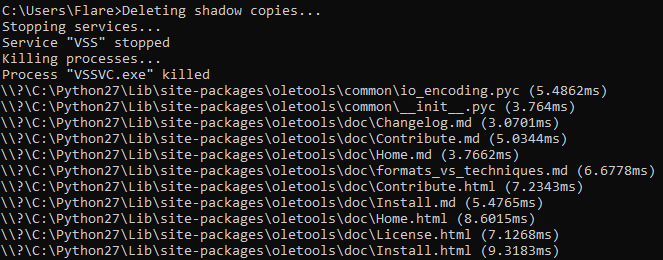
Next, it executes some commands to prevent backup and recovery:
vssadmin.exe delete shadows /all /quiet
wmic.exe shadowcopy delete
wbadmin.exe delete systemstatebackup
wbadmin.exe delete catalog-quiet
bcedit.exe /set {default} recoveryenabled No
bcedit.exe /set {default} bootstatuspolicy ignoreallfailures
wbadmin.exe delete systemstatebackup -keepVersion:3
After obtaining ‘SE_DEBUG’ privilege, the sample takes a snapshot of all running processes using ‘CreateToolhelp32Snapshot;’ it then searches for ‘winlogon.exe’ process. After it has been found, the malware opens it and impersonates the token to escalate privileges and bypass access control.
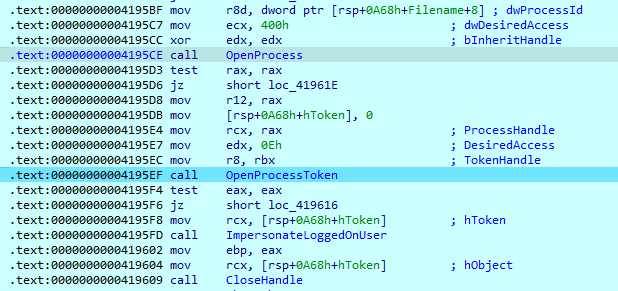
The sample has a list that contains processes and services names:
firefox, memtas, mepocs, msmq, excel, backup, mspub, mssql, mysql, notepad, ocomm, ocssd, onenote, oracle, outlook, powerpnt, sql, sqbcoreservice, steam, svc$, thebat, thunderbird, veeam, visio, vmm, vmwp, vss, vssvc winword, wordpad, xfssvccon, dbsnmp, encsvc, agntsvc, bdeng50, dbsnmp
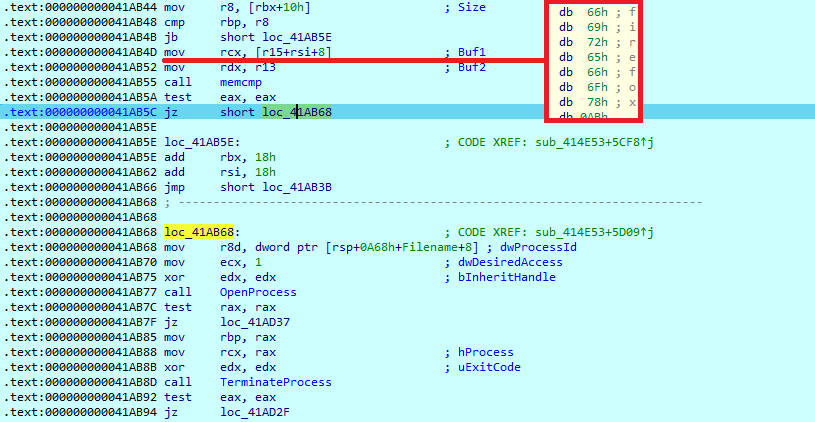
This list is used in two functions. The first takes a snapshot of all running processes, and then using ‘Process32First’ and ‘Process32Next,’ loads the result to the Buf2 variable. It then enters a loop, where the found process name is compared with each item from the saved list and loaded to the Buf1 variable. If the found process name matches the list, it will be terminated.
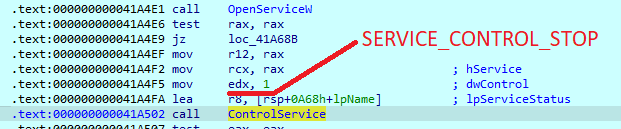
The second function uses ‘OpenSCManagerW’ import to obtain all active service names on the system with ‘EnumServicesStatusW’ function. The sample then compares the list with its own list. When the match is found, the sample uses the ‘EnumDependentServicesA’ function to find all dependent services. All found services will be terminated.
