Cybersecurity is the practice of defending your networks, systems, and applications from malicious online threats.
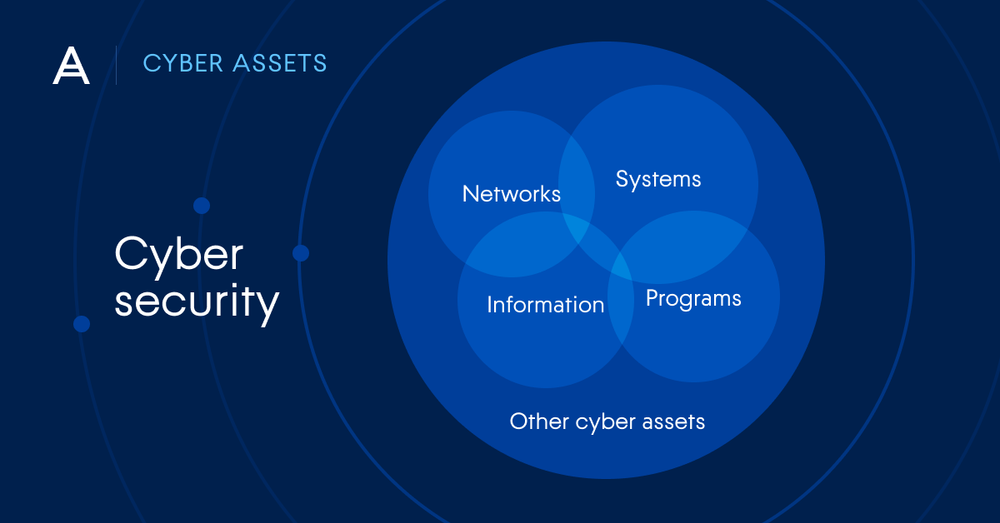
Digital data and operations are already at the core of most modern organizations, and this trend is only increasing. But with this reliance on computerized systems comes a variety of threats. These risks may be internal, originating with employees and contractors. They may be external, the result of activity by cybercriminals, or even your own customers. They may be deliberate acts of data theft or disruption, or they may simply be caused by human error and negligence.
No matter where or why a cyber threat originates, it has the potential to be devastating to companies, their employees, and their customers. That's why it's important to understand cyber security practices and tactics for effectively defending against hazards in the digital world.
Why is cybersecurity important?
Today's organizations face critical challenges with respect to cyber security. Data creation, processing, and storage is increasingly done at the edge, growing operational complexity and making data flows harder to track. Meanwhile, ever-greater computing power and AI are widely accessible, allowing cyber adversaries to target businesses more effectively than ever before. And these criminals are highly-motivated, driven by the prospect of multi-million-dollar rewards from businesses that often can't afford not to pay for the restoration of services or the recovery of lost data.
Any organization that uses modern technology must contend with the risk of potential threats. Taking steps to conduct a risk assessment is crucial for the health and operational security of businesses. Data security breaches and cyber attacks against business services have the potential to cause catastrophic financial and reputational damage, and the unauthorized access of PII(Protect sensitive data and personally identifiable information) can have severe impacts on the lives of employees and customers.
What are the 3 main pillars of cyber security?
Most people would associate cybersecurity with technology. Be it hardware or software, the common misunderstanding about cybersecurity is that it only relies on tech components.
Technology plays a massive role in a company's cybersecurity posture, but it's not merely enough to fight off cybercriminals all on its own.
Robust cybersecurity comprises technology, processes, and tactics to protect users and businesses from cyberattacks. Cybersecurity can minimize the risk of successful cyberattacks on your systems by implementing specific systems, networks, and technologies. It relies on the "information security management system (ISMS)" model.
And here comes the kicker – ISMS is built upon three primary pillars – people, processes, and technology.
For cybersecurity to operate correctly, you'd need specific technology, the proper processes to enable its potential, and humans to use it effectively to deny vulnerabilities in the system's defenses.
Let's explore the three pillars below to understand ISMS better.
People
As "people" is a broad, vague term when we discuss specifics in cybersecurity, let's break it down into two major aspects.
When we say "people", firstly, we refer to every person working in an organization. Employees should be aware of their role in the ISMS and fulfill it adequately.
To prevent or, at least, reduce the effect of cybersecurity incidents, employees should be aware of how to handle confidential data, how to spot phishing emails, and how to browse securely on the web. Additionally, they should be mindful of how to use their own devices for work (BYOD), secure their home against network intrusions when working from home, and more.
As cybercriminals target people to infiltrate a network, all company employees must understand all known threats and treat them accordingly.
Secondly, there's a group of people in every organization (or, at least, there should be) entrusted with broader responsibility. Your chief information security officer (CISO) and their team(s) need to be fully aware of all potential threats and be equipped with the latest skills and qualifications to manage cybersecurity controls, tech, and practices involved in battling a cyberattack.
If either of the two groups falls behind in preparation, your organization wouldn't be able to ensure adequate security measures.
For example, every employee can be educated on how to detect and respond to known threats. They can operate immaculately against all threats that they know of. However, if your IT staff isn't aware of a newly-emerged cyber threat, they wouldn't be able to inform your other employees about it. The latter, in turn, won't know the threat when they stumble upon it, so they won't be able to react correctly.
On the other hand, even if your IT staff is aware of all advanced persistent threats, it only takes for one of your employees to slip and accidentally click on a phishing email attachment. The attachment may carry ransomware or a pesky virus and quickly render your company's data corrupted or unusable.
Both scenarios can lead to data loss and disruption of business operations. To avoid a negative impact on your company, you'd need both prongs of the people pillar to operate in sync to counter threats effectively.
Deep dive into the first pillar of cybersecurity
According to a Proofpoint research conducted for Verizon's "2022 State of the Phish", 78% of organizations suffered from email-based ransomware attacks in 2021. In addition, the researchers identified 15 million phishing messages armed with malware payloads that were later linked to later-stage ransomware.
Why is this important here?
Well, for any phishing email to succeed, it needs a target user to take the bait. In an organization, employees are the widest attack surface for cybercriminals – even if only one user engages with malware, it may spread over your network almost instantaneously.
This is why training your employees to prevent phishing and social engineering attacks is crucial. In the best-case scenario, your employees would know how to spot a phishing email and report it. They'd also be aware not to download any suspicious attachments from unknown senders and not to respond to credential and login information requests as cyber attackers may try to steal sensitive data via them.
One of the most cost-effective approaches to sensible cybersecurity is employee training. You can divide the training into two categories – formal and informal.
The formal training should include training regarding your company's policies and procedures alongside specific incident response guidelines.
As for informal training, you can consider simulating phishing attacks and follow up with feedback.
You can also send mass emails informing your employees of current threats or other beneficial information. For example, a reminder email may reiterate that employees should never provide login credentials or other sensitive data via email, even if the sender and message seem legitimate. It's a simple task, but it may prevent your employees from interracting with (yet) unknown threats for them.
In addition, companies should consider annual reminders specifically for their payroll staff, as December, January, and February bring an increased chance of W2 phishing scams. During such digital attacks, your payroll staff is most likely to receive an email (supposedly from the CEO or CFO of the company) requesting employee W2 information.
Reminders, as the two above, are an excellent way to mix formal and informal training, but there are more things you can do as well.
For example, you can include tabletop exercises in the cybersecurity training of your employees. During such exercises, your employees can prepare for an actual data breach.
The simulation of a successful cyberattack can allow executives to test the employee's abilities to respond to an ongoing cyber threat in line with your organization's policies and procedures.
