- Stop phishing and spoofing attemptsMinimize email risk for clients with powerful threat intelligence, signature-based detection, URL reputation checks, unique image-recognition algorithms, and machine learning with DMARC record checks.
- Catch advanced evasion techniquesDetect hidden malicious content by recursively unpacking embedded files and URLs and separately analyzing them with dynamic and static detection engines.
- Prevent APTs and zero-day attacksPrevent advanced email threats that evade conventional defenses with a unique CPU-level technology able to act earlier in the attack chain to block exploits before malware is released, delivering a clear verdict within seconds.
Better security for your clients’ critical cloud collaboration applications.
Email is the biggest threat vector for your clients - neutralize it and minimize risks in email communication with a unique technology. Email Security enables you to offer more thorough cyber protection without increasing your management burden.
On-demand trainings

Acronis partners share their success stories
Build your services on a leading email security solution in SELabs evaluations
Replace the inefficient security stack of sandboxes and content disarm and reconstruction technologies (CDRs) with a multi-layered email security solution for lightning-fast detection that’s easy to deploy and manage.
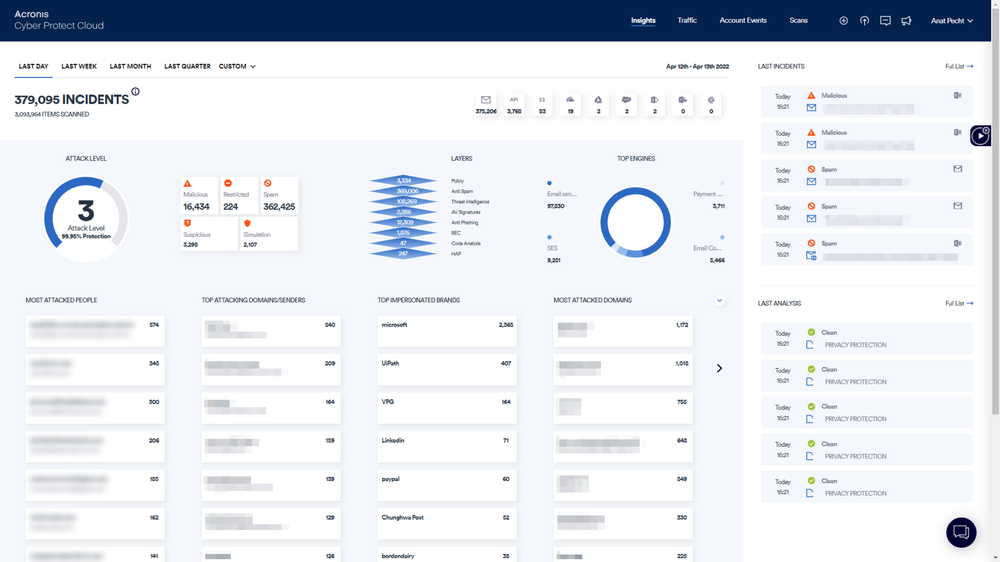
Scan 100% of traffic in real-time
Scan content across inbound and outbound emails, and prevent lateral movement. Unlike legacy sandboxing solutions, every bit of content - emails, files, and URLs - is analyzed at any scale.Prevent APTs and zero-days
Block sophisticated threats that evade conventional defenses such as APTs and zero-day attacks with a unique CPU-level analysis that allows action earlier in the attack chain than other technologies.Effortless, rapid deployment
Cloud-native deployment that integrates directly with the email system without additional configurations, including API-based for Microsoft 365. Reduce the administrative burden associated with a standard secure email gateway (SEG) deployment.Incident response services
Empower your service delivery and security teams with direct access to cyber analysts and email security experts that monitor all customer traffic and analyze malicious intents with ongoing reporting and support.Unmatched detection speed
Leverage an unmatched detection speed that allows you to prevent all threats before they reach end-users, compared to the reactive approach of standard email security technologies.
Upcoming online events
Stop email-borne threats before they reach end-users
Proven regulatory compliance




Clients are increasingly dissatisfied with the native defense capabilities of Microsoft 365, as they are slow in detection and unable to prevent more advanced attack techniques. Email Security ensures all email-borne threats are blocked in seconds.
| Detection speed | < 30 sec | 5-20 min |
| Detection accuracy | Best-in-class | Good |
| Threat coverage | Best-in-class | Good |
| Detection of malicious URLs | Best-in-class | Average |
| Detection of zero-days | Best-in-class | Limited |
| Prevention of APTs | Included | N/A |
| Prevention of ATO | Included | Add-on |
| Anti-evasion | Included | Below average |
| Incident response services | Included | N/A |
Protect not just emails, but clients’ riskiest collaboration tools
Protect clients’ collaboration apps, increasingly exploited in attacks with prioritized patching and exploit prevention. Leverage Acronis Cyber Protect Cloud, integrating backup and disaster recovery, next-generation anti-malware, and cyber protection management.
