There is always a lot happening in the world of cybersecurity, so we’ve captured some of the latest news in this week’s roundup.
Chasing the Chinese government’s COVID-19 secrets
Certain valuable data related to COVID-19 pandemic and thought by some analysts to have been kept secret by the Chinese government is attracting hackers from around the world. For example, the Vietnamese state-sponsored hacking group APT32 (also known as the OceanLotus Group) reportedly attacked Chinese state organizations hoping to steal virus control measures, medical research, and statistics revealing the number of infections that allegedly has not been disclosed by China. Vietnam is a neighbor of China and its interest in part appears motivated by its desire to control the spread of the pandemic around the region.
COVID-19 themed phishing campaigns
COVID-19 theme continues to be used in spear phishing campaigns to distribute Formbook in a rogue email with archived malware (SHA256: cfc573d1ea473dcb5bcfb0c3f869cc73f464dc3e697dca44d245c402803a5c90).
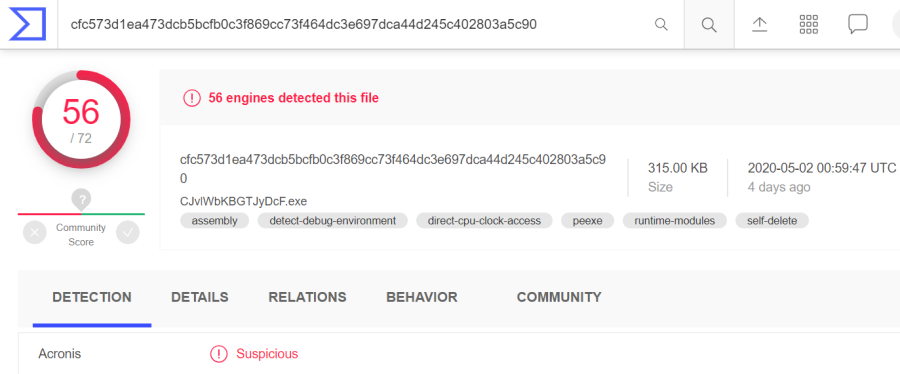
Source: Virustotal.com
A new pandemic-themed phishing email delivers a Formbook Trojan embedded into a bogus grade application for school teachers. Formbook is a type of form-grabbing software capable of stealing login credentials from web forms in an Internet browser. It has been promoted on hacking forums since February 2016.
Interestingly, the attackers employed several anti-analysis and anti-detection techniques such as sandbox detection and virtual machine detection, steganography and XOR encryption to hide the payload, thereby effectively evading Windows Defender.
The criminals behind Formbook campaigns have also been known to attack biomedical firms to steal financial resources, sensitive personal data, and intellectual property.
The new Trickbot campaign also exploited COVID pandemic fears to spread a malicious document entitled, “Family and Medical Leave of Act 22.04.doc” (SHA256: 875d0b66ab7252cf8fe6ab23e31926b43c1af6dfad6d196f311e64ed65e7c0ce). The Family Medical Leave Act (FMLA) provides employees the right to have medical leave benefits.
AI technology to detect COVID-19 was stolen by hackers
The Chinese company Huiying Medical, purported to have developed AI that can diagnose COVID-19 disease based on computed tomography (CT) scanning images with 96% accuracy, was allegedly hacked. According to cybersecurity firm Cyble, a hacker dubbed “THE0TIME” put Huiying Medical data up for sale on the Dark Web that may contain user information, source code, and reports on experiments at an asking price of four bitcoin (approx. $30,000).
Microsoft 365 users attacked with fake Microsoft Teams notifications
Up to 50,000 Microsoft 365 users were attacked with phishing emails containing fake Microsoft Teams notifications that redirect victims to a fake Microsoft 365 login page.