At the start, such practices may seem overwhelming to your workforce, but in time, they can significantly benefit your whole company's cybersecurity posture.
Processes
Processes in cybersecurity refer to management systems, policies and procedures, governance, and managing third parties—all of those need to be addressed correctly for the processes to operate effectively.
Processes are critical for any cybersecurity strategy as they define how an organization behaves in the face of a cyber attack. They outline the activities, roles, and documentation used to mitigate the risks of cyberattacks.
Processes must be continuously reviewed to adapt to the ever-evolving nature of cyberattacks. However, processes would resemble hollow shells if the people managing them weren't prepared adequately.
Deep dive into the second pillar of cybersecurity
Here, we will discuss four primary branches of processes as part of your cybersecurity strategy.
Depending on the company specifics, some may seem more relevant than others, but all of them combined can drastically improve your defenses.
Management systems
A proper management system goes a long way toward strengthening your cybersecurity plan.
Employees, executives, and cybersecurity professionals should understand their duties and responsibilities regarding cybersecurity. If your organization is bigger than most, the levels of competence assigned to different employees will vary greatly.
If you run a small business, these levels will, more or less, be evened out.
In both cases, a robust management system will enhance security awareness and fortify your defenses. Without such a system, issues (and data) could often escape your focus and open up vulnerabilities in your cybersecurity protection plan. If the problems persist unacknowledged, they may lead to data corruption, deletion, or compromise.
Enterprise security governance activities
Governance stands to reduce the risk of unauthorized third-party access to company IT systems and data. This prong of the second pillar comprises the development, assessment, institutionalization, and improvement of your enterprise risk management (ERM) and security policies.
Governance is responsible for determining how the personnel, executives, staff, and security specialists work together to secure data availability, ensure data loss prevention (DLP), and optimally protect your company's public image.
Governance activities should be consistent with your compliance requirements, management policies, and company culture. To ensure a state of development and sustainability, conducting a regular threat, vulnerability, and risk assessment, specific to your organization's industry is vital.
In doing so, companies can reduce the risk that a physical asset in their possession could be stolen or damaged. So, in essence, the governance of company security would include physical locks, barriers, fencing, fire response systems, lightning, intrusion detection systems, cameras, and alarms.
Policies
Policies "generate" a predetermined course of action to guide employees and executives toward strategies and objectives aligned with their company's preferences. It's a direct link between the vision of your company and the day-to-day operations.
Policies are responsible for identifying crucial activities and providing a primary strategy for handling various issues that may arise.
When a reader explores the policy, be it an employee or an executive, the text can pinpoint their limits and choices to guide them through a decision-making process and, ultimately, overcome potential problems.
Policies are most efficient when presenting the reader with a clear and easy-to-understand action plan required to implement the policy's purpose. If prepared correctly, a policy will help minimize or eliminate misunderstanding by setting clear boundaries and responsibilities for your workforce.
A well-written policy will also give executives control over events in advance and help prevent employees from making simple mistakes.
Third-party management
Better known as "vendor management", third-party management enables organizations to manage costs, mitigate risk, and enhance service excellence to improve gained value from their vendors.
In today's cybersecurity landscape, choosing vendors supporting the same (or higher) levels of cybersecurity as your own organization is critical. Vendors can just as easily be a target for a cyberattack. Allowing attackers to access a vendor's computer system may also translate into cybercriminals infiltrating your company's system.
Technology
The third pillar in cybersecurity can be labeled "technology" or "data and information".
Data and information protection is the most technical of the three pillars. (hence, "technology")
The gathered data needing protection originates from several sources; we have information technology (IT), personal data, operational technology (OT), and operational data.
All of the above must be managed appropriately and secured to negate data corruption or loss at any time.
Knowing the data your company handles enables your cybersecurity team to assess its associated risks and develop a list of needed technology to protect said data. Hardware and software can be deployed to reduce (or prevent) the impact of cybersecurity incidents, depending on your security plan, available IT staff, and budg
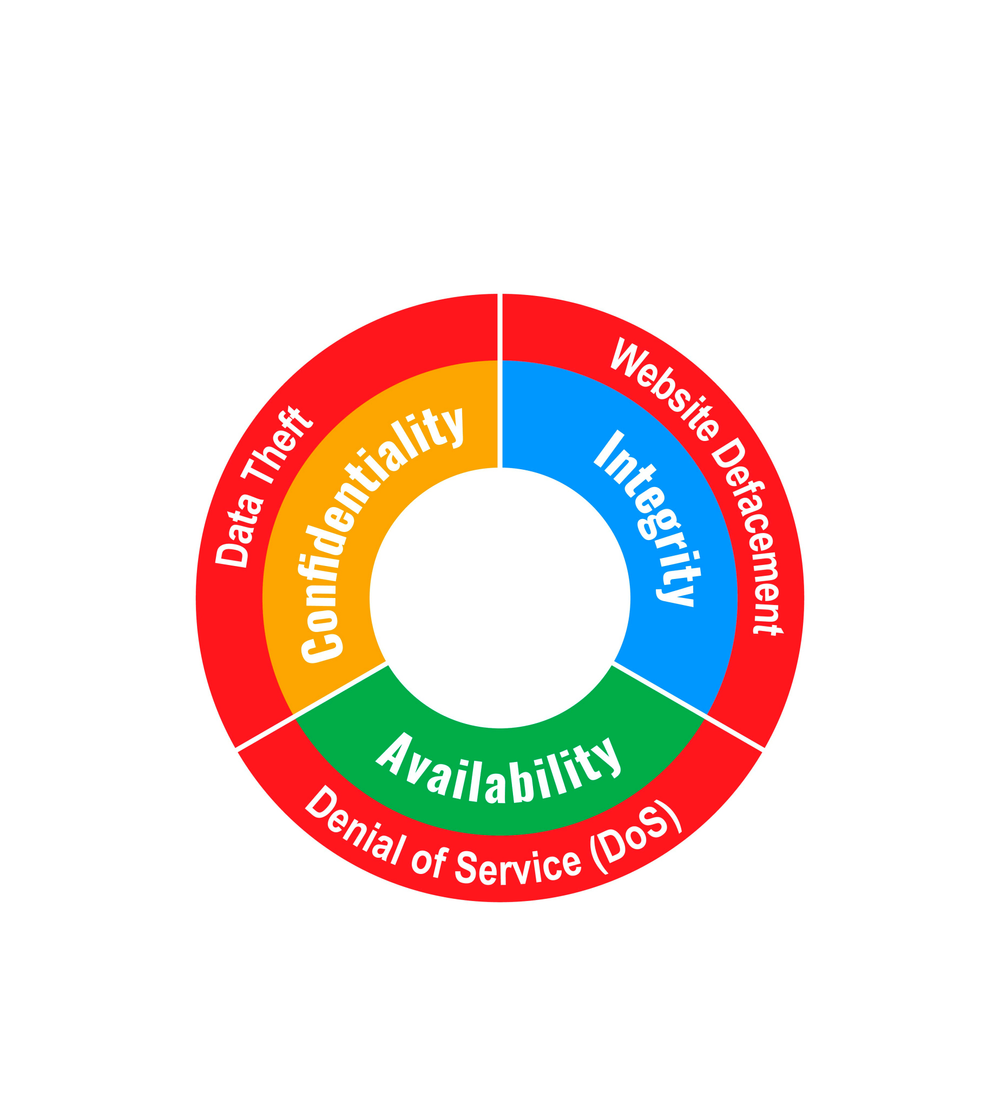
Deep dive into the third pillar of cybersecurity
When exploring data and information protection, we should emphasize the importance of the most robust information security model – the CIA triad. The CIA triad comprises confidentiality, integrity, and availability of data.