While GUI applications don't have a console by default, the sample uses the ‘AttachConsole’ function to get the handle of the parent process console and print output to the parent process console. Besides executed commands and stopped processes, it outputs each processed file alongside with the time it took to encrypt it.
File encryption
‘GetLogicalDrivesStringsW’ is used to obtain all available drives on the system. Obtained names will be passed to the ‘GetDriveType’ function to discover their types. If the result value is less than 2(0 = DRIVE_UNKNOWN and 1 = DRIVE_NO_ROOT_DIR), the names will be skipped during encryption.
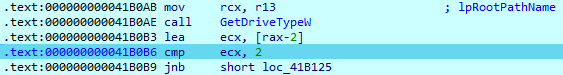
Additionally, if network shares are present in the system, they also will be encrypted. All found drives will be passed to the loop, which uses ‘FindFirstFileW’ and ‘FindNextFileW’ functions. During encryption, the sample skips many different files and folders, mostly consisting of system files and programs, so as not to disrupt system workability and to allow contact with the threat actor.
File names that are excluded from encryption:
Contact US.txt, autorun.inf, bootfont.bin, boot.ini, bootsect.bak, desktop.ini, iconcache.db, ntldr, NTUSER.DAT, NTUSER.DAT.LOG, Ntuser.ini, thumbs.db
Directory names that will be skipped:
Windows, Program Files, Program Files (x86), Program Data, $Recycle.Bin, All Users, Default, Google, System Volume Information, Boot, Intel, Internet Explorer, PerfLogs
Files extensions that must be skipped:
386, adv, ani, bat, bin, cab, cmd, com, cpl, cur, deskthemepack, diagcab, diagcfg, diagpkg, dll, drv, exe, hlp, hta, icl, icns, ico, ics, idx, key, ldf, lnk, lock, mod, mpa, msc, msi, msp, msstyles, msu, nls, nomedia, ocx, pdb, prf, ps1, rom, rtp, scr, shs, spl, sys, theme, themepack, tmp, wpx
To encrypt file content, Hunters International uses AES cipher. Each thread generates encryption keys using the ‘BCryptGenRandom’ function. Encryption logic implementation uses AES hardware instructions set, which includes AESKEYGENASSIST, AESIMC, AESENC, AESENCLAST.
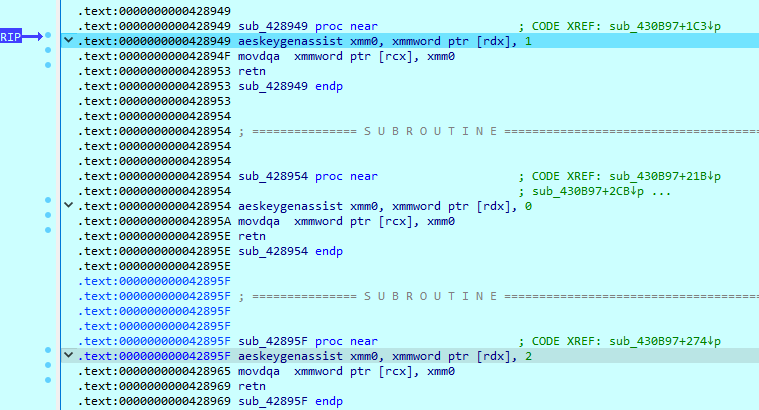
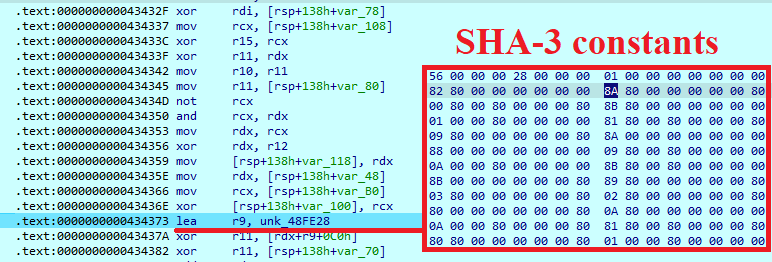
Note that in the earlier Hunters International samples, a ChaCha20-Poly1305 algorithm was used to encrypt file content. To protect encryption keys, the sample still uses RSA OAEP. It also uses a SHA3-256 Kecaak hash calculation function.
