Summary
- Discovered on March 17, 2022
- Written in .NET
- Makes registry changes, enumerates all files and places them in two lists — system files and non-system files
- Overwrites all enumerated files with hex zeroes
- Initiates shutdown upon completion of operation by either killing the LSASS process or manually shutting the machine down
Introduction
The DoubleZero wiper — so named for its tactic of zeroing files — was first discovered on March 17, 2022 by CERT-UA (the Computer Emergency Response Team of Ukraine). The malware was designed in order to wipe out system files, non-system files and entire registry branches, and was spread by spearphishing emails with an attached ZIP that contains the malware file.
DoubleZero enumerates all local non-system files into one list, and all system files to another list. The non-system files are wiped first, in order to prevent deleting a crucial system file that might interrupt the malware’s activity.
Technical analysis
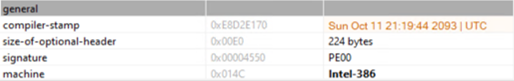
Looking at the file properties, we see that it’s an executable, and its compilation time was set to the year 2093. This is largely done by threat actors to prevent researchers from determining the real compilation time, thus making it more difficult to chain an attack to one adversary or another.
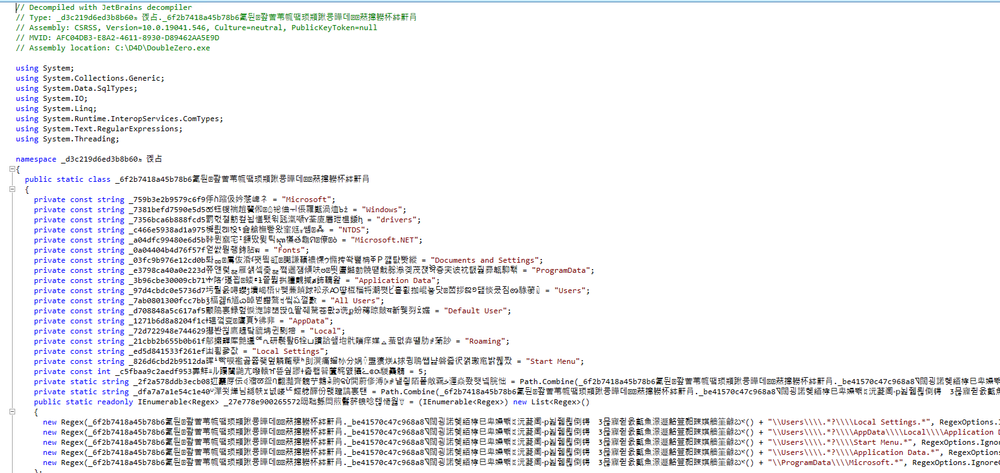
DoubleZero, although written in .NET, is obfuscated — another technique to make it difficult for researchers to inspect further.
After de-obfuscation, the wiper functionality can be divided into three parts: host reconnaissance, permission modification and wiping. This malware does not run on domain controllers, and it checks for the host’s role within the network. If the host is a domain controller, the malware terminates but does not wipe itself off the system.
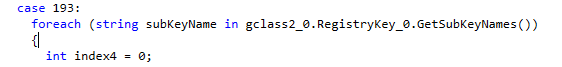
If the host is clear to run, the malware then enumerates all registry keys on the machine, along with their values.
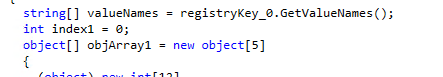
After enumeration, the wiper makes sure that it has the appropriate access rules to take control over registry keys, utilizing RegistryRights.TakeOwnership, RegistryRights.FullControl and RegistryKeyPermissionCheck.ReadWriteSubTree.
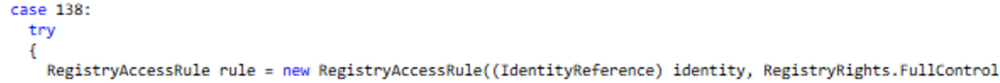
If no appropriate access rules are found, it will add a new rule do so.