Let's discuss the three components of the CIA triad below.
Confidentiality
For the CIA triad, confidentiality represents authorized access to data. Here, confidential information doesn't refer to something hidden or encrypted but ensures that other parties haven't compromised your data.
Confidential data shouldn't be disclosed to people who haven't required it or who shouldn't even have access to it. For a company to ensure confidentiality, it should determine who can access different types of data – more sensitive company data would have stricter access permissions. Additionally, authorized persons should have enhanced endpoint security implemented on their devices.
A confidentiality breach may occur during a successful hacking attack or another malicious campaign.
Integrity
Data integrity addresses if data has been tampered with or degraded during (or after) submission. To ensure data integrity means to ensure that the data has not fallen victim to unauthorized modification, corruption, or compromise, be it intentional or unintentional.
Data integrity can be compromised at two critical points during the transmission process – during upload (transmission) or the data storage process in a database or other collection.
Availability
Availability ensures that data is available to authorized parties when needed. For a system to be deemed "available", it must cover several conditions – adequately functioning computing systems, communication channels, and security controls.
As you've probably heard of the term, some systems are considered "critical". These are systems related to medical equipment, power generation, safety systems, etc.
Critical systems have incredibly high requirements regarding availability. Such systems must be fortified to their teeth to counter sophisticated attacks; they should also have safeguards to negate power outages, hardware failure, and other negative-impact events that may compromise the system's availability.
Availability is potentially the biggest challenge in action-packed environments, as such environments must be stable and continuously maintained. In addition, users should be allowed to access needed information with little to no waiting time.
To enable such access, a company may consider implementing redundant systems to allow a high level of fail-over. In such a case, it's worth noting that "availability" may also refer to the usability of a system.
Going over to the term "information security", it refers to the preserved integrity and secrecy during data storage or transmission. When an unauthorized party accesses data they shouldn't be able to, the event may be classified as an "information security breach".
Data breaches may occur for different reasons – hacker attacks, criminal actions, intelligence agencies' interference, competitors, employees, or other ill-intended (or accidental) data compromise events.
Studying the CIA triad may enable companies to better understand modern data integrity threats and prepare for them accordingly. The approach can establish guidelines for sensible security policies in organizations of any size.
While designing and maintaining a company's security policies can be challenging, the three-pillared approach to cybersecurity can help you build a solid cybersecurity strategy in an optimal timeframe without unnecessary hassle or increased costs.
While cyber security often involves digital security measures, such as antivirus software and user privilege limitations, there are also physical and offline components that can help ensure complete protection against a variety of advanced persistent threats.
Some of the primary types of cyber security include:
Application security — preventing data and code in business-critical security software (both in use and in development) from being stolen or hijacked, such as with penetration testing and encryption
Information security — protecting physical and digital data from unauthorized access and manipulation, both on-site and through remote systems
Physical infrastructure security (a.k.a. physical security) — ensuring that the structures and facilities you rely on, such as electrical grids and data centers, are access-controlled and guarded against physical harm or disruption
Network security — securing internal computer networks against unauthorized access, with tools like remote access management and two-factor authentication (2FA)
User education — teaching employees and customers best practices for recognizing and avoiding known attack types, such as malware and phishing attacks
Who needs cyber security?
Every person handling sensitive data would benefit from cybersecurity, be it an individual user, an SMB employee, or an enterprise executive.
Modern cyberattacks have evolved to a point where everyone on the web can become a target. Especially with phishing campaigns, you may become a victim of malware even if cybercriminals haven't explicitly targeted you.
This is why it's crucial to understand the dangers of online threats and secure your data accordingly.
We’re obligated to mention that SMBs and large companies are more frequent targets of malicious attacks. Let's start by exploring the most frequently attacked industries before we proceed to more specific traits that put individual users at risk of a cyberattack.
Critical infrastructure and state and local governments
Governments are directly responsible for their nation’s or global well-being and safety. As they handle immense amounts of sensitive data, a successful cyberattack on their critical infrastructure can affect the lives of millions of people.
Cyber hits on governments, defense suppliers, law enforcement agencies, federal government servers, and military groups are gradually becoming more impactful than physical attacks against the same critical infrastructures. If ransomware strikes a government server, it may cripple its participants, rendering them unable to provide urgent and day-to-day services.
Additionally, successful attacks on critical infrastructure sectors also have national security implications. Such an attack can be catastrophic in causing severe service disruption or even physical harm. This is why critical infrastructure security is vital to counter ill-intended third parties.

Companies reliant on compliance and regulation
For some companies, cybersecurity isn't a matter of choice – it's mandatory. Many organizations (both public and private sector companies) operate under strict industry or government regulations; most of those include a cybersecurity clause. (in addition to physical security measures)
In adding a cybersecurity component to the regulations, responsible institutions ensure that organizations take the necessary precautions to protect their consumers' data and military, government, and other sensitive information from cyber incidents.
Below, you can check some of the most common compliance standards.
GDPR – General Data Protection Regulation – aimed at organizations that offer services and goods to European Union citizens
DFARS – Defense Federal Acquisition Regulation Supplement – aimed at Department of Defense (or DoD) contactors
HIPAA – Health Insurance Portability and Accountability Act – aimed at companies operating with healthcare data
CCPA – The California Consumer Privacy Act – aimed to give consumers higher control over the data collected by businesses; it also guides the law and how to implement it
PCI – Payment Card Industry – aimed at companies who accept, store, and transmit credit card data used in online transactions
The penalties for non-compliance can be significant, not only in monetary terms but also in damaging a company's reputation and even leading to loss of contracts.
Business-to-business (B2B)
As we've discussed, a company can suffer from a cyberattack even if they have taken the necessary precautions to educate its employees. If a vendor of yours lacks the levels of cybersecurity to counter a hacking attempt, they may spread the infection across all businesses they operate with.
This is why many bigger organizations should initiate cybersecurity checks to determine which vendors are "safe" to do business with. If a company neglects such assessments, a poorly secured vendor can unintentionally bring havoc alongside standard day-to-day services.
On the other hand, if you run an SMB and have clients (larger companies) that employ critical infrastructure security checks, failing to meet the safety conditions may cost you the contract.
Even if you don't rely on more prominent clients to ramp up revenue, it's still best to apply cybersecurity solutions as a network resource to counter attacks and pass a cybersecurity check if a contract does arise.
Which individual users are at the biggest risk of a cyber attack?
Is cybersecurity important for individual users?
Well, the matter may be subjective for some, and that's understandable. More often than not, private industry SMBs, larger companies, financial institutions, and critical infrastructure entities rely on security solutions more than home users do.
However, everyone handles different kinds of data, some of which can be sensitive regarding your personal and financial privacy. Even if you aren't handling business data on your home computer, chances are you keep cherished photos, videos, music, payment details, and other data on it.
Now, let's proceed to the most common habits enabling a cyberattack on your home network. (and thus, catalyzing the need for cybersecurity tools to help you battle potential attacks)
Opening emails from unknown senders and downloading attachments/clicking on embedded links
We sure talk about phishing a lot, but we feel it's mandatory.
Phishing is the most common attack method for ransomware nowadays. Users who discard it as a threat may quickly lose access to their data indefinitely.
If you often receive emails from unknown senders and open them, you're one step closer to infecting your computer with different forms of malware. As phishing emails aim to entice users to download an attachment or click on a corrupted link, they have become increasingly convincing to the unsuspecting user.
If you interact with a phishing email and don't have email security solutions on your device, the malicious code can infiltrate your network and quickly overtake control.