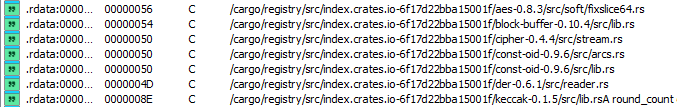
All encryption algorithms were taken from Crates.io web service for creating and searching different packages for Rust.
Encrypted AES key will be appended to the end of each file, separated with 16 bytes of ‘0x00’.
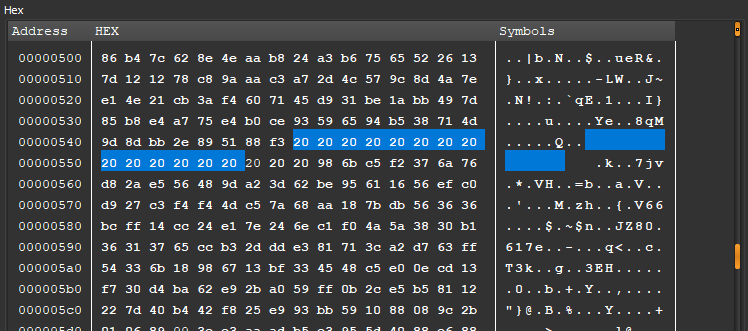
Free space eraser
After the encryption process is done, the sample creates a ‘buffer.swp’ file on each encrypted drive and continuously writes 16,384 bytes of random data until there is no free space on the disk. Even if a particular folder was passed as an argument, the sample will still wipe free space.
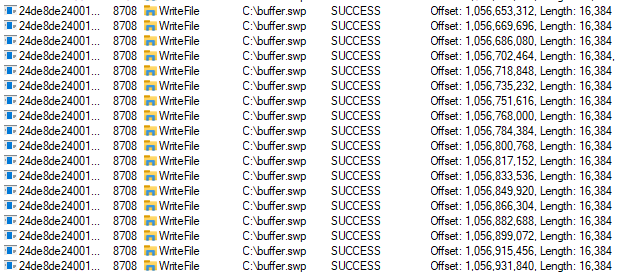
Ransom note
The ransom note is dropped in each encrypted folder on the system and automatically opened at the end of the encryption process.
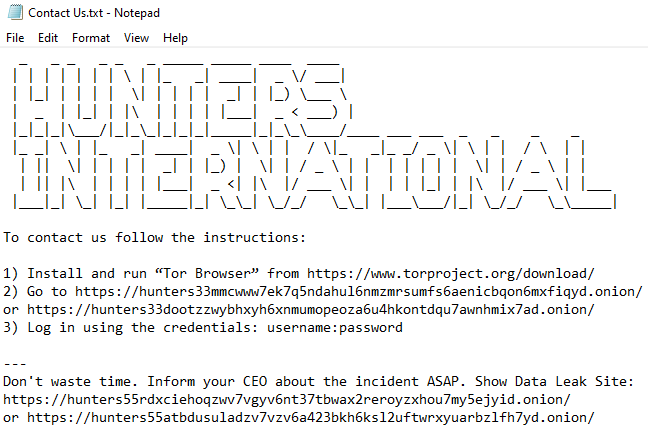
Data leak site
The data leak site contains the victims' names, their status, the deadline for paying the ransom and revenue value. Also, each company has tags that characterize data categories:
Encrypted Data, Private, Personally Identifiable Information, Financial Data, Customer Data, Passwords, Database, Technology, Governmental Data and Uncategorized.
Victims without a ‘Private’ tag also have a proof page featuring some of the encrypted and stolen files where everyone can download them.
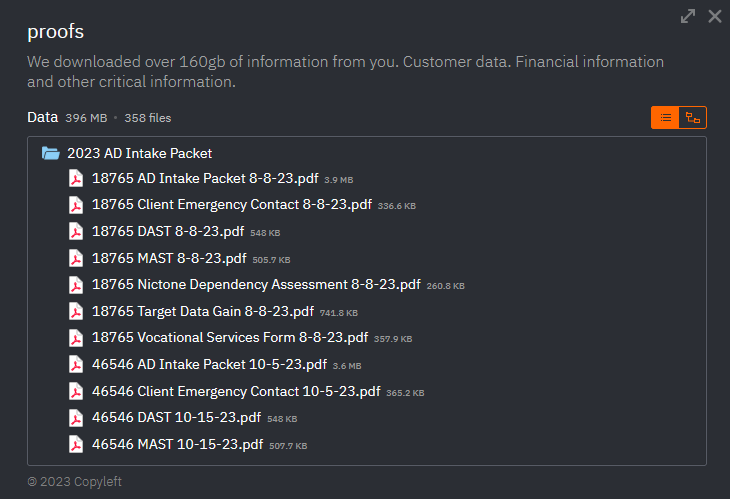
The data leak site also contains a News page. The latest post, dated April 24, 2024 contains a link to the public domain site. This site is the same data leak site, but it can be accessed from any browser.