With the assistance of DeleteSubKeyTree function, DoubleZero deletes the specified subkey and any child subkeys recursively, initiating the start of the wiping process.
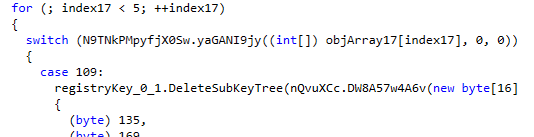
The malware then proceeds to a set list of paths to enumerate and add them to a list, as a preparatory step for the next wiping process.
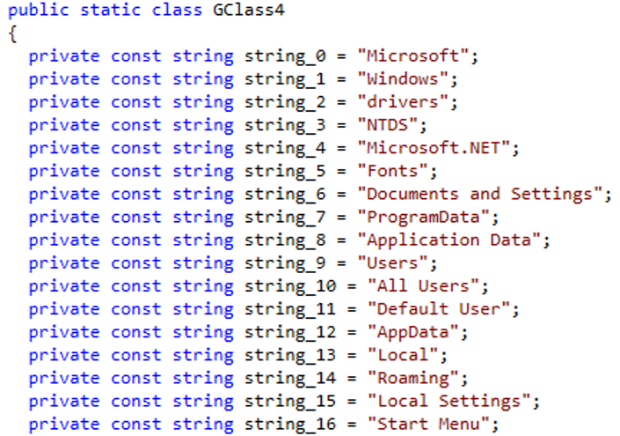
Under those paths, the wiper adds to the list the files identified within those directories, doing so recursively until there are no more files found.
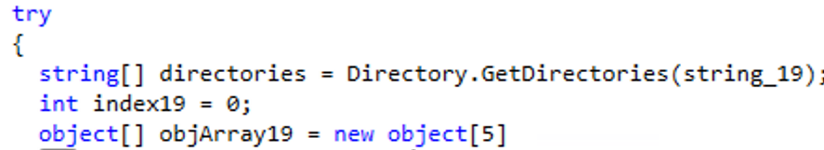
The malware contains two functions that can be used in order to corrupt the files — hence the name “DoubleZero.” It utilizes both, with no particular reasons guiding its selection of one or the other.
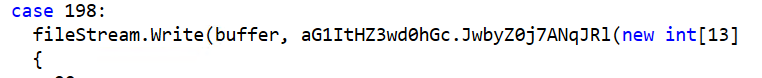
The wiper runs through all enumerated files and overwrites their contents with hex zeroes, completely corrupting them.

Non-system files are corrupted first, in order to ensure the continuity of the run. The wiper then commences corruption of the OS files, leaving the machine completely unusable.
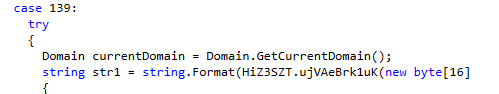
After deletion, the malware looks for a process named “lsass,” using a hard-coded string.
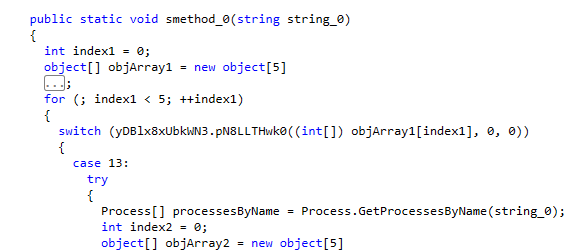
If this process is found, the wiper terminates it with the process.Kill command.