We're not saying that a cybersecurity solution negates the negligence toward phishing emails. Still, it offers an extra security step even for the most trusting users on the web.
Poor browsing habits
The internet is vast, and ransomware lurks behind (almost) every corner. If you visit unsecured websites and click on embedded links or try downloading "free" software, you can easily present attackers with control over your data.
A URL blocker (or other filtering feature) may save you from yourself, especially if you're clicker-happy.
Failing to update software
Patches and software updates are designed to fix cybersecurity vulnerabilities against evolved (known) cybersecurity threats. If you fail to patch your system regularly, you leave room for cybercriminals to exploit unpatched vulnerabilities and infiltrate your home network.
The same goes for security updates on your operating system and critical programs.
Now, if you have an automated patching feature on your cybersecurity solution, you won't need to worry about applying patches manually. You'd only need to set up the software once, and it will take care of the rest for as long as you use it.
Benefits of cybersecurity
By implementing the right cyber security solution, an organization can achieve the following 11 benefits:
Protect your business and your brand. A data breach can bring your operations to its knees and damage your company's reputation.
Improve business continuity by stopping attacks and eliminating downtime.
Protect your systems, network, and data from malware, ransomware, and phishing, DDoS, SQL injection, and social engineering attacks.
Protect critical data and personally identifiable information (PII) from unauthorized access, theft, and data leakage.
Meet the security requirements of compliance regulations, such as the EU General Data Protection Regulation (GDPR), California Consumer Privacy Act (CCPA), Payment Card Industry Data Security Standard (PCI DSS), Health Insurance Portability and Accountability Act (HIPAA), and ISO 27001.
Keep your website up and running. This is especially important for B-to-C companies that realize significant revenues from e-commerce sites.
Protect your employees' privacy and confidential employee information.
Gain the confidence of your customers, partners, and suppliers by demonstrating your commitment to security.
Achieve optimum productivity by eliminating unplanned downtime and ensuring the best possible system performance.
Eliminate the costs associated with a breach, including remediation costs and potential compliance fines.
Recover faster when a breach happens by getting visibility into how a data breach occurs.
What are the disadvantages of cyber security?
Even if cybersecurity solutions bring enormous benefits to users and organizations, they come with a few disadvantages depending on your point of view.
We will discuss the most common below and try to give you outs to counter them.
Keep in mind, we can safely label some of the disadvantages as "commonly perceived" but not necessarily damaging to companies or individuals. We will do our best to dissect them so you'd have an educated opinion.
Cybersecurity can be too expensive
Often, business executives feel they don't have the needed resources for a full-on cybersecurity strategy. Even if they have the funds, many companies may feel it's unnecessary to invest in a cybersecurity plan as cybercriminals have never attacked them.
The thing here is that cybersecurity, on its own, doesn't "print" money. A cybersecurity system is there to protect your data from attacks, but it can't generate revenue in the general sense of the term.
Nonetheless, take the time to calculate how much it would cost to rebuild your data due to a successful ransomware attack. You'd see that cybersecurity can save you a ton, even if it doesn't continuously generate funds.
Even if your business has never suffered from a malware hit, it only takes one successful attack to put your whole company on hold. Depending on its magnitude, a dedicated malware attack can gain access to some or all company data, break the trust of your customers, and even ask for a ransom to grant you back control over your files.
As for individual users, paying an extra monthly subscription fee may seem like a waste. After all, users can access free backup platforms (Google Drive, iCloud, DropBox) and can install free versions of respected antivirus software to counter evolving threats.
This is all well and good, but a deep look into "free" security solutions may prove otherwise. For example, free backup platforms don't pack enhanced cybersecurity features and don't take responsibility for keeping your data safe. Free antivirus software is good for "detecting" minor cybersecurity threats and potential attacks but it's hardly a viable threat response to any sophisticated attack on your system.
So, suppose you operate with sensitive data on your home network or have multiple computers on the same Wi-Fi. In that case, it's best to consider adding a cybersecurity solution to guard them all. Even if it's an extra expense, it may save your data from a nasty cyberattack in the long run.
How to flip it
The fix for this disadvantage is not often quick, but it's worth it if you go through with it.
The key element in the misconception of cybersecurity pricing is limited research. If your company takes the time to calculate potential losses due to a cyberattack – lost or corrupted data, downtime, customer satisfaction, etc. – the total costs of an attack would most probably exceed the agreed subscription fee for a robust cybersecurity solution.
After thorough research and planning, you could sensibly decide if the costs outweigh the risks or vice-versa. You will know why you need cybersecurity, when you might need it, and what it will bring to the table.
As for individual users, it's most efficient to count the potential weak spots a hacker can exploit on your home network. Those can be multiple devices connected to an older router, unsuspecting family members browsing unsecured sites, lack of patching habits, etc.
It's up to you to determine what number of potential exploits justifies a cybersecurity solution. Still, now, you'll be able to make an educated choice and find the best fit for your home network.
Cybersecurity can be challenging to set up
This disadvantage is more relevant for businesses rather than home users. As modern cybersecurity solutions offer intuitive software and an easy-to-use interface, individual users would be able to complete setup quickly, even if they don't consider themselves tech-savvy.
As businesses operate vast networks, with multiple servers and computers in an office (or in a BYOD environment), they'd need to coordinate cybersecurity implementation more thoroughly. (endpoint security, system updates, robust anti-ransomware tools, etc.)
The process can take time and effort and increase costs until the setup is complete. For SMBs, installing and configuring a cybersecurity solution may seem overwhelming, especially if they don't employ an IT specialist.
How to flip it
Here, the solution lies in thought before action. Proper planning can save companies immense resources in terms of time, effort, nerves, costs, and employee well-being. The same, even to a higher extent, is valid for critical infrastructure security projects.
If your organization decides to implement cybersecurity measures on the company network, the first step is to devise a plan. You can calculate how many machines would need to be comprised in the solution, what software could interfere with implementation, how many people you would need to take the process from start to finish, etc.
When you calculate the required actions, set timeframes to fulfill them, take into account potential setbacks, value in expected costs, etc., you'd be able to design a strategy and execute it without frustration.
Okay, there may be some frustration along the way, but if implemented adequately, the result will outweigh the hassle.
Cybersecurity requires regular monitoring (for businesses)
Home users can set up a cybersecurity solution without needing to check on it constantly. This is because if an error or an issue arises, they'd see it instantly on their computer.
Businesses, on the other hand, benefit from stricter monitoring schedules. For some organizations, these schedules may be deemed "regular", while others may require constant monitoring to ensure that the solution operates appropriately.
If you have a dedicated IT team, it shouldn't be a problem for them to assess the solution's performance and fix issues if such occur.
If you run an SMB, monitoring all cybersecurity tools may be more challenging, especially if you don't have an IT specialist on-premises.
If business processes run as usual and no threats target your SMB, you may be alright with just checking the daily summary of actions and performance reports for the solution. However, if a more exotic threat targets your business (it's a rare possibility, but it's still there), you may need to endure more continuous monitoring. The process may be tiresome, but it's worth going through.
After all, if you don't have a cybersecurity solution, most evolving threats on the web will be able to penetrate your defenses way easier. And if a sophisticated attack occurs, having no cybersecurity measures in place is way worse than having to monitor an active and comprehensive solution.
How to flip it
Here, the approach to improve monitoring lies in perception. Many businesses perceive cybersecurity as "overcomplicated technology", so any interaction with the solution may seem overwhelming.
As with any other topic, educating yourself and the employees responsible about the importance of cybersecurity can do wonders.