- Microsoft 365 outbound email scanningReduce reputational risks for clients by detecting malicious emails originating from their mailboxes via Microsoft 365 API-based scanning. Also enhances inbound protection accuracy through analysis of communications with external parties.
- UniqueX-ray insightsLeverage a holistic view of the threat landscape across organizations with forensics data for each client and email, proactive insights on threats a targeting clients and most risky attack patterns, and analysis of any file or URL on which your team needs forensics.
- Incident response serviceGain direct access to cyber analysts that act as an extension of your service delivery team, monitor all customer traffic, and analyzing malicious intents with ongoing reporting and 24/7 support, including handling false positives, remediating, and releasing as required.
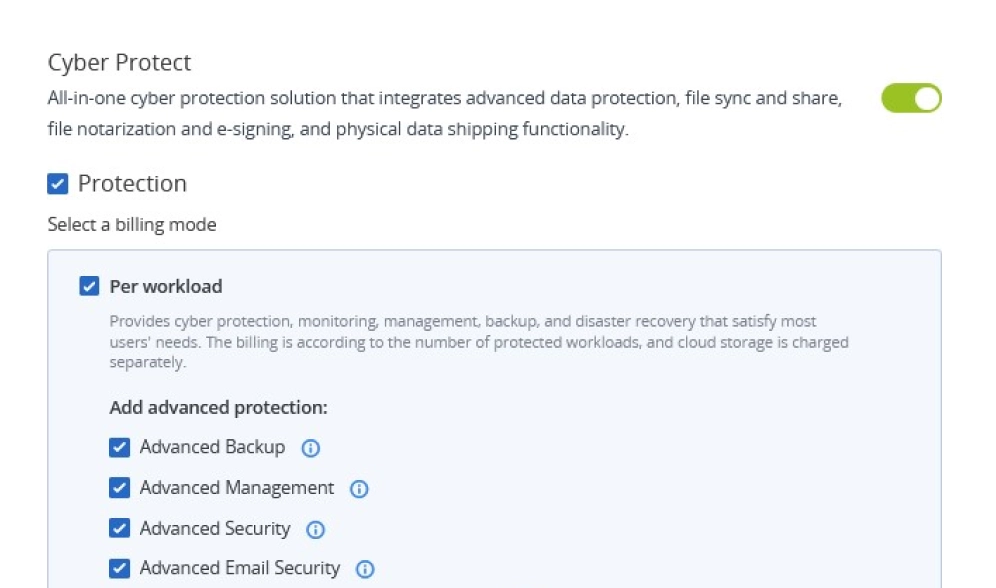
Expand your services with advanced protection packs
Add other powerful components to strengthen your services even further with advanced protection packs and unique cyber protection capabilities. Control your costs by paying only for the functionalities your clients need.
- Security + XDRInstead of counting on a costly and complex stack of point solutions, Acronis XDR introduces natively integrated, highly efficient protection built for MSPs:
- Natively integrated cybersecurity, data protection and endpoint management
- Highly efficient security designed to protect the most vulnerable attack surfaces with AI-guided incident analysis and single-click response
- Built for MSPs, including a single agent and console for all services
- Security + EDRInstead of counting on a costly & complex stack of point solutions, Acronis enables MSPs via integration of EDR, endpoint management, and backup & recovery to:
- Easily launch a complete security solution, including rapid recovery
- Protect against modern threats and readily comply with cyber insurance requirements
- Maximize efficiency through a single security platform
- ManagementStreamline and automate your routine tasks via scripting and promptly close security gaps in clients’ infrastructure through patch management. Gain visibility into your clients’ software assets and data protection to ease daily tracking and planning tasks, and improve clients’ uptime by monitoring disk drives health.
- Cyber scripting
- Automated patch management
- Disk drive health monitor
- AutomationStreamline MSP business with a single integrated platform that automates workflows, improves customer interactions, and provides real-time business insights. Enable data-driven decisions and smarter resource utilization, resulting in improved manageability and value-based client relationships.
- High-performance automation
- Precise forecasting
- Next-level profitability
- Advanced BackupDefend clients’ data, even between scheduled backups. Extend backup capabilities to SAP HANA, Oracle DB, MariaDB, MySQL, and application clusters. You can also gain visibility into data-protection statuses across your clients’ infrastructure.
