- The most secure backup and recoveryStrengthen business resilience with secure, immutable backup, rapid recovery and anti-ransomware technologies.
- Comprehensive security capabilityEnsure peace of mind and help to avoid costly downtime with integrated endpoint detection and response (EDR) and automated URL filtering.
- Powerful endpoint management and automationMinimize outages and boost uptime with automatic anomaly detection, proactive patching, automated scripts, and remote access for troubleshooting.
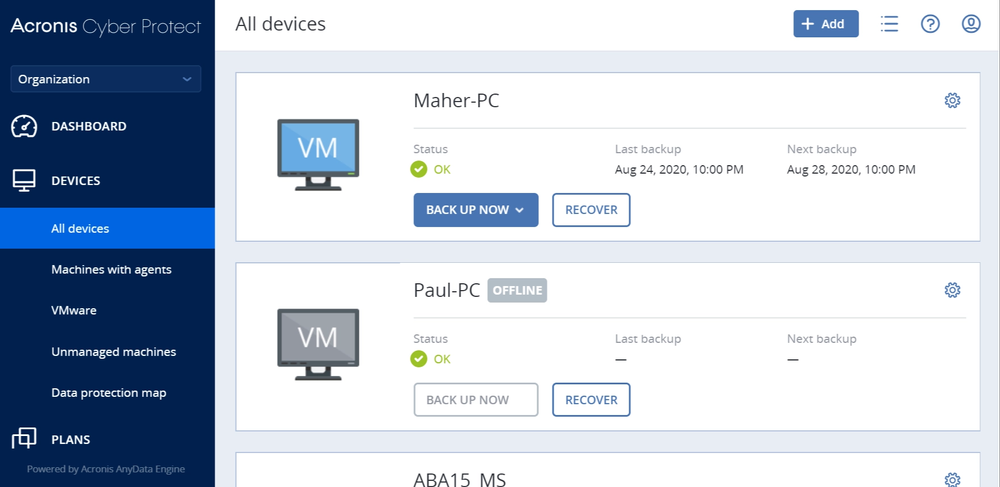
Easy, efficient and secure backup with rapid recovery
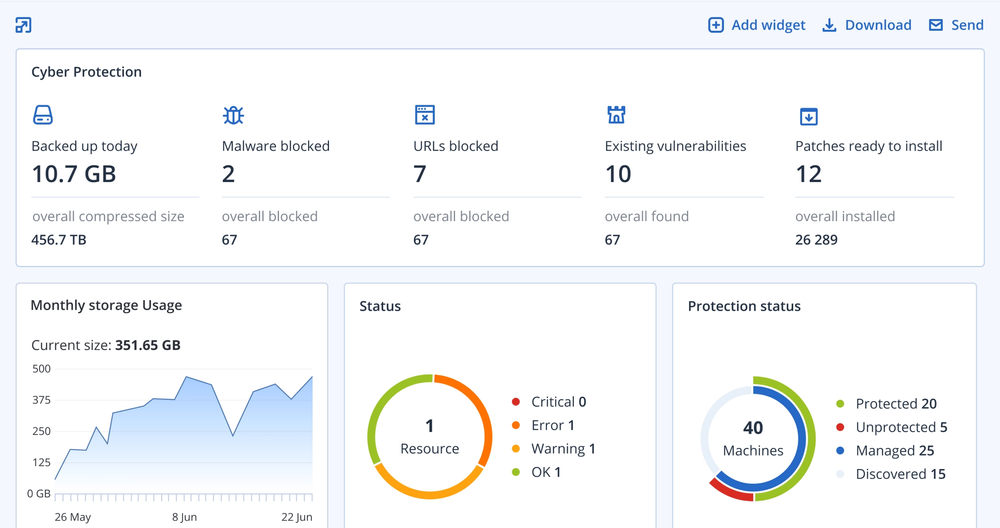
Centralized cybersecurity, backup and endpoint management
Advanced cyber protection for every endpoint in any location – making it ideal for today’s mobile and remote work environments.

