Would you leave your wallet on the street and hope nobody will touch it? No, you would not. Then why would you risk living in 2025 without having a reliable and efficient computer antivirus protection? Do you know that cyberattacks have quadrupled since COVID-19 hit the world? Ransomware, malware, and phishing attacks are multiplying daily; they have become like a tsunami that destroys everything in its path.
These attacks can ruin your life; cybercriminals use them to infect your devices, then steal your sensitive information and use it to gain financial benefits, or even lock your entire computer and ask for a ransom to be paid to have a chance to access your database again.
Fortunately, there is a way to fight back and protect your device and the data stored on it. With just one wise decision, start using antivirus software that can provide you with all the advanced features and protection capabilities, like real-time protection, ransomware protection, firewalls, and AI and ML technologies that can identify malware 24/7 before things escalate.
This guide will discuss how antivirus protection works, why you need such software, what threats antivirus protects from, and how to choose the best software on the market. Let's get started.
Types of antivirus protection
Antivirus protection is highly recommended for anyone using computers or mobile devices. Cybercriminals are continuously developing more destructive and sophisticated threats, from phishing attacks and malware to ransomware and identity theft. Protecting your devices and personal data has never been more critical. Users should consider equipping their systems with reliable antivirus software to defend against these potentially devastating cyberattacks.
Let's break down the types of antivirus protection to help find the right solution that fits your budget and meets your requirements. There is no universal "best" software—a solution that works effectively for one user might be insufficient for another. Understanding how different protection mechanisms work and what security features they provide is crucial for making an informed decision when selecting antivirus software.
Basic (free) antivirus software
It is an ideal solution for casual users, since these programs, like AVG Antivirus Free, offer essential protection against viruses and malware. It uses a signature-based detection method, which relies on a database of known malware signatures. So when you run a full or a quick scan, the software compares files on your system to this database to identify whether a particular file may be infected. If the software detects such files, it flags them immediately, and they are either quarantined for further inspection from your side or deleted.
Key features:
- On-demand scanning—Where you manually initiate scans to check for threats.
- Real-time scanning—Continuously monitors your system for suspicious and abnormal activity. Keep in mind that most free versions offer limited functionality for this feature.
- Malware and virus removal—The software automatically quarantines or deletes the infected files.
Limitations:
- These programs do not protect your devices from unknown malware attacks (zero-day threats).
- Do not offer advanced tools like firewalls, app lock, identity theft protection, and advanced AI and ML threat detection capabilities.
Advanced antivirus software
Advanced antivirus tools use heuristic analysis, behavioral monitoring, and machine learning to detect and block known and unknown cyber threats. Heuristic analysis involves examining the behavior of apps and files with the main purpose of identifying any suspicious patterns. For example, some types of malware attacks try to modify system settings and access your sensitive data. If the antivirus software detects such activity, it will immediately flag it as a threat and quarantine it to stop the attack at its early stage.
Behavioral monitoring is responsible for tracking the activity of programs in real-time, meaning that if a program tries to encrypt files, the antivirus program can spot that attempt and stop the attack immediately.
Machine learning works differently; it uses intelligent algorithms to analyze vast amounts of malware data and real malware attack cases, enabling it to improve its ability to detect new threats, thus providing efficient protection against zero-day attacks.
These advanced techniques work in a collaboration in order to provide protection with high success detection rates above 95% against the countless cyberthreats that every user may face daily. Furthermore, most advanced antivirus solutions offer features for optimizing system performance, customer support, and an intuitive interface.
Key Features:
- Firewall—Monitors network traffic to block unauthorized access.
- Wi-Fi protection—Alerts you to insecure networks and prevents hackers from intercepting your data.
- App lock—Secures sensitive apps on mobile devices with a password, two-factor, or multi-factor authentication.
- Online privacy tools—Blocks phishing attacks, infected links, and online scams.
Limitations:
- May require more system resources than basic antivirus.
- Come with a recurring subscription fee.
All-in-one protection
These solutions are equipping you with many more protection features than those provided by a typical antivirus software. They offer a multi-layered protection system that not only detects and removes viruses, malware, and other cyber threats but also provides backup and restore capabilities in case of an incident, identity theft protection, and extra features for addressing multiple threat vectors simultaneously.