- Continuous data protection
- Data protection map
- Off-host data processing
- Disaster RecoveryGet clients back to business in mere minutes when disaster strikes by spinning up their systems in the Acronis Cloud and restoring them anywhere, ensuring immediate data availability. Make disaster recovery painless and increase efficiency with orchestration, runbooks, and automatic failover.
- Disaster recovery orchestration
- Production failover
- Site-to-site VPN
- Email SecurityBlock any email threat, including spam, phishing, business email compromise (BEC), account takeover (ATO), advanced persistent threats (APTs), and zero days in seconds before it reaches end users. Leverage Perception Point’s next-generation technology for lightning-fast detection and easy deployment, configuration, and management.
- Anti-phishing and anti-spoofing engines
- Anti-evasion and account takeover protection
- Next-generation dynamic detection against zero-days
- Data Loss Prevention (DLP)Prevent leakage of sensitive data from endpoints via more than 70 local and network channels and strengthen compliance with minimal effort and speed to value.
- Content-aware data loss prevention
- Automatic client-specific DLP policy creation and extension
- Pre-build data classifiers for common regulatory frameworks
- File Sync and ShareGet a full control over data location, management and privacy with a file sync and share service, including a transaction ledger to enable notarization and eSignature capabilities, across all platforms.
- File notarization
- Embedded eSignatures
- Independent file verification
Learn More, Earn More with Acronis Academy
Whether you and your team are seeking professional certifications or starting an MSP business, we're here to support you at every stage.

Start learning for Free
New! MSP Academy offers budding and seasoned MSP professionals vendor-neutral training covering the A-Z of managing a successful MSP business.
Train on-demand
Access our most popular sales and technical training courses designed for existing MSPs looking to enhance their cybersecurity skills and knowledge.
Login to Partner Portal
Available exclusively to Acronis Partners. Access our complete Acronis Academy training catalogue and earn your required certifications.
Looking for help?
Frequently Asked Questions
What features are included in Email Security?
Email Security, powered by Perception Point, helps prevent all email-borne threats, including spam, phishing, BEC and impersonation attempts, ATO, malware, APTs, and zero days before reaching end users with multiple protection layers. It also enhances compliance and increases visibility into all actions performed by the admin users and the Incident Response team with a comprehensive audit log.
The anti-spam engines act as the first line of defense, applying anti-spam and reputation-based filters, including IP reputation checks, to email upon receipt — to block malicious or unwanted communication.
All emails are then recursively unpacked into smaller, individual components like URLs and files by anti-evasion technology. This process detects malicious embedded or hidden content. The URLs and files are separately run in multiple versions and patterns through the subsequent security layers to catch any hidden threats.
Email Security leverages powerful threat intelligence from six market-leading sources, combined with Perception Point’s technology that scans URLs and files in the wild to stay ahead of emerging threats.
Anti-phishing engines apply URL reputation filtering from four market-leading sources, combined with a unique image recognition technology that detects unknown, malicious URLs based on logos and images used on the webpage.
To catch payload-less attacks (BEC), such as impersonation attempts, look-alike domains, and display-name deceptions, Email Security leverages machine learning algorithms with IP reputation, sender policy framework (SPF), DomainKeys Identified Mail (DKIM), and Domain-Based Message Authentication Reporting and Conformance (DMARC) record checks.
In order to prevent ATO, Email Security stops attackers from infiltrating the organization via credential phishing, analyzes end user patterns and behaviors to detect anomalies, prevents attackers from spreading malicious content to other users, and provides incident management of every account takeover attempt.
Known malware is stopped with the help of best-in-class, signature-based detection technologies, specifically developed to prevent email-borne threats, that act as another layer of protection on top of users’ local anti-malware solution.
The last line of defense is the next-generation dynamic scanning that prevents advanced threats that evade conventional defenses such as zero days and APTs. The unique, CPU-level technology acts earlier in the kill chain than any other solution to block attacks at the exploit phase by analyzing the applications’ execution flow during runtime to identify deviations from standard flow based on assembly code.