If businesses start accepting cybersecurity measures as part of the company, they can alleviate a lot of the frustration when dealing with modern systems. Even if the interface seems jumbled to some, it's actually quite user-friendly and intuitive. Taking the time to understand it will pay off in terms of work hours and meeting deadlines in the long run.
Moreover, if SMBs can squeeze it into their budget, a dedicated IT team (or a single person) can be responsible for all cybersecurity procedures. (at least at first)
With time passing, this team (or person) can educate the rest of your staff on sensible cybersecurity practices rather than just fixing issues if they arise. Once more (or all) people in your business understand how cybersecurity operates, the functionality issues will become fewer, and the overall attitude toward cybersecurity will grow fonder.
As for bigger companies and enterprises, it's crucial to dedicate specialists in different areas of your organization. Some may answer for cybersecurity updates and innovation implementation, others may monitor performance, and a third team can follow potential new threats and adjust the solution to counter them reactively.
Of course, all teams should maintain constant communication and work to improve their collaboration. With time, they can achieve excellence and become a hive mind of cybersecurity masters.
Cybersecurity requires continuous management (for businesses)
This point overlaps with the previous one up to an extent. The most common misconception about cybersecurity solutions is that they are a one-time thing. You install the solution, configure it, and let it do its magic.
While modern security solutions can run in the shadows without disturbing any business or day-to-day processes, business cybersecurity requires a certain level of management.
Suppose you're a part of a large company. In that case, your IT teams will need to develop the cybersecurity systems gradually, put fortified defenses in different business areas, and fix vulnerabilities as they arise.
For SMBs, the process may take less time (as your IT team would have fewer devices to set up), but management is still a part of maintaining a stellar cybersecurity strategy.
For individual users, managing the solution only occurs if you wish to change backup settings or specify threat detection to new preferences. Other than that, you can pretty much set up the cybersecurity program and only check up on it when auditing backups, for example.
How to flip it
Businesses determined to make cybersecurity work should calculate expenses, work hours, and teams required to manage their cybersecurity network.
As with monitoring, cybersecurity management prompts users to accept the solution as part of the organization. It's a working, moving, and evolving part of your company and should be treated as such.
Finding the right people to form responsible teams is critical to ease management and move forward to complete cybersecurity coverage for your organization. Ensuring their communication enables swifter implementation, fewer "unsolvable" issues, and higher security against potential known and unknown threats.
Cybersecurity can create new risks (for businesses)
If approached carelessly, cybersecurity solutions can generate new risks for companies. If your organization picks a solution based on, let's say, affordable pricing rather than functionality, your teams may lose precious time configuring a platform that performs poorly in protecting systems on your environment.
Moreover, some solutions may be incompatible with your organization's systems, leading to unintended security breaches, data loss, or data corruption. It may also halt business processes and worsen your revenue stream.
In addition, if you don't employ a respected, robust cybersecurity solution, cybercriminals can exploit a "less prepared" solution to infiltrate your company.
Lastly, if you don't go through with proper implementation, monitoring, and management, a cybersecurity solution may turn into a costly expense. You may find yourself paying for a solution without reaping any benefits due to a lack of proper configuration and continuous inspection.
How to flip it
Here, you can take a deep look into the previous sections and design a comprehensive cybersecurity plan. Take time to pick the most suitable solution for your needs and budget, implement it properly, and then hire (or train) responsible teams to constantly monitor, manage, and improve your organization's cybersecurity environment.
As with any innovation to a business, cybersecurity will require time, effort, and an extended workforce to bring it home. However, once you've created an adequate system to manage the solution, it will keep all of your data protected, both in real-time and in secure storage.
Cyber security automation and implementation
Cybersecurity automation is an important trend that is impacting the security landscape. Cybercriminals are incorporating automation and artificial intelligence (AI) to scale their attacks, while leading cyber security providers are quickly incorporating automation and AI into their solutions to improve efficiencies and improve response times. Cyber security automation eliminates the need for your IT team to manually sift through every alert to identify, triage, and act on a threat because the machine can automatically execute security actions – detection, investigation, analysis, and remediation – without human intervention – and do so in a matter of a few seconds.
Cyber security software that automates a response to a threat also eliminates errors and ensures that every threat is immediately detected and acted on. With the volume of alerts that come in, security analysts do not have the time or resources to manually analyze every threat, making it impossible to respond in real-time.
Automating security decreases the total cost of data breaches almost three times, but only 40% of organizations have partially deployed it and 35% of organizations have not even started implementing it.
Cybersecurity automation provides advantages to organizations looking to do more with less resources and reduce response times with automatic threat prevention capabilities.
Where is cyber security used?
As cybercrime is an increasingly threatening issue, security measures could be implemented in almost any internet-connected aspect.
Individuals can use cybersecurity to secure their own and work devices connected to a home network.
SMBs can meet regulatory compliance and ensure their business can grow in a safe environment. Larger companies can employ massive cybersecurity systems to counter DDoS attacks, ransomware hits, and other malware threats to stimulate competitiveness, a stellar revenue stream, and the potential to evolve continuously.
Governments could rely on the highest tier of cybersecurity to fight off known and unknown threats and ensure national and global security.
Non-profit organizations could benefit from a robust solution to keep their operational data, projects, and campaigns uninterrupted by ill-intended intruders.
Educational institutions can safeguard student records, academic research, and other intellectual property (IP) information.
Cybersecurity tools are applied to all internet-connected systems within the organization to ensure online and physical security against cyber attacks. The various features of a robust cybersecurity solution are able to monitor, detect, and prevent online threats due to the implementation of various algorithms.
Even if the term “cybersecurity” invokes anti-hacking associations, primarily, a comprehensive solution can aid in automated backups, mobile devices data protection, and disaster data recovery.
Organizations of various sizes and purposes can benefit from enhanced cybersecurity, as everyone, even casual internet users, carries sensitive information on their devices. And as they'd probably want that data to stay secure from cyberattacks, it's best to take the necessary precautions to guard it adequately.
What are the top cybersecurity challenges?
The following describes the cybersecurity challenges that a business faces, some of which can be addressed by using the right cybersecurity solution. Other challenges are outside the realm of technology but are important to consider and address where possible.
Software supply chain attacks are on the rise and if a cybercriminal invests enough time and money in a given target, any organization can be breached.
Malware gangs offer ransomware-as-a-service, allowing "distributors" to infect as many computers as possible with spam, phishing/account take-over/zero-day attacks, and spoofing.
Use of artificial intelligence (AI) and automation antes up the game as cybercriminals are now using modern technologies to scale their attacks.
Growing use of internet of things (IoT) devices means that a business may need multiple solutions to secure and protect different IoT devices. The security of IoT devices is still an immature market.
Limited budgets can restrict small-to-medium-sized businesses (SMBs) from making an investment in the right cybersecurity solution.
Insider threats can be stopped by the right cybersecurity solution, but businesses must be diligent when it comes to managing disgruntled or exiting employees who have legitimate access to sensitive data or PII(Protect sensitive and personally identifiable information).
A cybersecurity talent gap exists across the globe, and it is not expected to improve. In the U.S. alone, there were 7,956,341 employed cybersecurity experts employed from April 2020 through March 2021. Over the same period, there were 7,464,420 open positions.
Many businesses do not properly train IT staff and users on cybersecurity. Users need to know what attacks look like, what to do, and what not to do. Continuous security awareness training for IT staff and security professionals is just as important because the landscape changes fast and criminals are constantly introducing and perfecting new threat techniques.
