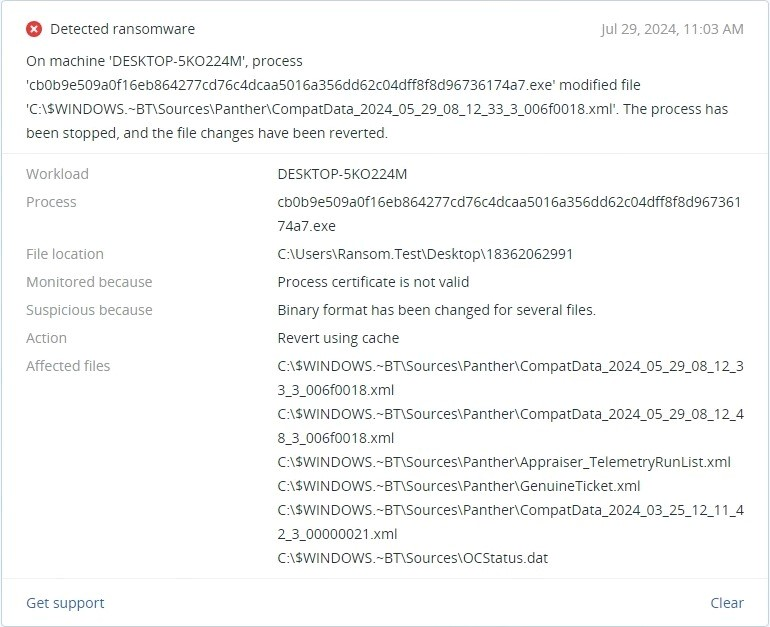
Summary
- Written in Golang
- Has multiple command line arguments
- Has compressed configuration
- Encrypts files using ChaCha20 and RSA-OAEP
- Encrypts SMB shares
- Send logs to C2 server
Introduction
Eldorado ransomware has been active from at least March 2024. It mostly targets U.S. companies, including health care, education and government sectors. An Eldorado threat actor published posts on the RAMP (Russian Anonymous Marketplace) searching for people with pentesting and network skills to conduct ransomware attacks, offering a reward of a maximum 20% of paid ransom. The malware samples examined in this article are generated using Eldorado’s internal builder and can have different variants for Linux and Windows — x32 and x64 versions. According to the threat actor’s post, the domain administrator’s password can be provided to the builder while its username will be taken from the environment.
Technical details
Overview
The analyzed sample is a PE64 file compiled with Go 1.20.14. It has a fake compilation timestamp, is not packed and doesn’t have any resources. The big sample size is normal for applications that were developed using Go.
Execution
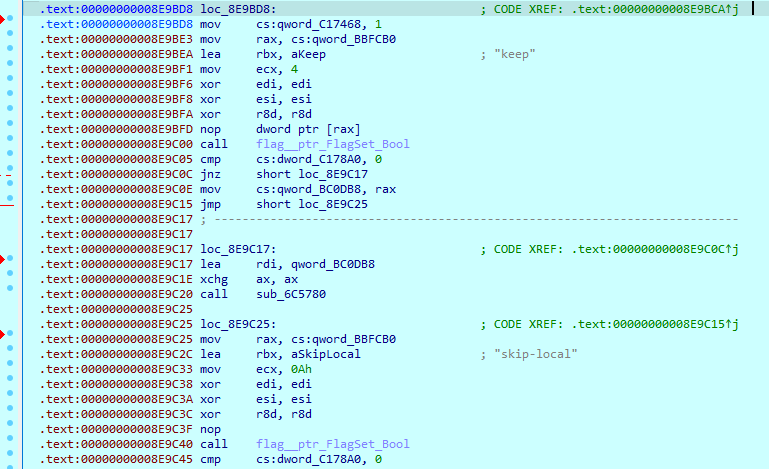
At the start of execution, Eldorado sample checks command line arguments and compares them with its own list:
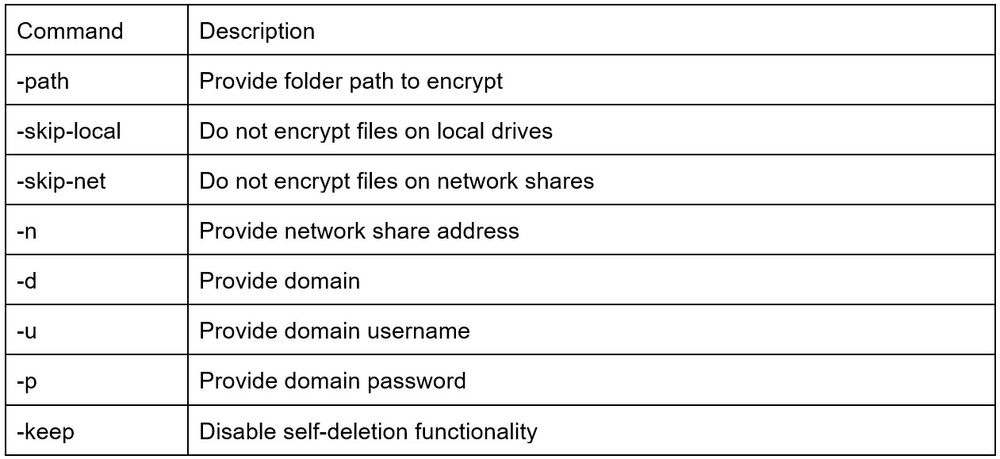