Key features:
- Full-system protection across multiple devices and platforms.
- Advanced AI-powered threat detection and prevention.
- Real-time monitoring of system vulnerabilities.
- Complete data backup and recovery solutions.
- Identity theft protection with credit monitoring.
- Secure online banking and shopping environments to keep you safe online at all times.
- VPN services for enhanced online privacy.
- Parental controls and child safety features to protect your entire family online.
- Performance optimization and system cleaning tools.
Having such protective software on your side literally creates a 360-degree protective system, proactively blocking sophisticated cyberthreats while providing peace of mind knowing that no matter the circumstances, you will not lose your database or face life-ruining consequences.
Limitations:
- They come at a higher price compared to advanced antivirus tools, which is reasonable since they provide complete protection for your devices.
Why do you need antivirus protection?
Because it successfully protects your devices, database, and sensitive information against being used for fraud, sold on the dark web marketplaces, or being used by cybercriminals to gain financial benefits without your knowledge. Did you know that according to research, 90% of cyberattacks in 2024 involved social engineering tactics? Powered by AI, these attacks are at their peak, since the rapid expansion of AI and GenAI tools provides cybercriminals with the opportunity to scale their attacks. Can you imagine how far hackers can go? Nobody knows, but one thing is for sure: only time will show, but things do not seem to calm down any time soon.
One of the most important things you can do to protect yourself against these attacks is to start using antivirus protection. keep in mind that there is no software in the world that can make you immune to cyberattacks and guarantee 100% success rates.
Nevertheless, equipping your devices with reputable and efficient antivirus software can significantly reduce the chance of falling victim to a cyberattack. Well-implemented security solutions typically block between 90-95% of known threats, though their effectiveness against zero-day attacks varies. Without such protection, you are leaving yourself vulnerable to a host of risks that can disrupt your life in ways you might not even imagine.
What are the consequences of not using antivirus protection?
The consequences can range from minor inconveniences to catastrophic losses, depending on the severity of the attack. You could wake up one morning to find your bank accounts drained, credit cards maxed out, new loans taken in your name, or your identity used in criminal activities without your knowledge.
Cybercriminals might also lock your computer, use it for cryptomining, or exploit it in numerous other ways. Believing that this will not happen to you is dangerously complacent; while not inevitable, the risk is real and significant for everyone connected to the internet.
How can cyberthreats impact personal privacy, financial security and businesses?
Have you ever considered how much of your life is stored online? From bank details to private messages, photos, and videos, your digital footprint is vast. Cybercriminals are constantly looking for ways to exploit vulnerabilities, and without effective protection, your personal privacy and financial security are at serious risk.
Phishing attacks, infected links, and online scams are just a few of the online threats that can lead to identity theft or stolen personal info. For businesses, the stakes are even higher, where even a single breach can lead to stolen customer data, costly downtime, and irreparable damage to reputation.
For example, in 2023, the MOVEit file transfer software breach exposed the sensitive data of hundreds of organizations, including government agencies and large enterprises. Cybercriminals exploited software vulnerability to steal personal information, financial records, and other critical data.
Such breaches occur when organizations or PC users do not update their operating systems and other third-party software applications; they do not implement adequate security measures, which results in leaving them exposed to vulnerability exploitation.
This is just one example; unfortunately, these happen daily, and hundreds of organizations and individuals find themselves in such catastrophic situations, while on the other hand, antivirus software could save them from such scenarios or at least minimize the damages.
So, you should never ask yourself if you need antivirus protection, but ask which is the best choice. Always seek solutions that will provide the necessary computer and mobile security to minimize the risk of becoming the next cybercriminal's victim.
What threats does antivirus protection defend against?
Have you ever wondered how many ways your computer and mobile devices can be compromised? Well, you will not like the answer, but we have to discuss this. Viruses can infect your device and corrupt files, ransomware attacks can lock your computer and demand a payment for giving you back access to it, while spyware silently steals sensitive information without leaving any traces.