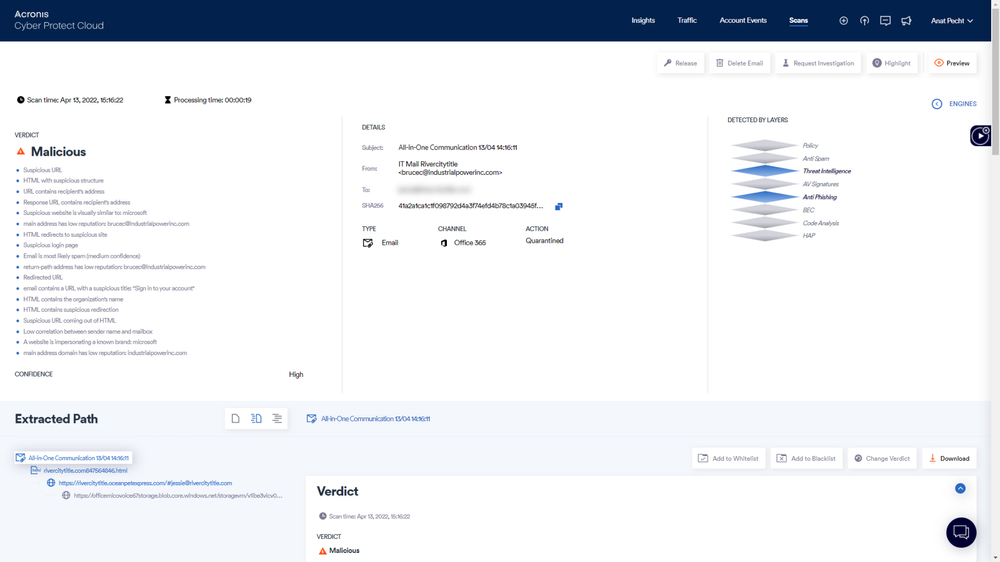
Moreover, service providers have access to a dashboard that provides a holistic view of the threat landscape across organizations with forensics data for each email, proactive insights on threats seen in the wild, and analysis of any file or URL on which the service delivery team needs forensics.
With the incident response service, you also gain access to cyber analysts that monitor all customer traffic and malicious intent with ongoing reporting and ongoing support, including handling false positives, remediating, and releasing when required.
How easy is it to migrate to Email Security from another solution?
If you choose to migrate to Email Security from another solution, the process of upgrading your services is as seamless as possible. Email Security is an API-based email security technology that integrates directly into the email system without the need for any additional configuration, including configuring MX records.
If you already use Acronis Cyber Protect Cloud, implementing Email Security happens with the flip of a switch.
Will Email Security affects clients’ email delivery?
Due to the unmatched detection speed, which is up to a few seconds, compared to seven to 20 minutes for legacy sandboxing solutions, all emails are scanned before delivery to end users with near-zero delays to ensure proactive protection without disrupting every day business process.
What is email security?
Email security ensures the availability, integrity and authenticity of email communications by detecting and blocking email threats to reduce the risks of email-borne attacks.
What are some types of email security threats?
Email security threats come in many forms:
- Spam is any type of unwanted, unsolicited digital communication that is sent out in bulk.
- Phishing is a common attack technique that utilizes deceptive communications (including email, instant messages, SMS, and websites) from a seemingly reputable source in order to gain access to sensitive information.
- Business email compromise (BEC) involves phishing emails that use impersonation and company knowledge to trick employees to wire money or data, or to change bank account information.
- Account takeover (ATO) also known as account compromise, occurs when a cyber attacker gains control of a legitimate account. Once they have control of an account, they can launch a variety of attacks, such as supply-chain phishing, data exfiltration, financial fraud, etc.
- Malware is an application written with the intent of causing damage to systems, stealing data, gaining unauthorized access to a network, or generally wreaking havoc.
- Ransomware is a form of malware that infects systems and encrypts files. The user cannot access their data until a ransom is paid in exchange for a decryption key. Once the ransom is paid, a user can only hope that the attacker will provide the decryption key and permit them to regain access to their files.
- Advanced persistent threats (APTs) are complex attacks intended to establish an illicit, long-term presence in a network in order to collect highly sensitive data or compromise an organization’s operability.
- Zero-day exploits refer to a vulnerability that is actively being exploited in the wild, but is not yet known to the software provider. Thus, a software patch to fix the exploit is unavailable.
Is email security important?
Email is the primary attack vector, with 94% of malware being delivered via email, according to a 2019 Verizon Data Breach Investigations Report. More recent reports from Verizon, HP and Acronis still point to email as one of the most common entry points for attacks.
Cybercriminals will continuously target business’ email accounts, attempting to open a backdoor and infiltrate an organization’s network. That’s why it is vital to secure your clients’ riskiest communication channel. It’s important to note that no matter how trained an employee is, they receive hundreds of emails a day and with email exhaustion, they can inadvertently click on a malicious email.
Do MSPs need email security?
Amidst the rising number of digital threats, more service providers are seeing cybersecurity as their primary revenue generator. Email security is an essential service for the majority of businesses as email is still the most used communication channel and the primary channel cybercriminals attack.
To remain competitive and reduce security risks for clients, service providers must offer a portfolio of services with multiple defense layers, including email security. Launching such a service can help MSPs increase their client base and increase per client revenues.
What languages are available in the Email Security management console?
Email Security management console UI is available in these languages: English, Spanish, German, French, Italian and Portuguese.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.