Command line argument operations are performed using the ‘flag’ package.
Executing a program without any argument will cause the program to be executed in normal mode, which includes:
- Encrypt files on all available local drives.
- Encrypt files on network shares.
- Get local IP address and try to search any shares in this network.
- Get username from configuration or find domain username on the system.
- Get password from configuration. If no password was provided, it will skip SMB shares.
Next, the sample loads some additional imports and retrieves system information, which depends on the command line arguments and configuration. This can include local IP address and domain username. After that, it loads the saved configuration and decompresses it using gZip.
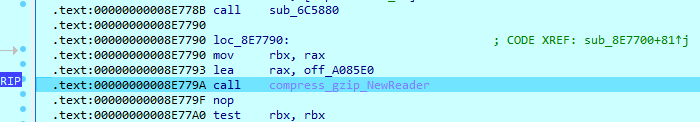
The result of its operation is a structure, which contains RSA Public Key, Ransom Note Name and Text and Domain Admin Password. All those values represent the memory addresses of correspondent data. Also, there is a size for each structure field.
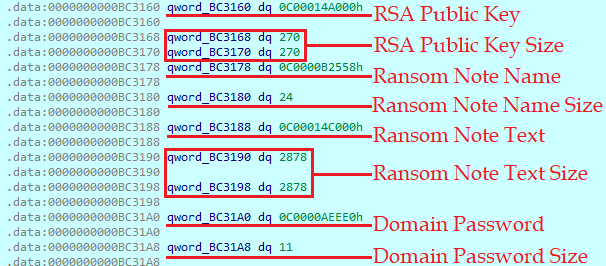
The RSA public key is then transferred to the ‘ParsePKCS1PublicKey’ function from the ‘x501’ package function alongside with 270 bytes size value.
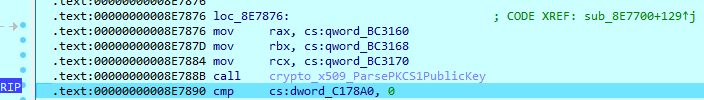
As a result, the next RSA public key is saved in the memory for file encryption.