Many organizations are unprepared for an attack. They have not developed (and tested) incident response plans and trained their IT staff on how to respond when a breach happens. With supply chain attacks increasing, both enterprise organizations and SMBs are at greater risk than ever before.
Not implementing a zero-trust approach puts an organization at risk. Zero trust means that you never trust anything or anyone inside or outside the network by default.
Many SMBs inadvertently misconfigure their cloud service, making their organization even more vulnerable to attacks. SMBs should engage a managed service provider (MSP) to ensure proper configuration.
What is the weakest link in information security?
To determine the weakest link in information security, we will need to examine the essence of all three cybersecurity pillars.
Technology
Technology doesn't make mistakes on its own. People are the ones who create, program and use technology to protect information. It does what people instruct it to do. Even when discussing artificial intelligence (AI), its algorithms are designed and programmed by people. (for now, at least)
Technology can "make mistakes" – security vulnerabilities in the software, for example, but those can be fixed easier due to sensible security patch updates. And again, the flawed nature of technology depends on the people who create it. It is then their responsibility to fix it if something goes wrong.
Processes
Processes, much like technology, don't "make decisions" on their own. People are the ones who design sets of steps to follow so they can ensure a consistent outcome over indefinite cycles.
If a process doesn't prove effective, people are responsible for reviewing it, pinpointing the issues, and developing a fix to update it.
People
Even if technology or processes can be labeled as "complex" by different users, people are the most complex of the three. Every person can think for themselves and make their own decisions.
Sometimes, the decisions are good regarding work productivity and business prosperity. Other times, they are not. In such cases, a machine or a process can aid in fixing the issue, but again, people are the ones who should drive the process to completion.
It's in our nature to make mistakes because we are responsible for finding a solution to an issue. Unlike machines, you can't predict if a person will make the same mistake again or not.
Even with the proper training and threat awareness, it's fundamentally uncertain if a person will always make the right decision, making humans the weakest link in the cybersecurity chain.
Let's explore the primary cybersecurity risks caused by humans below to understand how to counter them best.
Interacting with phishing emails
Cybercriminals take advantage of the trusting human nature and design attacks capable of enticing a click from unsuspecting users.
They play on our emotions, curiosity, and even fear to carry out malicious attacks. Phishing emails often invoke a sense of urgency, so the user won't have time to think through. In such a case, an employee can act hastily against their company's policies and thus grant control over the company network to unauthorized third parties.
The rise of bring-your-own-device (BYOD) environments adds to the impact of phishing attacks. Often, employees won't have top-tier cybersecurity tools on their personal devices, raising the risk of a successful malware attack even further.
Bypassing security controls
Most companies have strict internet usage policies. Such policies aim to restrict employees from accessing specific types of sites – gambling, adult consent, gaming, and P2P sharing sites are the most common in this list.
Suppose an employee goes against the internet usage policies. In that case, they will try to bypass the URL blockers (or other means of restricting website access) and expose your company's network to cyberattacks in the process. They can do so by using public proxy servers or unauthorized VPN services to download unsecured apps, connect to unsanctioned websites and cloud platforms, or go on a clicker rampage on malicious ads.
It's not always that gambling or gaming sites will harm your company's network, but P2P (peer-to-peer) sharing sites pose a significant risk, as it's not up to their creators to validate the contents of a downloadable file. Furthermore, P2P platforms are easiest to establish if the people behind them don't waste resources on secure file-sharing software or properly managed permissions.
Downloading unauthorized apps
Unauthorized apps are labeled as such for a reason. It's not that the app itself is malicious and capable of penetrating a company network. (although some apps are designed to do just that)
The risk with unverified apps comes from the poor security they offer.
Most app developers perceive cybersecurity as a low priority; despite the rise in app hacking attacks, most creators add security measures to their apps only if issues arise. (after the app is complete and already available to public use)
Apps can hold different types of user data – login info, credentials, usernames, passwords, email addresses, etc. Following a successful attack, cybercriminals can get ahold of all sensitive information on the app and exploit it to blackmail users, put the data on the black market, or turn the app into a gateway to a DDoS attack on a corporate network.
If an employee downloads an app with poor built-in cybersecurity, they create an exploitable vulnerability for hackers to use, especially if they use their mobile devices connected to the company's Wi-Fi network. The most common invitations to hack an app are the lack of multi-factor authentication (MFA), unsecured data storage, no data encryption enabled, or easily accessible code.
As popular apps are open for anyone to download, attackers can study their weak spots, design an attack, and strike when the gain potential is at its highest. So, even if an employee has downloaded an unsecured app and had it "safely" on their office computer for a month, the app can still pose great risks to your company network.
Using poor passwords
The modern technology landscape requires companies to adopt different platforms to conduct business optimally.
Nowadays, cloud-based technologies are the most common addition to a business's traditional tech environment. With them comes the need to create more accounts and, therefore, more passwords to authorize access.
The problem here lies in repetition. Most users prefer to use a simple password so they won't forget and have to reset it. In addition, they'd use the same simple password for multiple accounts to ease fast access. However, quick access for a user may sometimes mean quick access for perpetrators as well.
When users default to patterned passwords, they often rely on the following concepts:
- using numeric passwords (e.g., 123456789)
- including their name, the name of a loved one, their pet's name, hometown, etc. (e.g., Brian123, Milo007)
- using their birth year, favorite team's name, or other easily remembered combos (e.g., theKnicksrule1967)
As we've mentioned, these tricks are beneficial for always remembering your password, but they also invite threat actors to do a bit of digging on users and easily guess their passwords. If said passcodes are linked to a company-access account, they can quickly gain access to your corporate network.
Using weak authentication
The desire for quick access enables another vulnerability in account security.
As it's convenient to access a profile with as few steps as possible, some employees may find it irritating to go through MFA whenever they need to interact with an app or program.
Whether it's a code, a biometric scan, or another means of authentication, skipping MFA erases a step (or two) between the attackers and the data on company accounts.
Misconfiguration
Developers, system administrators, and other IT executives can also make mistakes. If a system admin forgets to change the default passcode for a server, cybercriminals may be able to access it more easily if they pinpoint the vulnerability.
Additionally, copy-pasting a configuration from one serverless function to another can raise the risk of a successful attack due to misconfiguration.
Another example is when a single IT specialist is responsible for the account login procedures for all other employees. As the person responsible would need to fortify every account on your premises, they can sometimes forget to secure an account or two, leaving vulnerabilities open for hackers to exploit.
What are the common attack types targeting users?
Below, you will find the three most common attack types reliant on human error to infiltrate critical systems.
Social engineering attacks
Such attacks are designed to exploit vulnerabilities in human nature. The most typical example is phishing attacks – they prey on people's fear, insecurity, or curiosity to entice a click on a fraudulent link or a ransomware download.
Malware and ransomware attacks
We've discussed the importance of immediate patching, but we will reiterate it here.
When users fail to apply security updates, they leave known vulnerabilities unpatched, and attackers can target those vulnerabilities to carry out a successful hit.
Patching common vulnerabilities and exposures (CVEs) can be time-consuming, so some users will put it on hold and continue using their machines without downtime. However, cybercriminals can use the period from when the patch is issued to when it's applied to penetrate the device's defenses.
Dictionary attacks
Dictionary attacks aim to infiltrate a password-protected device (or an account) by systematically attempting various known weak passwords. Even if attackers haven't researched thoroughly, they can find lists of commonly used passwords online and go through them to break into a device.
As challenging as these attacks can be, it's still people that enable them. When discussing insider threats for cybersecurity, we use the term "rogue employee" to best describe a person who invites cyberattacks, intentionally or not.