Beyond these threats, phishing attacks use deceptive tactics to trick you into providing personal information that later will be used for financial fraud and other criminal activities. Let's not forget malware, which is hidden in seemingly harmless downloads. As you see, each threat has its own way of causing harm, but they all share one goal: exploiting vulnerabilities in your system. A reputable and efficient antivirus program can detect these threats and intercept them, saving you time, money, and headaches.
How are threats delivered?
The human factor is the weakest link in cybersecurity; that is a fact. With this in mind, consider how often you click on links from emails sent by friends. Do you download applications from untrusted sources?
All these activities can reward you with the unwanted surprise of malware infection. What is even more concerning is that even trusted platforms like Google Play and the App Store can host hidden dangers despite each application undergoing security tests before being delivered to users.
Why is a proactive approach to threats necessary for complete protection?
A purely reactive approach is not effective anymore against the cyber threats as we know them today, leaving your system vulnerable during critical exposure periods. Effective protection requires multi-layered defensive strategies and approaches that can properly identify emerging threats before they strike.
Advanced solutions are effective because they combine real-time scanning, behavior analysis, and threat intelligence to identify suspicious patterns that indicate potential cyberattacks. Furthermore, these tools are constantly updated to provide protection against newly discovered and previously unknown vulnerabilities and threats. Many can automatically renew their virus definitions, while automatic quarantine prevents detected infections from spreading across your devices.
This is why a proactive approach significantly reduces risk exposure compared to antivirus tools that rely solely on signature-based detection methods. Additionally, features like firewalls, app locks for sensitive apps, VPN, and Wi-Fi security add an extra layer of protection, not only for your computer but also for all of your mobile devices.
Acronis True Image as a solution
Acronis True Image provides all the necessary tools to protect your devices from cyberthreats. This all-in-one solution not only equips you with powerful cybersecurity but also automates the backup process to create copies of every file in your invaluable database, allowing you to quickly restore all your data when needed.
If you want to minimize the risk of experiencing a cyberattack that may literally ruin your life, equip your devices with reliable and effective protection against the countless cyberthreats that stalk around the corner to strike in the most inappropriate moment. Are you curious how Acronis True Image works? Let's explore its core features, and you will understand how things happen:
- Top-notch Ransomware ProtectionUses behavioral analysis and machine learning to detect both known and zero-day attacks.Creates instant local backups when suspicious encryption attempts are detected.Enables prompt recovery in case of confirmed threats.
- Advanced Threat DetectionNeutralizes ransomware, viruses, other malware types, and email cyberattacks.Analyzes system behavior and network activity to prevent compromises.Provides exceptional phishing protection to safeguard your information and credentials.
- Comprehensive Backup & RecoveryOffers flexible backup options (full disk images, incremental, and differential).Protects entire systems or specific folders.Supports mobile device backup (iOS and Android).Verifies backup integrity and allows testing in a safe environment.
- Customizable Automated BackupSchedule backups (hourly, daily, weekly, and monthly) to save time and ensure your data is always protected.Choose backup types (full, incremental, differential).Set custom retention policies for local and cloud storage.Achieve recovery time objectives under 15 minutes for individual files.
- Secure Cloud StorageAccess AES-256 encrypted backups through Acronis's cloud infrastructure.Store data in geo-redundant data centers with optional multi-factor authentication.Choose from storage tiers ranging from 50GB to 5TB.Sync data between multiple devices.
- Privacy Protection ToolsEncrypt sensitive data.Manage passwords effectively.Prevent identity theft and unauthorized access.
- 24/7 Customer SupportAccess technical assistance via phone, chat, and email whenever needed.
Unlike traditional anti-malware solutions that focus solely on threat detection, Acronis True Image delivers professional-grade data protection that goes beyond basic malware removal, ensuring the best possible security for all your devices.
How to set up Acronis True Image for maximum protection
Once you choose to rely on Acronis True Image for protecting your devices, it is time to configure it properly to take advantage of the powerful security features of the product. Below you will find step-by-step instructions for installing the software, enabling the active protection, and backing up your entire database for added data security.