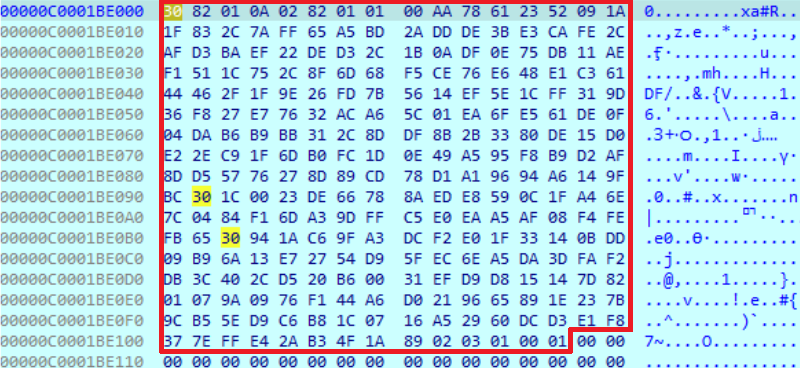
After that, the sample searches for ‘cmd’ executable path to execute the next command:

This will change the page code to 65001 value (UTF8 format) and obtain system information, which includes OS data, hardware components, network interfaces and machine domain name. After that, it starts to create encryption threads with ‘sub_6C7380’ function as a start address.
File encryption
After encryption threads are created, the malware checks for all available logical drives on the system and starts searching for appropriate files. It compares discovered files and folder names with its own list of excluded names.
Excluded folder names:
Windows, programdata, program files, program files (x86), $recycle.bin, all users, wininit, appdata, application data, local settings, boot.
Excluded extensions:
.00000001 .exe .dll .sys .msi .ini. .inf .lnk
Excluded file names:
Ntdlr, ntdetect.com, autoexec.bat, ntuser.dat, ntuser.dat.log, iconcache.db, bootsect.bak, bootfont.bin, bootmgr, thumbs.db.
To encrypt file content, Eldorado uses the ChaCha20 algorithm from the ‘crypto’ package. First, it makes two slices — 32 and 12 bytes in size.
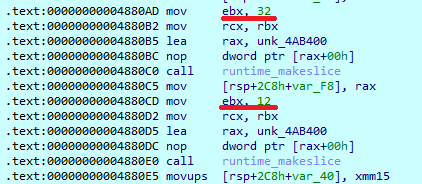
For each file, the sample writes random cryptographic values to those slices. The 32-byte slice is used to store a key, and a 12-byte slice is for nonce. Then it calls the ChaCha20 initialization function.
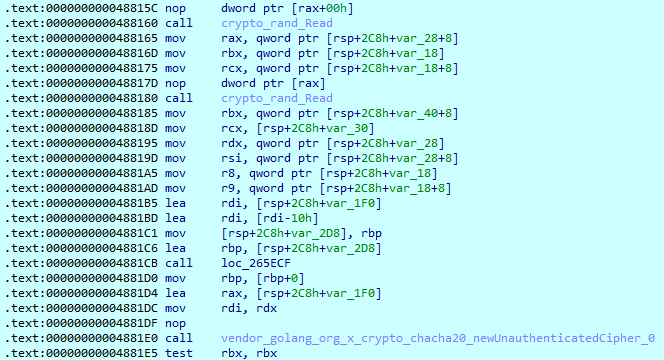
After this step, the sample reads file content. The maximum buffer size is 1,048,576 bytes. The ‘ReadAt’ function supports offsets in parameters, so if the file size is larger than this value, it will add an offset to the next read. Then it calls an encryption function.
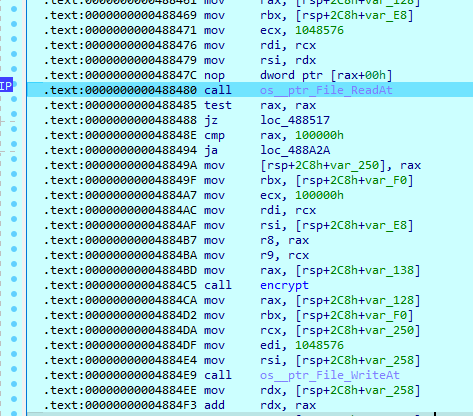
After file content is encrypted and written to the file, the sample passes key and nonce to the RSA-OAEP function that was taken from the Golang RSA package.