Below, we will explore the three primary types of rogue employees, discuss how they typically behave and what you can do to counter their actions.
The three types of rogue employees
Rogue employees undermine the SMB, enterprise, or organization they're part of by ignoring rules and security policies. Some may hide their actions to keep from being discovered, while others may break the rules in the open without concern for being scolded or fired.
The actions of such individuals may range from harmless to severe enough to invoke a critical security risk to your organization's data.
In the worst-case scenario, rogue employees can invite malware to "hop on" the company network, give business-essential data to competitors, or engage in corporate espionage.
Now, off to the three types.
The A-grade student
We bet every company has such an employee – they are ambitious, highly motivated, and resourceful. Their primary purpose is to get the job done. Their intentions are good, so they feel no harm is done if they break the rules to complete an assignment in optimal time.
Such employees perceive security rules as obstacles – they only slow them down and don't bring any value to the working process. This is why they believe that cybersecurity guidance is aimed only at less capable employees; having to comply as a part of the group irritates them.
The "Couldn't care less" employee
Such employees aren't trying to damage the company intentionally. They've just become accustomed to breaking the rules and security policies. They either don't understand the policies' purpose, don't comprehend the expected outcome, or are lazy and oblivious to potential cybersecurity threats.
A common perk for "couldn't care less" employees is leaving their login ID and passcode on a sticky note, stuck on their monitor. They could also occasionally share sensitive company data in an email without being asked to.
The "Grudge"
Disgruntled employees may bring the most significant risk to a company. They could be holding a grudge (due to various reasons) and try to harm the organization in resourceful ways; they can steal company data, leak classified information, or enable a massive cyberattack from the inside.
How do rogue employees bypass security controls?
Organizations implement excessive restrictions to protect information and reduce the potential attack surface for criminals to exploit.
A rogue employee would need to bypass security protocols to access data they're not supposed to. The typical approach to go around the rules involves proxies and VPN services.
Rogue employees can rely on the following:
Proxy – Forward Proxy, Transparent Proxy, Public Proxy, Anonymous Proxy, High-Anonymity Proxy
Virtual Private Network (VPN) – PPTP, L2TP/IPSec, OpenVPN, SSTP, Wireguard
Tor (the Onion Router)
All methods ensure a high level of privacy, as they grant anonymous access to the internet. (with the Tor Browser guaranteeing the highest level of anonymity)
In using either a proxy, VPN, or Tor, employees become insider threats (up to a different extent) by exposing the organization to malicious sites or data exfiltration.
How to counter rogue employees and protect your company data?
Ensuring your data's security against rogue employees falls upon the cybersecurity professionals in your employ. (or yourself, if you are the responsible person in your organization)
The key here is to find the optimal balance between "poor security" and "too much security".
In essence, your company's security policies shouldn't enable easy unauthorized access while remaining compact enough not to halt user activities.
We know that's easier said than done, but with the proper research, implementation, and education, your company can become a stronghold without imposing a sense of tyranny.
Employee education and security awareness training
Is cybersecurity important for your employees?
We're not talking about their ability to pass employee training with flying colors. We've already discussed that, but now, we want to emphasize the importance of active education rather than simply imposing rules to follow. The proper educational campaigns can minimize the damage from phishing, reduce the impact of ransomware attacks, avoid suspicious link clicking, and keep company data away from prying eyes.
You can start the education by explaining the warning signs of a cyberattack. Then, discuss how to spot phishing emails, malicious links, and ransomware attempts. Explain to your employees what to do upon detecting known threats and, more importantly, why they should do it.
It's critical for your employees to understand the consequences should an attacker steal sensitive data.
Understanding that a single phishing attachment can wreak havoc across your entire network would mean downtime for the business, increased expenses to recover crucial data, and, ultimately, the risk of losing job positions until the company bounces back.
You can conduct intensive mock "phishing" campaigns to see which employees take the bait. However, scolding the employees who interact with the bogus emails is not optimal. It's essential to explain to them that most too-good-to-be-true deals in emails are phishing attempts.
And those phishing attempts won't bring anything beneficial to them but rather harm the company and increase work hours to recover data and hassle to keep the business going during and following a data breach.
Another good practice is to take the time to train each employee for the best threat response practices regarding their own computers. It may seem redundant, but the comfort of a known device will help them remember potential threats after seeing them appear on a familiar screen.
You can also go through explaining why unauthorized websites are harmful – don't focus on your opinion towards gambling, gaming, or adult consent sites but draw a relation between unverified websites and the immediate risk to cybersecurity.
All in all, cybersecurity education is fundamental to maintaining data security within your organization. Nonetheless, it is not enough to counter every potential rogue employee.
This brings us to the next section.
Policy enforcement and monitoring
Some phishing campaigns are so sophisticated that they can fool even a trained eye. This is why policy enforcement and monitoring are critical.
First and foremost, you should ensure that web security policies, web filtering, and firewalls are enabled on your company network.
Secondly, you should block proxy, VPN, and Tor access. (unless your company requires the use of any of the three)
You can implement app controls to deny the installation of the Tor Browser or use your network security system to detect Tor traffic. In addition, you should restrict access to public proxies (and VPNs) – even if an employee has a valid reason to use them, they shouldn't do it unless your company relies on such services.
You can use a traffic tracker solution to inspect packets on your network. (or rely on an in-house solution, if available)
Such solutions can detect obfuscated proxies, VPN, and Tor traffic. You can also “catch” and block any activity carried out over a proxy, VPN, or Tor.
If your system administrators detect and block suspicious traffic, it's best to discuss this with the employees involved. Simply blocking their actions could mean they will make another attempt the day after. Or in a few hours. Or in a few minutes, for the most eager ones.
It may sound as if you're educating a child, but in the ever-expanding world of cybersecurity, everyone could learn a thing or two, even the most well-read experts.
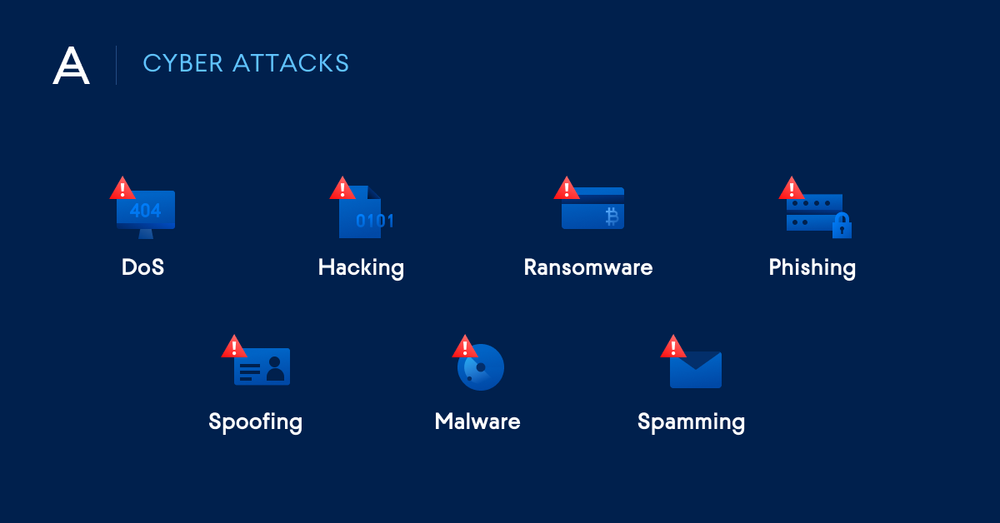
Examples of cybersecurity threats
There are many types of cyber threats — malicious acts that threaten to damage or steal data, or to otherwise disrupt workloads and services. No matter the type or the origin, such threats are a serious hazard to business health and operations. Some of the more common variations include:
"Different types of cyber attacks - DoS, Hacking, Ransomware, Phishing, Spoofing, Malware, Spamming"
Malware
Malware — shorthand for "malicious software" — is an application that's intended to cause damage to computer systems, steal data, gain unauthorized access to networks, or otherwise wreak havoc. Malware infection is the most common type of cyberthreat. While it's often employed for financial gain, malware is also used as a weapon by nation-states, as a form of protest by hacktivists, or to test the security posture of a system.