- Business continuity with cloud disaster recovery
- Cloud-to-cloud Microsoft 365 backup, with unlimited cloud storage
- Proactive security augmented with endpoint detection and response
Advanced attacks can only be countered with advanced security.
- ProactiveVulnerability assessments, patch management, security posture monitoring, threat hunting, removal of malware from backups and automatic protection of new devices.
- ActiveContinuous data protection, real-time threat protection, and informed threat investigations and ML-based monitoring of workloads to detect issues before they cause downtime.
- ReactiveRapid response to security incidents and recovery of data with attack rollbacks. integrated disaster recovery and additional investigation capabilities like forensic backups and secure remote desktop access.
Acronis Cyber Protect Cloud
Get cyber protection as a managed service from an Acronis partner

See Acronis Cyber Protect in action
Explore how integrated cyber protection reduces complexity , delivers better protection against today’s cyberthreats and maximizes efficiency by saving you time and money.
Upcoming online events
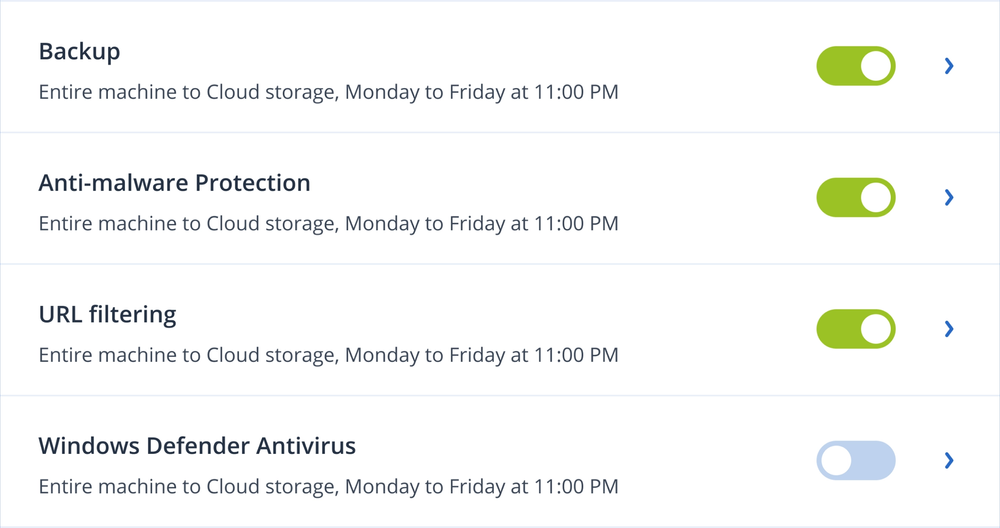
Complete protection for modern-day threats
Endpoint Detection & Response
Advanced and unknown threat detection together with informed threat investigation and response.Anti-malware and antivirus
Proactively protect your data, applications and systems from advanced cyberattacks with real-time protection, AI-enhanced behavioral heuristic antivirus, anti-malware, anti-ransomware and anti-cryptojacking technologies.Fail-safe patching
Cyber Protect automatically creates a backup before any patches are applied to ensure that its quick and easy to recover if any installed patches cause system instability.Forensic backup
Simplify future analysis, compliance reporting and investigations by collecting digital evidence – like memory dumps and process information – from disk-level backups with Forensic Mode.Defeat ransomware
Prevent reinfection via integrated anti-malware scanning and malware removal during the recovery process. Gain peace of mind with immutable backup storage.Continuous data protection
Safeguard new data as it’s created. Acronis’ agent monitors every change made in the listed applications and continuously backs them up so recent changes aren’t lost if the machine needs to be reimaged.Global threat monitoring and smart alerts
Benefit from the global network of Acronis Cyber Protection Operation Centers (CPOC) by receiving real-time alerts on malware, vulnerabilities, natural disasters and other global events that may affect data protection.Data compliance reporting and data protection map
Ensure compliance reporting by getting detailed information about stored data and use automatic data classification to track the protection status of important files.AI-powered Cyber Scripting
Automate IT tasks with precision using AI-driven scripts. Improve efficiency and reduce errors while streamlining endpoint management across all devices.ML-based monitoring
Boost technician efficiency with predictive monitoring. Reduce downtime using ML anomaly detection. Prioritize and reduce alerts for faster issue resolution.Remote desktop
Use one application for seamless access and support for Windows, macOS and Linux machines using highly secure NEAR proprietary protocol.HW and SW inventory
Keep up-to-date information on hardware and software assets to properly plan replacement and to plan and track updates.