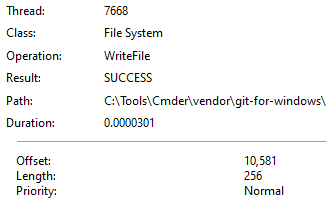
It takes the encrypted key and nonce and writes them to the end of the file. This block is always 256 bytes in size and written using the ‘WriteAt’ function, which takes an offset from the previous write procedure.
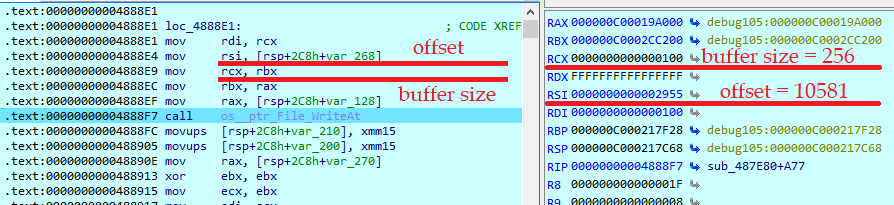
This block is appended to the end of the file without any delimiters.
Finally, it drops a ransom note to each encrypted logical drive, as well as to Documents and Desktop folders. It will then be opened with a notepad.

Console output
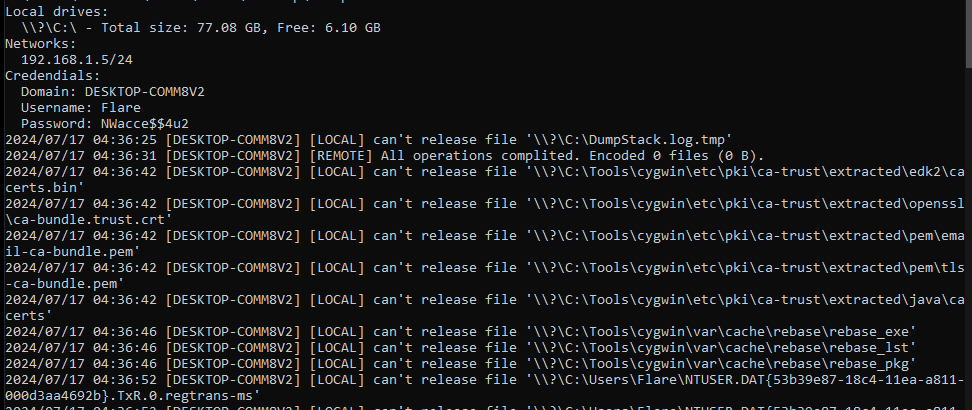
During execution, the sample outputs some data to the console. It starts printing all available drives on the system, as well as their total size and free space. Next, it prints local IP addresses and credentials such as computer name, username and password. The password is taken from configuration and considered to be an SMB password that was given to the builder during compilation. After that, the malware prints all errors that occurred during execution.
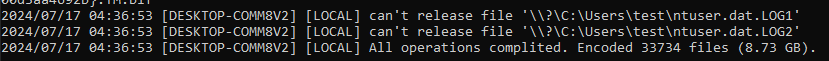
At the end of the encryption process, the sample outputs the results. This includes encrypted file count and size.
Network activity
During execution, the sample loads two saved links, which are used to communicate with the C2 server. The second string contains an invalid link.

The first string contains an IP address of the server. The sample connects to it using websockets. The second string will be split and only the ‘http://logger’ part will be used in the Origin request header. The data that is transferred to the server are logs, which includes information from console output.
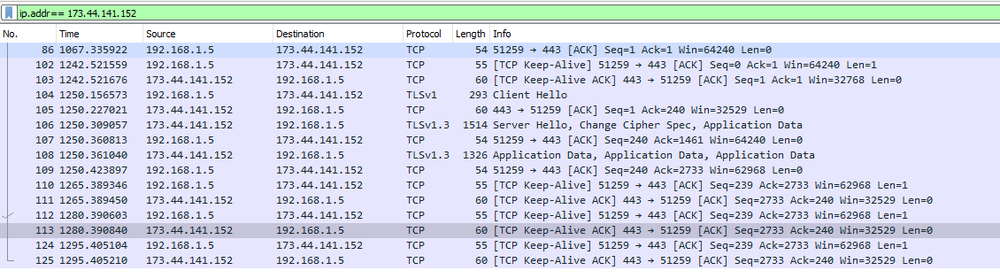
This IP address is located in the U.S. and belongs to the Eonix Corporation, a company that provides cloud business solutions.