Malware is a collective term and refers to a number of types of malicious software variants, including:
Viruses — the most common form of malware. Much like their biological namesake, viruses attach themselves to clean files, replicate, and spread to other files. They may delete files, force reboots, join machines to a botnet, or enable remote backdoor access to infected systems.
Worms — similar to viruses, but without the need for a host file. Worms infect systems directly and reside in memory, where they self-replicate and spread to other systems on the network.
Backdoors — a stealthy method of bypassing normal authentication or encryption. Backdoors are used by attackers to secure remote access to infected systems, or to obtain unauthorized access to privileged information. While many backdoors are strictly malicious, deliberate variants may be built into hardware or operating systems for legitimate purposes — such as restoring access to a user who has forgotten their password.
Trojans — named for the famous wooden horse from the story of the Trojan War. Trojans may disguise themselves as a legitimate application, or simply hide within one. They discretely open backdoors to give attackers easy access to infected systems, often enabling the loading of other malware.
Ransomware
Ransomware is also a form of malware, though one that warrants special focus due to its ubiquity. Originally, ransomware was designed to encrypt data and lock victims out of their systems — that is, until they paid their attackers a ransom in order to restore access. Modern ransomware variants tend to take this a step further, with attackers exfiltrating copies of the victim's data and threatening to release it publicly if their demands are not met. This usually increases the pressure on victims considerably, as stolen data often contains personally-identifiable information (PII) of customers and employees, sensitive financial details, or trade secrets.
Ransomware distribution campaigns often rely on social engineering techniques such as phishing, tricking users into downloading a dropper that retrieves and installs the payload. More aggressive ransomware variants, such as NotPetya, exploit gaps in security to infect systems without the need for trickery.
Once on the system, ransomware finds all files of a specific type locally and across the network, encrypting — and often stealing — them. The original files, recovery points, and backups are then deleted to prevent users from restoring the system on their own. Ransomware usually changes the file extension, (e.g. myFile.doc.encrypted) and adds a "help" file, explaining how victims can pay to recover their data.
Phishing (for sensitive data)
Phishing is a common attack technique, and a form of social engineering: the strategy of manipulating people into taking unsafe actions or divulging sensitive information.
In phishing campaigns, cyber attackers use deceptive communications — email, instant messages, SMS, and websites — to impersonate a trustworthy person or organization, such as a legitimate business or government institution. Taking advantage of users' trust, attackers trick them into clicking malicious links, downloading malware-laden attachments, or disclosing sensitive personal information to enable financial misconduct or identity theft.
A more focused approach is "spear phishing", in which attackers target a specific individual — or a small group of individuals, such as employees in a specific role at a specific company. These cyber threats are generally tailored to their target based on insider knowledge or information available on the web (e.g. through social media). As an example, an attack might be directly addressed to the victim and disguised as an email from their direct manager or their company's IT department. Though they require extra effort to create, spear phishing attacks tend to be quite convincing and are more likely to succeed.
Distributed denial of service (DDoS) attacks
Distributed denial of service attacks target servers, services, or networks in order to disrupt traffic flow, preventing users from accessing these resources. DDoS attacks are most commonly intended to cause financial or reputational damage to an organization or government body.
Such cyber attacks often use large networks of malware-infected systems — both computers and IoT devices — that the attacker controls. Individual devices in these security networks are commonly referred to as "bots" (or "zombies"), and a collection of them is known as a "botnet".
Attackers use these botnets against servers or networks, having each bot send repeated requests to the target's IP address. This ultimately causes the server or the network security to become overloaded and unavailable to normal traffic. Remediation is usually difficult, as the bots are legitimate Internet devices — making it hard to separate the attackers from innocuous users.
SQL injection (SQLI)
Structured Query Language (SQL) is a standard language for building and manipulating databases, often used in web and other servers. SQL injection attacks insert malicious SQL code into a server, manipulating it to display database information that the attacker shouldn't be authorized to access. This information may include sensitive corporate data, user credentials, and employees' and customers' PII(Protect sensitive and personally identifiable information).
While SQL injection can be used to attack any SQL-based database, such techniques mainly target websites. A malicious actor could carry out an attack simply by submitting an SQL command into a vulnerable website's search box, potentially retrieving all of the web app's user accounts.
Social Engineering
This is the practice of duping an individual – in person, on the phone, or online – into doing something that makes them vulnerable to further attacks. In the digital world, it is easier to trick people into falling into online traps than it is in real life, making the online approach a prevalent and dangerous practice.
SE takes advantage of people's emotions to make them do something so that a criminal can gain physical access to private offices and buildings and/or online access to a company's systems. Here are some common techniques that these criminals use to dupe individuals, get the information to launch further attacks, extort credentials, and/or steal data or money.
How to manage cyber security?
Cyber threats, then, are one of the biggest issues facing businesses and individuals alike. And cyber security is concerned with defending networks, computer systems, and applications against these threats. But it's important to note that cyber security is not the same thing as data protection.
Data is now the world's most valuable resource. It's at the core of business operations, and data volumes in need of protection are growing at explosive rates. Cyber security helps protect the systems that make it possible to generate, manage, store, and transfer data. It doesn't address data itself — backups, authentication, masking, or erasure. If data is encrypted, altered, or deleted, a standalone cyber security solution can't do much to help you restore it in a timely fashion.
That's why Acronis recommends solutions built with cyber protection — an integrated approach that combines cyber security with data protection — as the driving force:
- Acronis Cyber Protect Cloud — a platform that enables service providers to deliver cyber protection in an easy, efficient and secure way. With one solution, users gain access to cloud backup, cloud disaster recovery, ransomware protection, file sync and share, and blockchain-based file notarization and e-signature services, all managed from a single console.
- Acronis Cyber Protect — a single solution integrating backup with next-generation, AI-based antimalware and protection management. The integration of multiple protection technologies not only increases reliability — it also decreases the time required to learn, deploy, and maintain new capabilities. With Acronis Cyber Protect, users enjoy complete cyber protection against modern threats.
- Acronis True Image — the only personal solution that delivers easy, efficient, and secure cyber protection through with a unique integration of reliable backup and cutting-edge antimalware technologies — safeguarding data against all modern threats. Reduce the complexity and cost of safeguarding data, so you’ll never have to worry about disruptions to your digital life.
The cyberthreat landscape is vast and constantly evolving. Standalone cyber security and data protection solutions are helpful in securing workloads, but they leave gaps in your defenses. A multilayered approach incorporating the latest cyber security technology alongside data security and authentication is necessary to provide reliable protection for modern workloads across multiple domains.
Want to dive deeper? Check out The Ultimate Cyber Insurance Coverage Guide for MSPs to better understand how to navigate policies, coverage requirements, and risk management strategies tailored for IT service providers.
About Acronis
A Swiss company founded in Singapore in 2003, Acronis has 15 offices worldwide and employees in 50+ countries. Acronis Cyber Protect Cloud is available in 26 languages in 150 countries and is used by over 21,000 service providers to protect over 750,000 businesses.