How to install Acronis True Image
- Step 1: Launch the Acronis True Image installation package (with .dmg file extension).
- Step 2: In the window that appears, double-click the "Install Acronis True Image" icon.

- Step 3: Strictly follow the on-screen installation wizard.
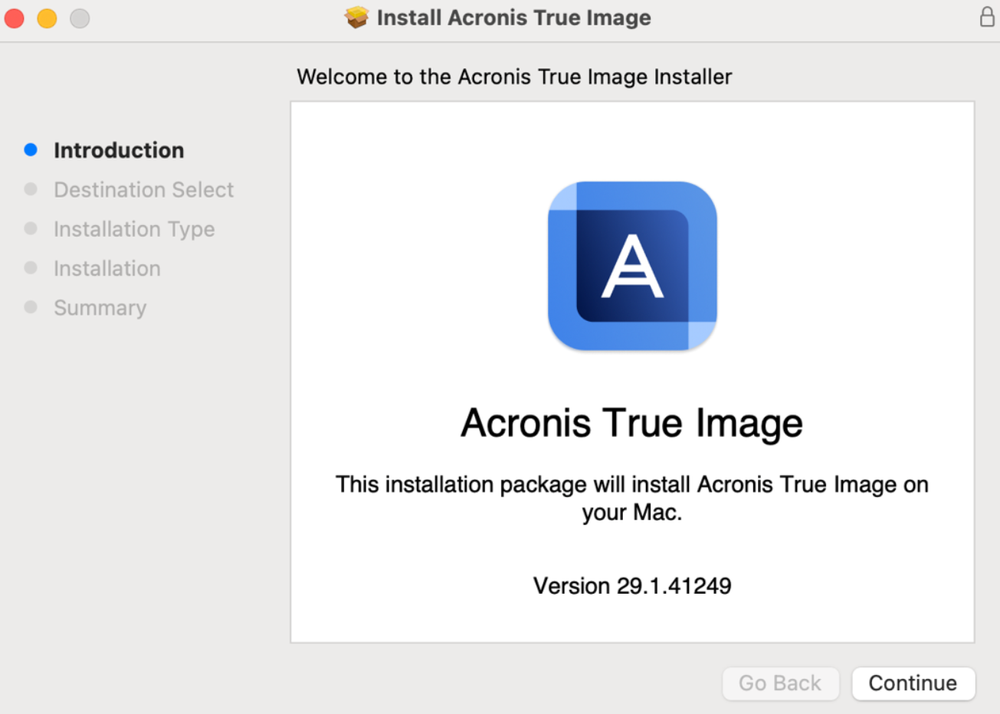
- Step 4: Enter your credentials when prompted to complete the installation.
How to enable Acronis True Image—Real-time protection (Active Protection)
- Step 1: Launch Acronis True Image.
- Step 2: Navigate to the Protection tab.
- Step 3: Once in the Protection tab, click Settings.
- Step 4: In the Active Protection tab, turn on the Anti-ransomware Protection, Real-time Protection, and Web Filtering toggles to protect your computer and your personal files.
- Step 5: Click OK.
Create a backup of your database for added data security
- Step 1: Open the Acronis application.
- Step 2: On the left pane menu, click Backup, then click Add Backup.
- Step 3: Select the backup source icon on the left, and then choose the type of items you want to back up - Disks or Files and folders.
- Step 4: Next, you must select the items that you want to back up and then click OK.
- Step 5: Click the backup destination icon, and then select a preferred destination for backup.
- Step 6: Click Settings to set the options for the backup, including schedule and archive cleanup. The scheduled option is very useful; it enables you to perform scheduled backups based on your preferences.
- Step 7: Once ready, click Back up.
Choosing the right antivirus protection
When selecting the right antivirus protection, the most crucial things to consider are: what are your needs, how many devices do you want to protect, and what features are crucial for equipping yourself with reliable and efficient antivirus software? The best antivirus software must equip you with:
Malware protection
A detection rate of 95% demonstrates above-average performance in identifying and removing malware threats, according to AV-Test. As mentioned earlier, cybercriminals nowadays develop new threats using AI to evade detection, but premium antivirus tools are constantly updated to provide you with essential protection against the latest cyberthreats.