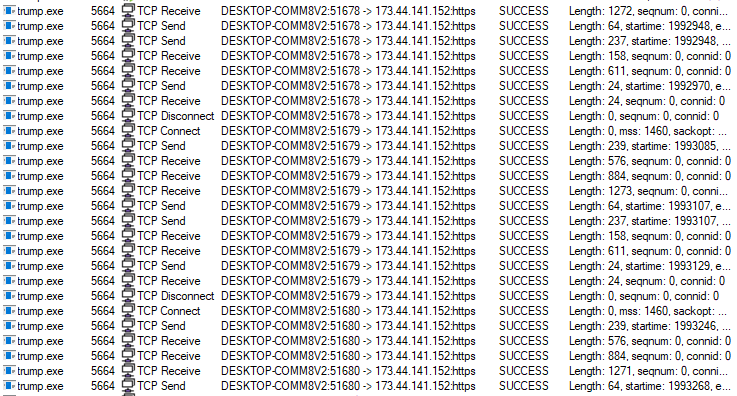
Even when the encryption process is complete, the sample continues execution and constantly reconnects to the server, changing its port number on each connection.
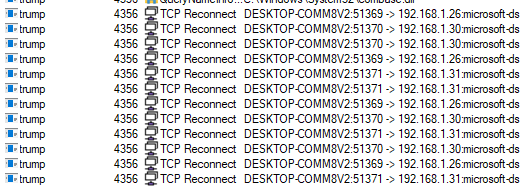
When no IP address is provided in configuration and ‘-n’ argument is missing, the sample constantly attempts to connect to all possible local IP addresses with ‘microsoft-ds’(port 455), which in Windows is used for SMB. To do this it uses a ‘go-smb2’ client implementation that allows it to connect to SMB shares, and enumerate and change files.
Ransom note
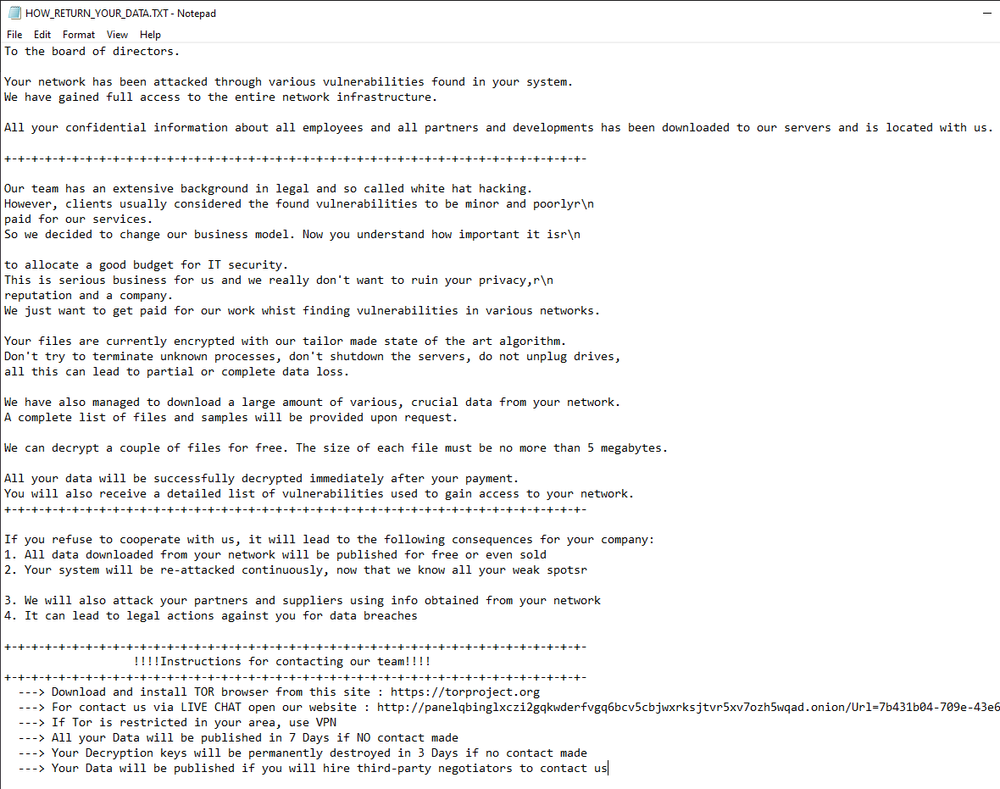
The ransom note ‘HOW_TO_RETURN_YOUR_DATA.TXT’ contains a TOR link for live chat with a threat actor, which is currently offline.
