- Protection for sensitive data across 70+ channelsProtect clients’ sensitive data — prevent data leakage from workloads via peripheral devices and network communications by analyzing the content and context of data transfers and enforcing policy-based preventive controls.
- Automatic, behavior-based DLP policy creation and extensionNo need to drill down into client business details and define policies manually. Automatically baseline and profile sensitive data flows to create and continuously adjust DLP policies to ever-changing business specifics, ensuring protection against the most common causes of data leaks.
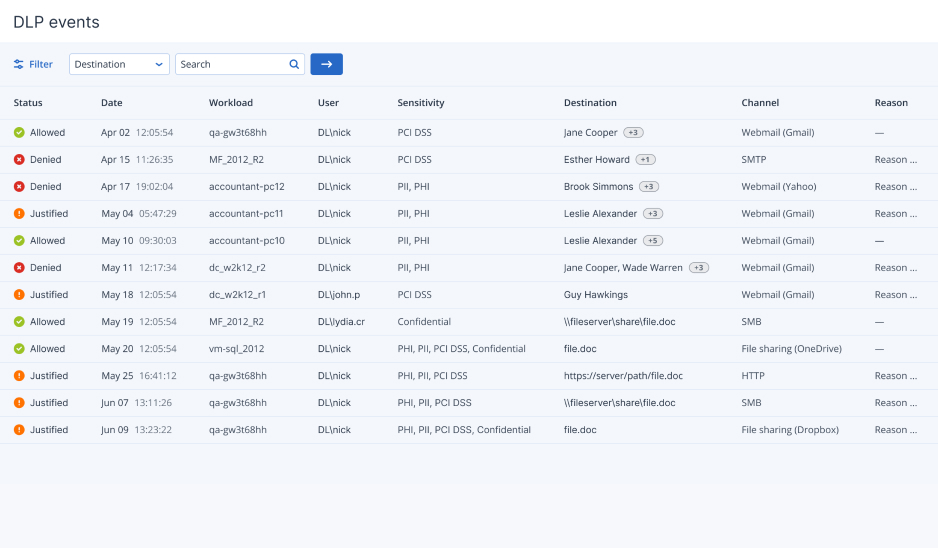
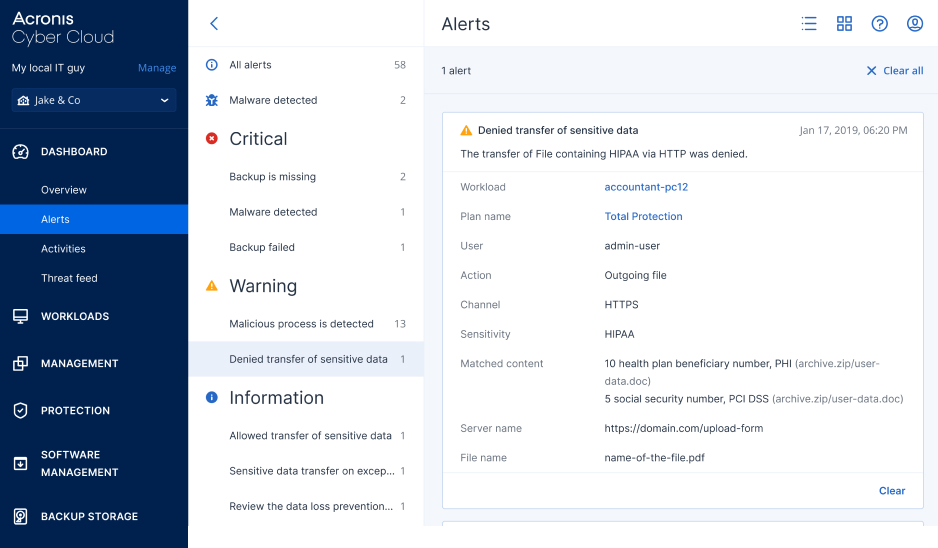
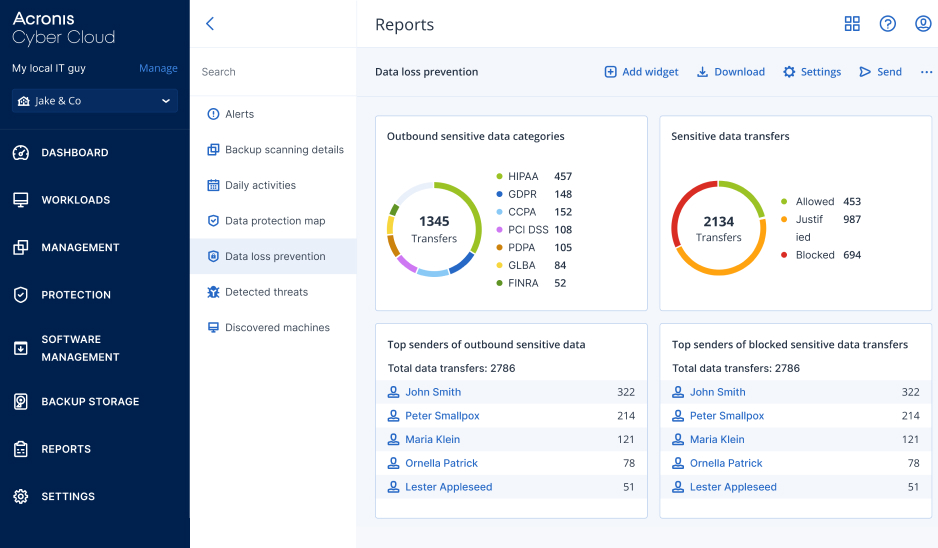
- Prompt reactiveness to DLP eventsEnable rapid response and forensic investigations and simplify DLP policy maintenance via centralized audit logs and alerts on security events. Ease reporting with information-rich widgets.
Strengthen your clients’ regulatory compliance out of the box
Leverage pre-built data classifiers for most common regulatory frameworks protecting personally identifiable information (PII), patient health information (PHI), cardholder data, and documents marked as confidential.



On-demand trainings

Ensure faster growth with Acronis
Expand your portfolio with a DLP service that’s easy to launch and manage
Upcoming online events
Differentiate your DLP services with an edge over the competition
