If you’re a user, you always have access to the internet in the office – it’s a given that you don’t have to think about too much. At home, however, each of us usually plays the role of an admin, where your task is to set up the system that your family can use properly. Now that we’re in the midst of the COVID-19 epidemic and a lot of people are working from home, it is more important than ever to double-check the security of your router, since it is now not only the gateway to your personal data, but also to the valuable company data you are accessing remotely.
By default, modern wireless routers use signals that cover a much larger area than your average apartment. Combine that with the number of times that you’ve shared your Wi-Fi password with friends, relatives, and neighbors, and suddenly you realize how many people actually have access to your home router. There are a few security issues you need to solve to be sure your home digital environment is now safe:
- First, ensure your router’s firmware is updated to block known vulnerabilities.
- Next, limit the access others have to the router and your Wi-Fi network(s).
- Then, reduce the signal strength to cover the space you need, but not more than that.
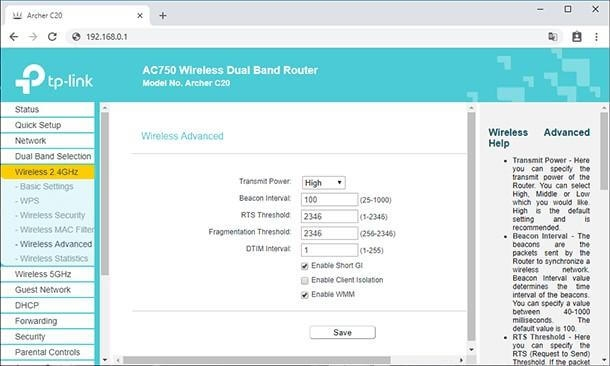
Ensure that you’re running the latest firmware and do not use a default login and password When you log in to your router management console, what credentials do you use? Changing the default usernames and passwords is a must. There have been too many cases in which cybercriminals easily accessed routers using default login credentials that are publically available on the internet, changed all of the settings, and redirected traffic to the resources they need – which completely compromises the users' internet access. Everyone knows that by using “admin/password” or “admin/admin” you can find your way to the heart of every other router The strong password rules that are normally recommended work just fine here. While the user name can be anything of your choice, using a long-phrase password stops most blunt attackers. Just changing your login credentials is not enough, though. The next step is to check if there have been any firmware updates for your router. You can find this option in the advanced settings and the firmware typically can be downloaded right from the management console and automatically applied. You should also check if the model of your router is considered safe. There can be critical vulnerabilities known to exist in your type of router, but no new firmware patch to fix it. If that is the case, you should seriously consider replacing it with a model that offers better security – otherwise you’re open to attacks; changing the password will not help. A couple of years ago, the American Consumer Institute Center for Citizen Research studied the router security of 13 different manufacturers, including Linksys, Belkin, Netgear, and D-Link. While 17% of the routers scanned were vulnerability-free, that the remaining 83% of routers examined had, on average, 172 vulnerabilities. How to harden router settings Once you’ve taken those initial steps, it's time to look at the router functionality and adjust any settings that can add more security. Turn off Wi-Fi Protected Setup (WPS) WPS offers an easy way to get new devices to recognize the network and connect to the router with the press of a button. Unfortunately, this convenience presents a security weakness – the code method used to establish the connection is easy to crack. If your router has a WPS button, then turn off the WPS code capabilities in the console – it's better to rely on the button. If you don’t have the button, you should turn off WPS completely. The WPS button is either found on the front or back of your router and can greatly vary in size. Turn off UPnP Universal plug and play (UPnP) is a convenient way of allow gadgets to find other devices on your network and, if necessary, to modify your router so it allows for device access is available from outside of your network. It is better to switch off router UPnP capabilities, however, because of the potential hacks available through it. There were several such attacks seen last year. Wi-Fi encryption should be WPA2 with AES WPA2 with AES encryption is the only strong enough option available in home routers that is strong enough. Each Wi-Fi password should be a long phrase, as we discussed above. It is recommended that you change router password regularly – and in difficult times like the COVID-19 pandemic, it should be at least once a month. Be smart about choosing an SSID Service Set Identifier (SSID) is basically your wireless network’s name. Router manufacturers often put the brand name or model of the router in the SSID. If you got a router from your internet service provider, they might change that SSID to show their own name instead of the manufacturer’s. Don't use the default and do not identify yourself. Next, your router doesn’t have to broadcast its SSID – make it a hidden network. The devices that already have connection data stored will still be able to connect, but no one else will be able to see the SSID and. Without it, it is impossible to connect to it. Use a password-protected guest network If your router supports guest networks, use them – but do not make them open: lock them down with password protection. Whenever possible, use a guest network for your IoT devices, which are largely vulnerable and unprotected. That way, if the bad guys do find their way into your IoT network, all they’ll find is the other IoT devices – they won’t be able to work their way onto your computers or phones. Don’t forget though that if you sign in to your Google account through your smart TV, it can be compromised. Disable Remote Administration Many routers offer functionality that enables it to be controlled from a remote network. You do not need this when you work from home, so be sure to disable it. Your router’s console should only be accessible from the devices that are connected to the network. Switch off port forwarding Port forwarding or port mapping is an application of network address translation (NAT) that redirects a communication request from one address and port number combination to another while the packets are traversing a router. In most cases you don't even know that your router has this feature, so just check that it is turned off. Shutting off NAT port mapping protocol (NAT-PMP) protects both your system and the rest of the internet. Turn on the firewall If your router has a built-in firewall in it, it is better to turn it on. This works a little differently than the software firewalls in Windows and macOS, since a hardware firewall doesn’t block traffic requested by a client within your LAN. That means you can – and should – keep the software firewall in your OS running as well. Use a VPN A VPN client may be embedded into your router. If so, use it. It is a good solution to the problems raised by wireless packet sniffers. The protection offered by the VPN goes through the router, which means that even if the router’s encryption were somehow removed, you still have VPN encryption making your data unreadable. Test for open ports For technically advanced people this Test Your Router page provides many ways to test for the kind of open ports that are a security issue. If you want to dig deeper into the topic, it also contains a lot of useful information regarding known attacks and security flaws. Center or reduce your signal footprint Modern routers are quite powerful and their signal can cover relatively big spaces. Be mindful where your router is placed and, if your house is larger than the router’s signal footprint, center your router in the middle of the house. That will give you the maximum coverage available while preventing the signal from passing outside. If your apartment or house is smaller than the signal footprint, then you have several options to reduce the signal strength. If your router allows you to tweak its signal power, experiment with it. You could use a 5GHz range if all your devices support it because it has a smaller range and does not penetrate walls easily. Example of router management console where you can control transmit power By applying these recommendations, you can ensure your home Wi-Fi network will be better equipped to stop cyberattacks. The safety of your remote working environment will be boosted dramatically, both now and in the future.

About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 20,000 service providers to protect over 750,000 businesses.