Continuous real-time protection
Real-time protection is a must, since it monitors your entire system, all of your files and programs for any suspicious and abnormal behavior. This proactive protection mechanism stops ransomware, viruses, spyware, and other malicious codes before they get out of control, ensuring your PC and mobile devices are protected.
Anti-spam and pop-up blocking
Malicious pop-up advertisements and spam-filled websites are well known for being common infection vectors. If you click unintentionally on such an ad, it may start a download of a file and open Pandora's box for your computer.
Thankfully, today's antivirus programs are able to intercept these threats by blocking intrusive pop-ups and spam content from suspicious websites, reducing the risk of infecting your device.
Web protection
Reliable security software will provide you with multi-layered protection mechanisms like URL filtering, real-time content analysis, and browser integration via extensions or API hooks. These systems function by continuously inspecting HTTP/HTTPS traffic, verifying website certificates, and scrutinizing JavaScript execution patterns, all with the aim of safeguarding your device while browsing the internet against malicious attacks.
Some antivirus programs even offer cloud-based sandboxing to examine and remove suspicious files in isolated environments and employ heuristic engines with ML algorithms to detect previously unknown threats.
Dark web monitoring
This is another fundamental feature to look for when choosing protection software for your computer. Dark web monitoring uses specialized crawlers, honeypot accounts, and intelligence feeds to scan accessible areas of Tor networks, I2P environments, and cybercriminals' forums for exposed credentials.
This monitoring mechanism gathers information from known breach repositories and different dark web marketplaces. If it detects your name, address, social security number, or other information related to your identity, it instantly notifies you.
Anti-phishing protection
This type of protection works by a combination of multiple detection methodologies: URL blacklist verification, SSL certificate analysis, domain score assessment, visual similarity detection, and content heuristics that are able to identify credential harvesting forms. They work both at the browser level (through extensions that perform real-time checks) and at the network level (through DNS or HTTP traffic monitoring).
Premium antivirus programs leverage ML models that are specifically trained on phishing patterns to successfully detect any known and zero-day attacks.
Customer support
Customer support is as important as any other protection feature that antivirus programs provide you with. You may face any kind of issue, whether it is a bug in the software or you have questions about how to use its full potential. In such cases, having the ability to contact technicians 24/7 is essential because they will help you resolve these problems quickly and efficiently.
User-friendly interface
Last but not least, select an antivirus program that has mastered the art of making complex technology accessible. A user-friendly and intuitive dashboard will give you a complete overview of your security status while making advanced features easily accessible, so do not compromise on that.
Conclusion
Nowadays, we live in a world where our computers and mobile devices are an inevitable part of our daily activities, so equipping them with antivirus protection is not optional anymore; it is vital. Seeing how cyberattacks grow both in frequency and sophistication leads to the conclusion that the risks to your personal privacy, financial security, and even your identity have never been greater.
From ransomware and phishing attacks to zero-day threats, our digital world is fraught with dangers that can ruin a person's life in unimaginable ways and in a matter of minutes.
Equipping yourself with robust and effective antivirus software is of utmost importance to reduce the risk of becoming the cybercriminal's next victim, and Acronis True Image stands out as a comprehensive solution. Rather than focusing solely on threat detection, it acknowledges that comprehensive protection must include data recovery, automatic backups, cloud storage, and a variety of privacy tools—all accessible through an intuitive interface.
Whether you are protecting sensitive files, securing online transactions, or ensuring your data is recoverable after an attack, Acronis True Image delivers peace of mind knowing you are covered and protected from the unexpected. This solution is able to address the full spectrum of digital threats facing users in 2025.
Do not wait until you become another cybercrime statistic; protecting your devices and database requires proactive measures and efficient security tools. Choose Acronis True Image—the all-in-one solution that combines cutting-edge security with user-friendly functionality—because your data, privacy, and peace of mind are worth it. Investing in this software will position you one step ahead of the mean and destructive cybercriminals' attacks. Take action today and secure your future!
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.