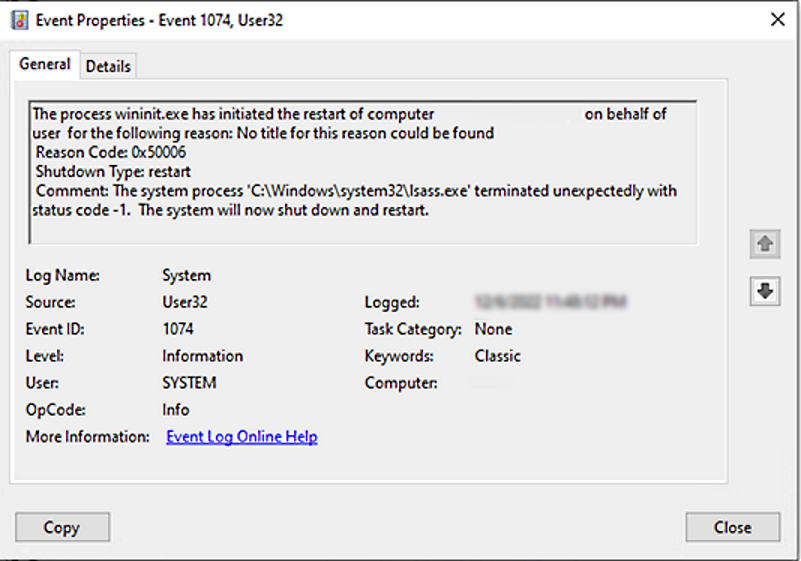
This causes the machine to shut down and restart.
Finally, DoubleZero uses the ExitWindowsEX function in another attempt to shut down the victim’s machine, in case the termination of LSASS didn’t do the trick.
After shutdown, the victim will be unable to restart their machine, as the OS is corrupted. The following error message will appear:
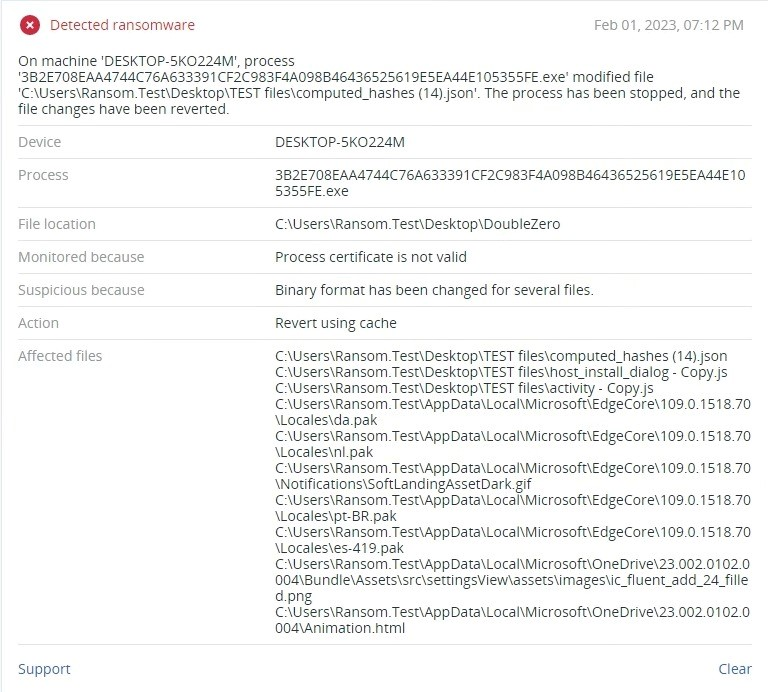
Detected by Acronis Cyber Protect
Conclusion
With the rising conflict in Ukraine, many politically motivated hacker groups have joined the cyberwar battlefield. Out of those, only two known wipers have been spotted in the wild, yet both spared domain controllers on the compromised networks. This behavior clearly points to a multi-layered destructive operation that could devastate an organization with its tools. As evidence shows, enterprise media organizations have already been victimized, which is why having a security solution that can prevent and protect from wiper attacks is very important.
Acronis Cyber Protect offers protection against both known and unknown malware threats by detecting and blocking malicious behavior, keeping your sensitive data safe from harm.