Industry-proven protection













- 100% detection rateIn AV-Test certification under macOS, Acronis detected 100% of malware and had zero false positives.
- 0% false positivesIn the AV-Comparatives test, Acronis was one of only four solutions with zero false-positives.
- 100% high performanceIn all eight performance categories for AV-TEST, Acronis demonstrated either a Very Fast or Fast performance rating.
Acronis Cyber Protect
Protect your entire business against data loss and downtime with comprehensive cybersecurity plus fast, secure backup and disaster recovery in one integrated, easy-to-manage package.
Select the workloads you want to protect
Cloud storage
Subscription period
Start by selecting workloads
0
Protect more workloads on more platforms
Physical
Applications
- Microsoft Exchange
- Microsoft SQL Server
- Microsoft SharePoint
- Microsoft Active Directory
- Oracle Database
Virtual
- VMware vSphere
- Microsoft Hyper-V
- Citrix XenServer
- Red Hat Virtualization
- Linux KVM
- Oracle VM Server
Endpoints
- Windows PC
- Mac

Looking for help?
Frequently Asked Questions
Is Acronis Cyber Protect any good?
Acronis Cyber Protect is a comprehensive cyber protection solution that combines backup and data protection features with advanced cybersecurity capabilities. It's designed to provide businesses with a single solution that protects different types of workloads from a wide range of cyber threats. Thanks to this comprehensive approach which delivers complete protection from a single platform, it has been considered the go to all in one solution for all types of businesses.
How many licenses do I need for my environment?
A license is required for every machine or physical host that you want to backup. In the case when the product is used on a cluster, each node of the cluster must be licensed.What is the difference between Standard and Advanced editions?
Acronis Cyber Protect Advanced offers a number of advanced features and benefits in comparison with the Standard Edition, such as centralized management of backup plans, backup to tapes, SAN storage snapshots, Acronis Notary, Acronis ASign and other.
In case of agent installation inside VM and agent-based backup, the following rules apply:
- Advanced license is required under the following hypervisors: XenServer, KVM, RHV, Oracle VM Server
- Standard license can be used under VMware vSphere, Microsoft Hyper-V, Virtuozzo.
Please refer to this article for the full comparative table of the options.
What is the difference between on-premises and cloud deployment?
Cloud deployment means that the management server is located in one of the Acronis data centers. The benefit of this approach is that you do not need to maintain the management server in your local network. This type of deployment is available only for subscription licenses and at the moment does not include some features of the Advanced edition. This type of deployment is recommended if you have a Mac-only environment or a single Mac to back up (since Management Server cannot be installed on a Mac).
On-premises deployment means that all of the product components are installed in your local network. You have to use this method if your machines are not connected to the Internet.
You can find more detailed information here.
What is Acronis Cloud Storage and how is it licensed?
Acronis Cloud Storage is a storage option that saves backups to safe and secure Acronis Data Centers. Acronis Cloud Storage licenses are subscription-based and depend on the storage capacity levels. You can save backups from an unlimited number of machines and any type of platform to cloud storage, including mobile device backups. The quota is shared among all the devices registered in the account*.
(!) Note that in order to use Acronis Cloud Storage you need at least one Acronis Cyber Protect license.
*Does not apply to the free cloud storage. The free cloud storage available with a subscription license is valid only for the licensed workload and cannot be shared across other workloads.
Sorry, your browser is not supported.
It seems that our new website is incompatible with your current browser's version. Don’t worry, this is easily fixed! To view our complete website, simply update your browser now or continue anyway.