Current DLP solutions require costly security expertise and deep knowledge of clients’ business processes, together with complex, error-prone, manual configuration to ensure client-specific policies. With DLP, you can prevent data leaks for clients with the provisioning speed and policy management ease you need.
Automated DLP policy creation
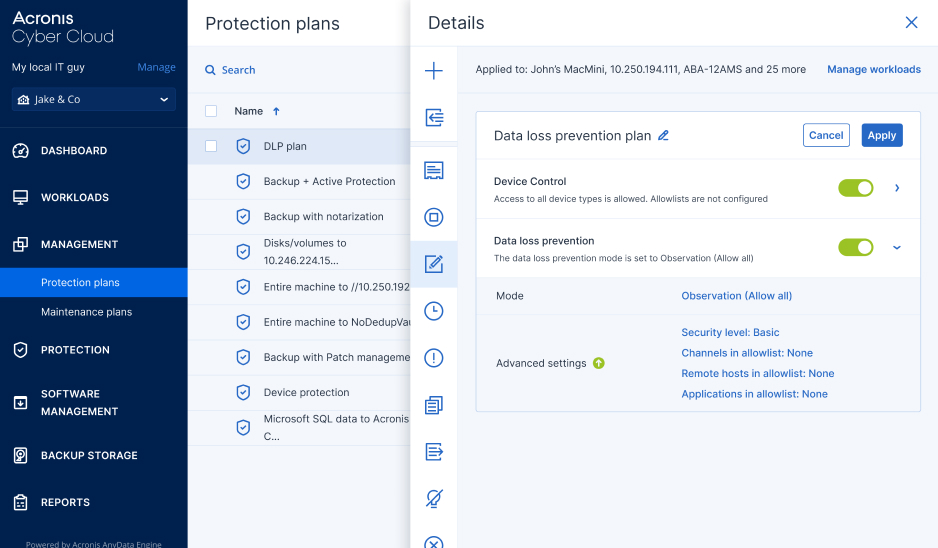
Minimize manual work and the risk of error. Simplify provisioning by automatically creating an initial DLP policy for each client with a behavior-based approach.Client-specific DLP policies
Baseline and profile outgoing sensitive data flows across organizations to automatically map clients’ business processes to a DLP policy — adjusted to their specifics. Leverage optional end-user assistance for higher accuracy, and request client validation before enforcing a policy.70+ controlled channels
Control data flows across most common local and network channels, including removable storage, printers, redirected mapped drives and clipboard, emails and webmails, instant messengers, file sharing services, social networks, web access, and network protocols.Unmatched DLP controls to differentiate your service
Ensure web-browser-independent control of data transfers to social media, webmail and file-sharing services. Leverage content inspection of outgoing instant messages and sensitive data detection in images sent from remote and offline computers.Centralized cyber protection with single console
Control your TCO, reduce management overhead and boost margins by using a single solution that integrates backup, disaster recovery, next-generation anti-malware, email security, workload management, and data loss prevention.
