In the latest incident that illustrates the overlap of the traditional economy and infrastructure with the digital realities of modern business, one of the largest pipelines in the U.S. was forced to shut down this past weekend after being hit by a ransomware group.
Managed by Colonial Pipeline Co., the 5,500-mile pipeline runs across 14 states between Houston, TX and New York Harbor, and provides around 45% of all fuel for the U.S. East Coast.
Early reports indicate that the Colonial’s systems were compromised on Thursday, when nearly 100 gigabytes of data was stolen before being encrypted – making it the most recent ransomware attack to employ the exfiltration strategy Acronis predicted would be a major trend this year.
Details of the attack are still unfolding, but here’s what we know.
What’s happening with the pipeline?
As a precautionary measure, Colonial shut down the pipeline to prevent the infection of its business systems to compromise the operational control systems of the pipeline. Colonial is working with industry experts to restore service. In the meantime, fuel transportation has shifted to tanker trucks to ensure the fuel supply is not completely interrupted. The broader impact of the attack will depend on how long it lasts.
The latest from Colonial was a statement: "Restoring our network to normal operations is a process that requires the diligent remediation of our systems, and this takes time ... the Colonial operations team is executing a plan that involves an incremental process that will facilitate a return to service in a phased approach.”
This makes sense since industrial systems like those targeted in this attack are more complex than traditional IT systems. They need to be restarted in a precise sequence, which makes the recovery process even more cumbersome.
Precisely how long it will take is unclear, but it’s worth noting the average for complete recovery can be 16 days.
How did the attackers get into the system?
The initial attack vector that breached the company has not yet been disclosed, so it is unclear if emails, weak passwords, or unpatched software played a role in this particular incident. Each of those is a common, effective attack vector, with email being identified as the top vector in 2020.
This incident illustrates that any sector can become a victim of cybercrime, especially ransomware attacks.
Why did the attackers steal data and then encrypt it?
Like other cybersecurity analysts, the experts at our global network of Acronis Cyber Operations Protection Centers have seen an emerging trend of ransomware attackers focusing on new ways to optimize the financial return of their attacks. Instead of simply demanding a victim pay a ransom to decrypt their affected files, ransomware criminals are now stealing sensitive, proprietary data before encrypting it – and then demand payment to stop the public dissemination of that stolen information.
In fact, our CPOC analysts have found evidence of more than 2,000 companies around the world that recently suffered a data leak following a ransomware attack. We expect this shift in strategy to continue among ransomware criminals.
Who’s behind the ransomware attack?
Several media reports identified the DarkSide ransomware group as being behind the attack, which was then corroborated by the FBI.
The ransomware group itself finally confirmed its involvement, issuing a statement that it is apolitical and does not have ties to any specific governments. “Our goal is to make money, and not creating problems for society.”
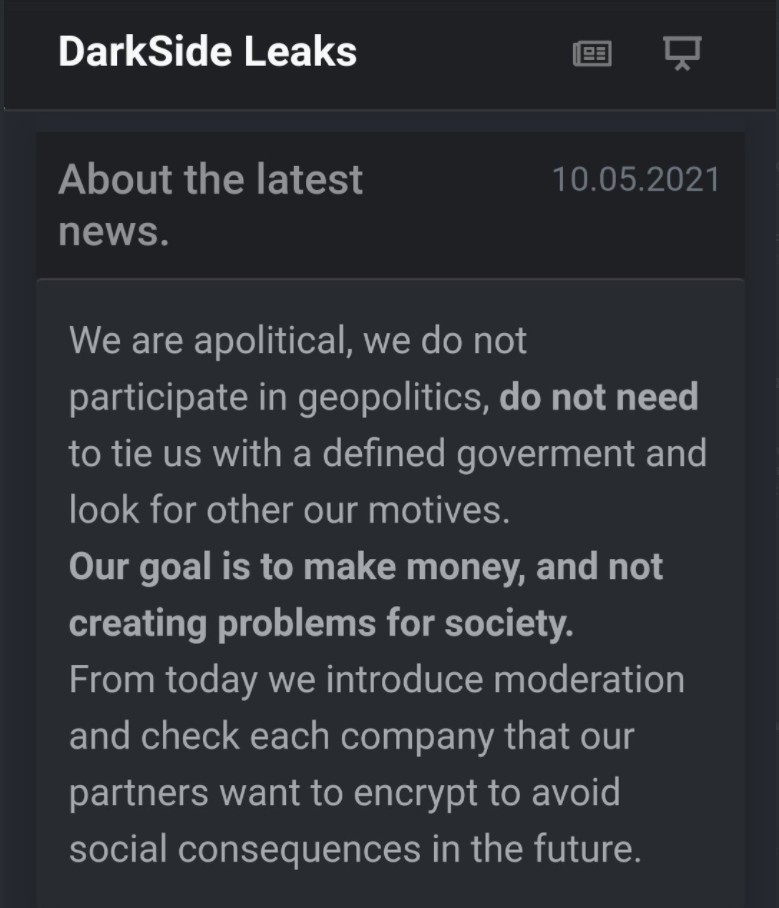
The group seems to have clarified its apolitical nature since certain nation-states increasingly turn to cyberattacks as a way to exert pressure on their rivals. Because this attack targeted a major energy infrastructure player in the U.S. and the DarkSide group is presumed to have ties to former Soviet states (since its ransomware will not attack Russian, Kazakh, and Ukrainian-speaking companies), it could be assumed that the group was working with a U.S. rival in the region.
While there is no way to be sure, the financial motive seems to match what The White House briefing revealed, when the deputy national security adviser for cyber and emerging technology reported that the incident was the result of ransomware as a service.
Final thought
The Colonial Pipeline ransomware attack is not the first to target critical infrastructure and certainly won’t be the last. While DarkSide claims it won’t target hospitals, schools, and government agencies, other ransomware groups will. And besides, DarkSide’s attacks can take down a large sector of the economy simply by targeting the right business.
Any organization that relies on its data and IT systems is vulnerable. In today’s world, that’s every business.
That is why Acronis believes every organization – whether they manage their own IT protection or they rely on a managed service provider (MSP) – should be adopting cyber protection strategies that can eliminate the risk from such attacks.