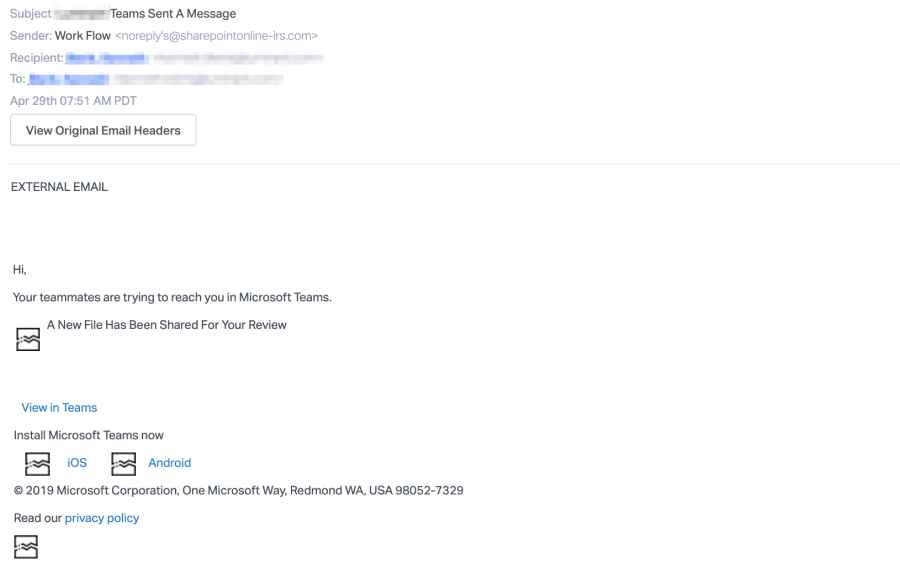
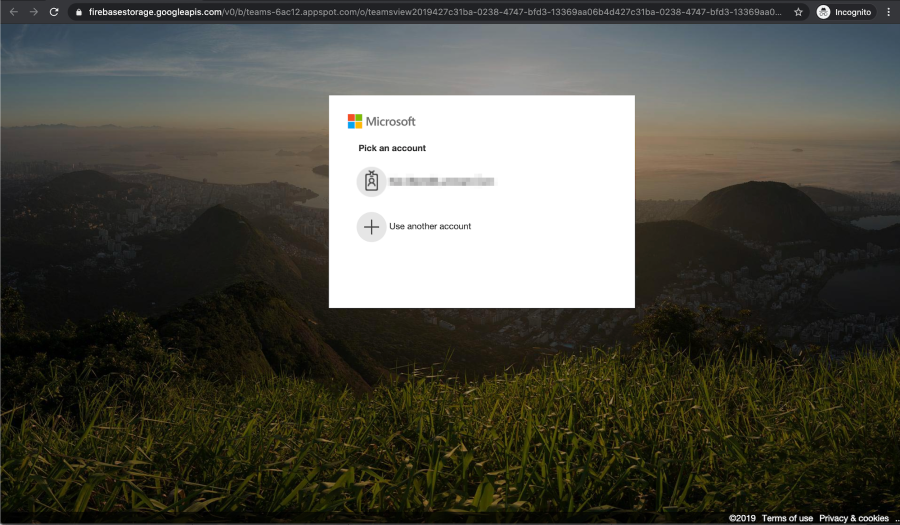
Phishing attacks on Microsoft file-sharing services
In the first quarter of 2020, Microsoft file-sharing services such as Sway, SharePoint, and OneNote were attacked via several small phishing campaigns that targeted financial services companies, law firms, and real estate groups. One attack, named PerSwaysion for its abuse of Sway services, executes in three steps. It starts by sending phishing emails that contain a malicious PDF attachment, purporting to be a Microsoft 365 file sharing notification with a “Read Now” hyperlink. Clicking on the link opens another decoy document in Microsoft file-sharing services (notably Sway) with another “Read Now” link that takes the victim to a bogus Microsoft sign-in page that steals their credentials.
Keys for Shade and Troldesh ransomware released
The cybercriminal gang responsible for the Shade and Troldesh ransomware attacks decided to publish 750,000 decryption keys after it shut down its operations at the end of 2019. If you have been victimized by one of these attacks, your decryption keys may be available without having to pay a ransom. If your encryption files have one of the extensions below, check the ShadeTeam project on GitHub and follow the instructions to decrypt your files:
xtbl, ytbl, breaking_bad, heisenberg, better_call_saul, los_pollos, da_vinci_code, magic_software_syndicate, windows10, windows8, no_more_ransom, tyson, crypted000007, crypted000078, rsa3072, decrypt_it, dexter, miami_california
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