Prevent data leakage and strengthen compliance with the ease and speed you need
Expand your services with advanced protection packs
Add other powerful components to strengthen your services even further with advanced protection packs and unique cyber protection capabilities. Control your costs by paying only for the functionalities your clients need.
- Security + XDRInstead of counting on a costly and complex stack of point solutions, Acronis XDR introduces natively integrated, highly efficient protection built for MSPs:
- Natively integrated cybersecurity, data protection and endpoint management
- Highly efficient security designed to protect the most vulnerable attack surfaces with AI-guided incident analysis and single-click response
- Built for MSPs, including a single agent and console for all services
- Security + EDRInstead of counting on a costly & complex stack of point solutions, Acronis enables MSPs via integration of EDR, endpoint management, and backup & recovery to:
- Easily launch a complete security solution, including rapid recovery
- Protect against modern threats and readily comply with cyber insurance requirements
- Maximize efficiency through a single security platform
- ManagementStreamline and automate your routine tasks via scripting and promptly close security gaps in clients’ infrastructure through patch management. Gain visibility into your clients’ software assets and data protection to ease daily tracking and planning tasks, and improve clients’ uptime by monitoring disk drives health.
- Cyber scripting
- Automated patch management
- Disk drive health monitor
- AutomationStreamline MSP business with a single integrated platform that automates workflows, improves customer interactions, and provides real-time business insights. Enable data-driven decisions and smarter resource utilization, resulting in improved manageability and value-based client relationships.
- High-performance automation
- Precise forecasting
- Next-level profitability
- Advanced BackupDefend clients’ data, even between scheduled backups. Extend backup capabilities to SAP HANA, Oracle DB, MariaDB, MySQL, and application clusters. You can also gain visibility into data-protection statuses across your clients’ infrastructure.
- Continuous data protection
- Data protection map
- Off-host data processing
- Disaster RecoveryGet clients back to business in mere minutes when disaster strikes by spinning up their systems in the Acronis Cloud and restoring them anywhere, ensuring immediate data availability. Make disaster recovery painless and increase efficiency with orchestration, runbooks, and automatic failover.
- Disaster recovery orchestration
- Production failover
- Site-to-site VPN
- Email SecurityBlock any email threat, including spam, phishing, business email compromise (BEC), account takeover (ATO), advanced persistent threats (APTs), and zero days in seconds before it reaches end users. Leverage Perception Point’s next-generation technology for lightning-fast detection and easy deployment, configuration, and management.
- Anti-phishing and anti-spoofing engines
- Anti-evasion and account takeover protection
- Next-generation dynamic detection against zero-days
- Data Loss Prevention (DLP)Prevent leakage of sensitive data from endpoints via more than 70 local and network channels and strengthen compliance with minimal effort and speed to value.
- Content-aware data loss prevention
- Automatic client-specific DLP policy creation and extension
- Pre-build data classifiers for common regulatory frameworks
- File Sync and ShareGet a full control over data location, management and privacy with a file sync and share service, including a transaction ledger to enable notarization and eSignature capabilities, across all platforms.
- File notarization
- Embedded eSignatures
- Independent file verification
Learn More, Earn More with Acronis Academy
Whether you and your team are seeking professional certifications or starting an MSP business, we're here to support you at every stage.

Start learning for Free
New! MSP Academy offers budding and seasoned MSP professionals vendor-neutral training covering the A-Z of managing a successful MSP business.