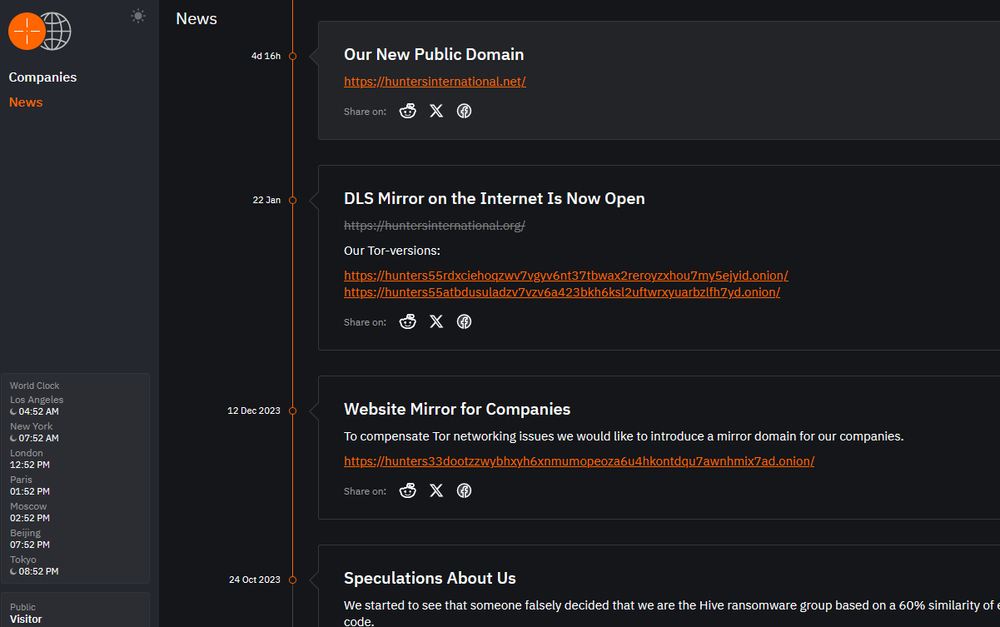
This public domain is registered in Russia with a fake identity using the NiceNIC domain service. In fact, this person (Mihail Kolesnikov) owns more than 400 domains.
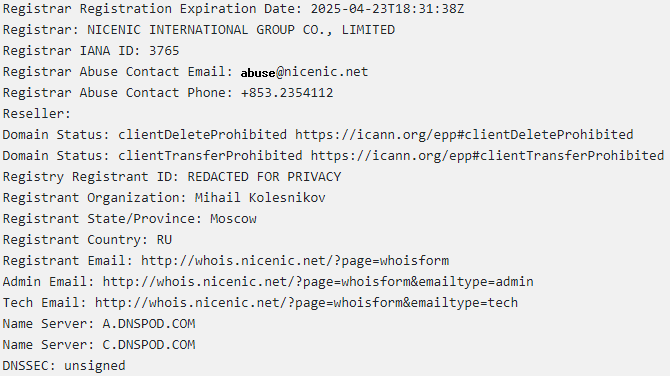
Additional links from the ransom note lead to the chat with the threat actor. It requires a login and password from the ransom note to enter.

Conclusion
Even though Hunters International group has taken the Hive ransomware source code as a base for their malware, they have improved some crucial mistakes in the encryption process. Considering that Hunters International works as ransomware as a service, we can expect a continuation and even an increasing number of attacks. Being written in Rust programming language, the malware uses different packages from the Crates.io site, which includes encryption logic, thread working and others. Combining AES and RSA ciphers makes file encryption strong, and data exfiltration is used to ensure that the victim will pay the ransom not only for decryption but also to prevent their data being sold on underground forums.