Data leak site
The data leak site contains a list of victims, each of them containing a tag that includes the company name, location and specialty.

Each victim has a separate page that contains the breach date, as well as a link to contact a threat actor, the size of stolen data and the date the data will be available for purchase.
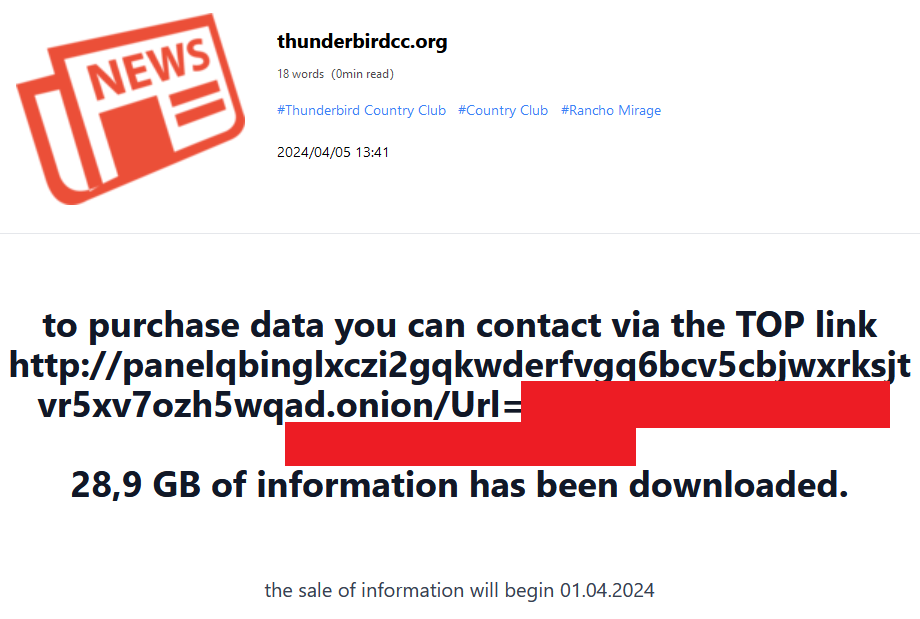
Additionally, the data leak site contains a ‘Contact’ section that contains threat actor’s email: russoschwatz@onionmail.org.
Conclusion
Despite being a new player in ransomware attacks, the Eldorado threat actor successfully carried out its operations. This group searches for affiliates and network specialists for their team on Russian-speaking underground forums. Their malware is designed for Windows and Linux systems in the Golang language, which can be configured during the building process. Besides local files, it can encrypt files on SMB shares using ChaCha20 and RSA-OAEP ciphers. The malware connects to the C2 server to send logs during the whole execution process. Based on the data leak site, they use a double extortion scheme, meaning that besides encrypting files they can also upload them to their servers, so they can sell stolen data if the victim refuses to pay the ransom.
Detected by Acronis