Train on-demand
Access our most popular sales and technical training courses designed for existing MSPs looking to enhance their cybersecurity skills and knowledge.
Login to Partner Portal
Available exclusively to Acronis Partners. Access our complete Acronis Academy training catalogue and earn your required certifications.
Looking for help?
Frequently Asked Questions
How complex is it to provision and manage services on top of Acronis DLP?
Service providers can leverage DLP to deliver data loss prevention services without adding costly security expertise headcount on their end.
Advanced DLP removes the inherent complexity of DLP solutions historically focused at enterprises, with automatic client-specific DLP policy creation achieved by learning from end users.
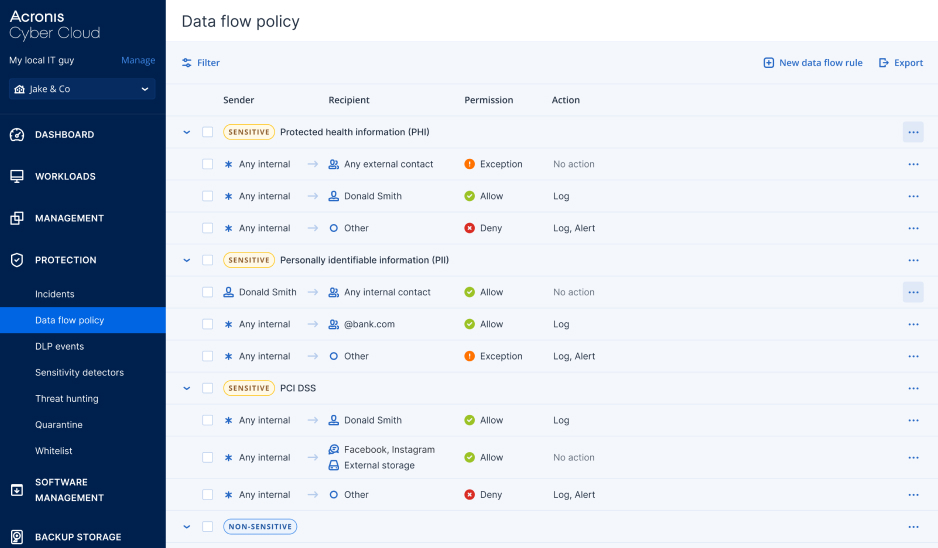
Advanced DLP also streamlines DLP service management. Once the initial DLP policy is generated automatically in an easy to understand and validate graphical format, the enforced DLP policy can be extended with additional rules to allow and protect newly observed data flows through an automated, user-assisted process.
The advanced pack is natively integrated into Acronis Cyber Protect Cloud, allowing you to centralize service management and provisioning and manage clients per tenant while integrating it with the most common RMM and PSA tools used by service providers.
The unmatched level of data loss prevention automation offered by DLP, with its MSP-centric design, makes it easy to launch a comprehensive DLP service without high costs for Acronis partners.
What types of clients could be protected with DLP?
Data loss prevention protects against leakage of sensitive data. Service providers can launch services on top of DLP oriented with clients that store regulated sensitive information such as personally identifiable information (PII), protected health information (PHI), or payment card data (PCI DSS). DLP services are also critical for clients that need to protect confidential corporate information.
Traditional industries that rely more heavily on data loss prevention are banking and finance (BFSI), healthcare, government, IT providers and telecoms, manufacturing, legal, retail and logistics.
How are services with DLP usually provisioned?
Provisioning data loss prevention services could be a complex and costly process, historically requiring additional consultation from DLP vendors. DLP, however, is specifically designed to remove this complexity and enable service providers to include a comprehensive DLP into their practice.
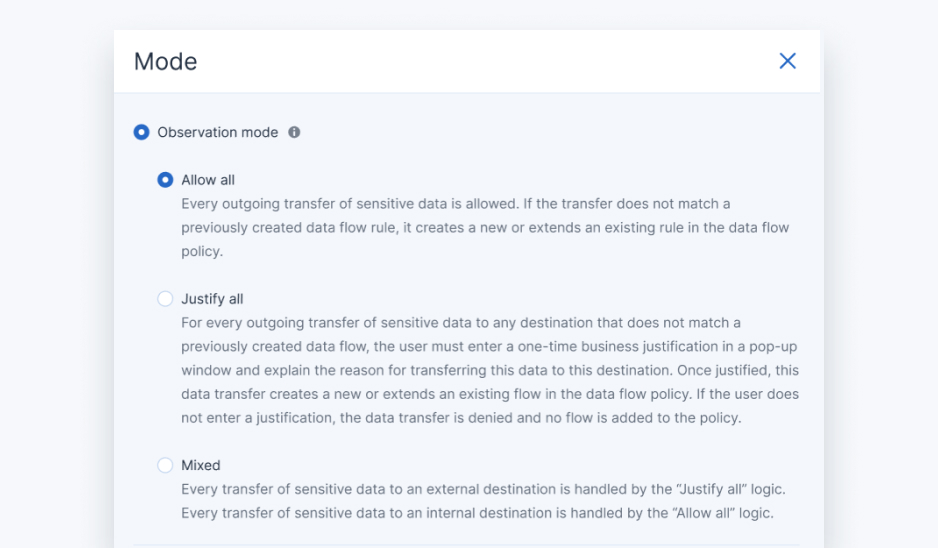
The service is provisioned to clients through the Acronis Cyber Protect Cloud agent and requires only a flick of a switch in the management console. In initial provisioning, DLP should be set in observation mode to automatically create the initial DLP policy by observing end users’ behavior and optionally requiring a one-time justification from them for newly detected data flows. The baseline data loss prevention policy creation period should take between one and two months, depending on the quantity of observed data flows during that period.
Once generated, the baseline (initial) DLP policy is presented in an easy-to-understand graphical format. It is then validated with clients, who best understand their business’ specifics and can help make the DLP rules more accurate. The validation process is extremely easy, requires no technical knowledge from clients, and is done in just a few hours.
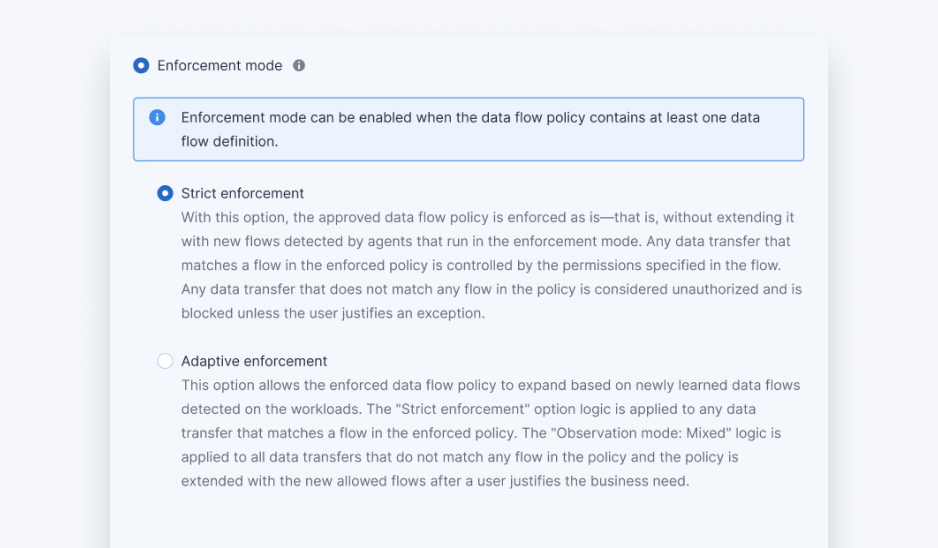
Once validated, the data loss prevention policy is enforced to allow all business-related transfers of sensitive data while blocking any sensitive data transfer that is not used in the business process. The policy can be enforced in two ways — strict enforcement or adaptive enforcement. In adaptive enforcement, you can leverage automated, user-assisted extensions of enforced policies with additional rules to allow and protect new data flows that were not observed when creating the initial DLP policy. The adaptive enforcement mode enables better business continuity, ensuring new data flows will not be blocked. The strict enforcement mode is for clients who require more strict controls, DLP will block any new data flows that do not match already approved ones in the DLP policy.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.